
It is widely held that the Romans successfully built their own novice navy into a formidable fighting force after capturing and “reverse-engineering” a Carthaginian warship that had run aground. This would be not only yet another example of how “chance favors the prepared mind”, but also of how easily “intelligence” secrets can get away from you. And in the hacking world, there is no such thing as too much information.
OK…so what do I do now?
In phase one of the hacking process you did some footprinting work and came up with tons of information. Some of it was harmless and some of it is so bizarre that you’re not even sure what it is, more less what to do with it. I get that. So welcome to the stage where you learn what to do with all of those targets that you identified during your reconnaissance efforts.
Regardless of the type of system you are testing, you’re going to have to do some scanning and enumeration before you start the exploitation and increase the depth of your penetration testing. Scanning is the process of discovering systems on the network and taking a look at what open ports and applications may be running. When it comes to scanning there are 3 major types. These three types also include a set of 4 steps that make up a basic scanning methodology. The 3 types are network scanning, port scanning, and vulnerability scanning. The 4 steps that make up the methodology are:
- Identify live systems
- Discover open ports
- Identify the OS and services
- Scan for vulnerabilities
The more you sweat in times of peace, the less you bleed in times of war…

While footprinting provides us with a high-level view of our target, scanning is the next step along our path. Scanning is akin to knocking on virtual doors to see who’s at the crib and how they are hanging out. Although we intend to go inside and have a look around, at this point we’re still casing the joint. It’s like we’re just rolling around the neighborhood scoping out the scene.
So what is this enumeration, then, you ask? Well, if ports are synonymous to doors and port scanning is like knocking on them or tugging at the knob checking to see if they are open then enumeration is like standing on the porch talking with the neighbor. While it was all good knowing which ports were open, we now want to see if we can find some low-hanging fruit around. Things like open shares and user account information. At this point it’s worth being mindful of the fact that lions on the hunt don’t spend their time chasing after prey with strong defenses. They go after targets they know they can take down with little effort and time. Let this be your guide and it will serve you well in your quest. Don’t worry about trying to obtain the glory of being known as the world’s greatest hacker. Tomorrow there will always be someone greater than thou. Forget that and stay focused. In for a sip, in for a sea!
Let’s go over some examples that we can safely try out. I’ll be performing my scans running Nmap in an old-school distribution of the infamous Backtrack penetration suite. Nmap is short for Network Mapper. It is by far the most widely used scanning and enumeration tool on the planet. In subsequent post I’ll take you on a ride through a full-scale pen test within a lab environment. For now, we’ll perform a few basic examples on our home network. (Nmap is free by the way. If you’re running Windows and you want to follow along with the example, there’s a graphical version that you can download called Zenmap.)
I’ll be using 192.168.1.0 /24 as a subnet since it’s the most common private address range in use on most home networks. We’ll start by running a ping sweep with nmap using the “sP” and “v” options. sP provides the ping and v sets it to verbose mode. The command you’ll run looks like this: nmap -sP -v 192.168.1.0/24.
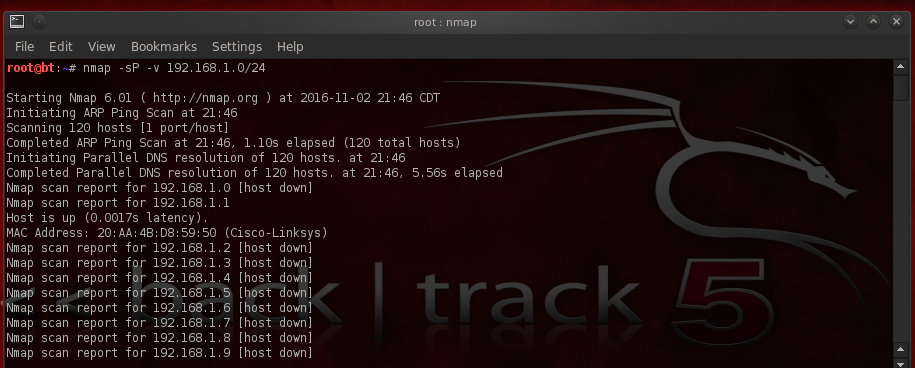

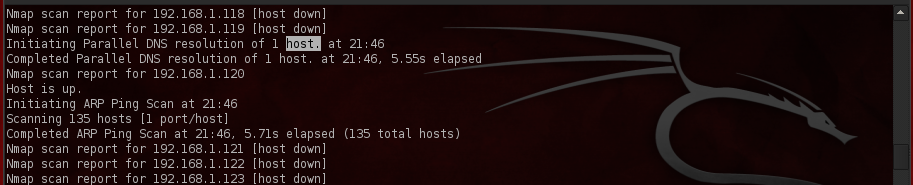

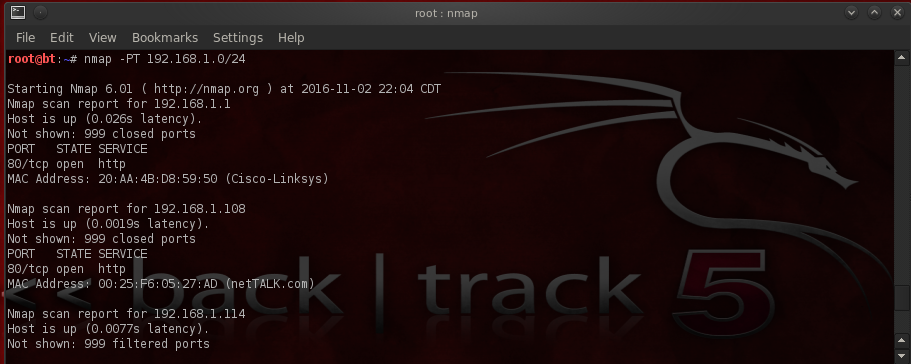
Next, to ensure that we hit every device- because some may be blocking ICMP requests- we’ll try a TCP sweep. The command you’ll need to run is: nmap -PT 192.168.1.0/24


Finally, let’s try and fingerprint an operating system on the host. The command you’ll use for this one is: nmap -sS -O 192.168.1.116 (“116” is used here as an example.)
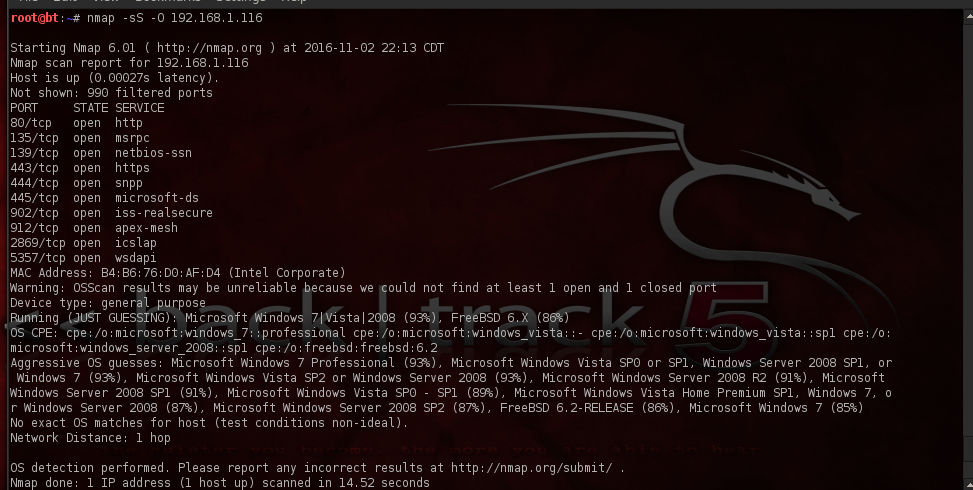
Wow! Pretty interesting stuff there, right? While my intention was not to give you a lesson on using nmap, I was however aiming to show you how port scanning your target identifies which ports are open, and gives you more information in building your attack vectors. Remember, good hackers will spend 90 to 95 percent of their time gathering information for an attack, and after scanning comes enumeration. Enumeration in the hacking world is listing off the items we find within a specific target. When we enumerate a target, we’re moving from passive information-gathering to a much more active state.
Mysteries call out to be understood. Every lock longs for a key, every empty cup thirst for wine.
Hack On, Gents!

