Passive & Active Recon – Part 2
27
June, 2022
Days 26 – 29
Passive & Active Recon: Part 2
100 Days of Hacking
This post will be brief and will make up Part 2 of Passive and Active Recon. We are still grinding along HTB’s Bug Bounty Job Role Path, Information Gathering- Web Edition. Specifically, this post will cover finding Virtual Hosts and finally, we’ll tackle the questions from the accompanying assessment.
Day 26 – 27
Virtual Hosts
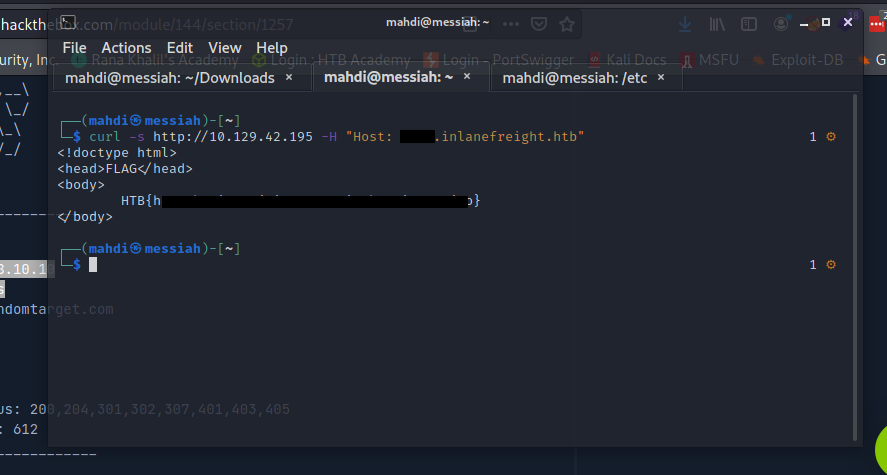
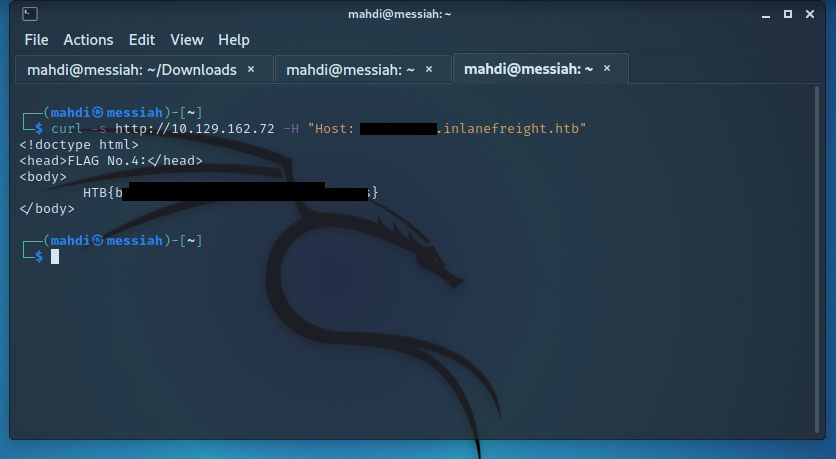
Enumerate the target and find a vHost that contains flag No. 1. Submit the flag value as your answer (in the format HTB{DATA}).
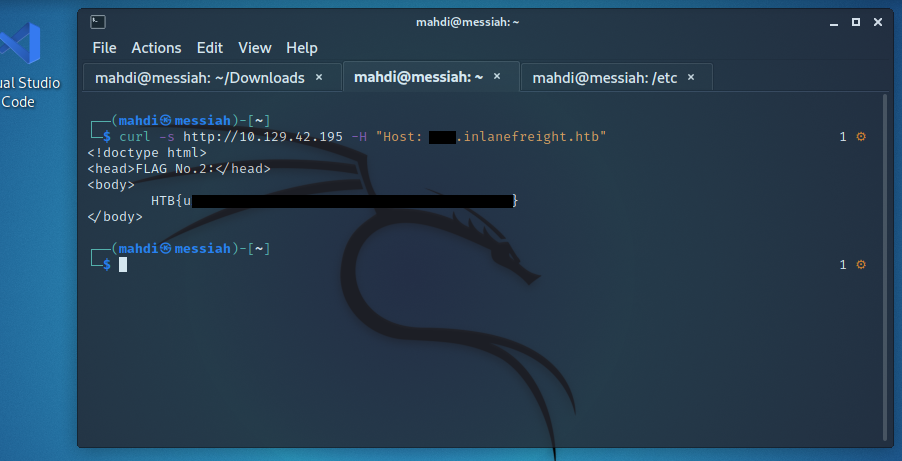
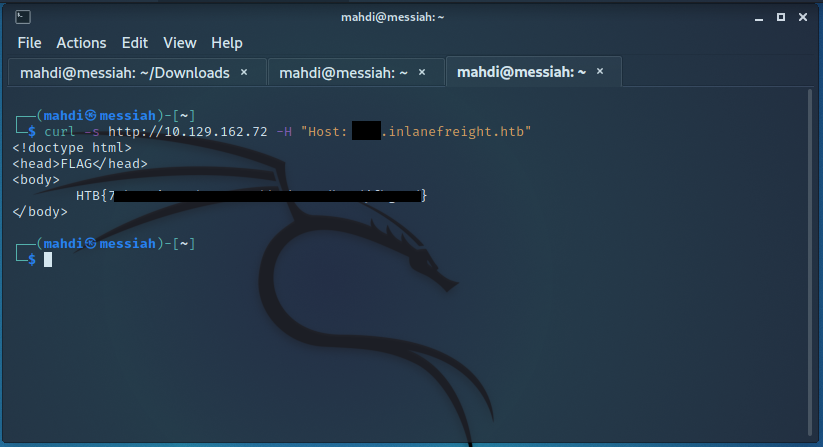
Enumerate the target and find a vHost that contains flag No. 2. Submit the flag value as your answer (in the format HTB{DATA}).
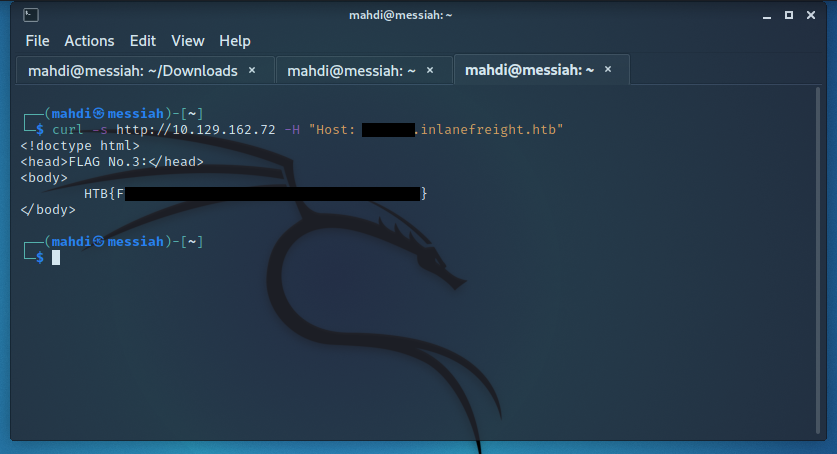
Enumerate the target and find a vHost that contains flag No. 3. Submit the flag value as your answer (in the format HTB{DATA}).
Enumerate the target and find a vHost that contains flag No. 4. Submit the flag value as your answer (in the format HTB{DATA}).
Day 28 – Day 29
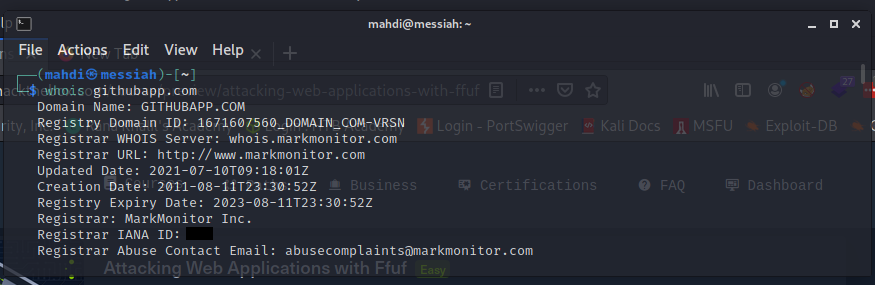
What is the registrar IANA ID number for the githubapp.com domain?
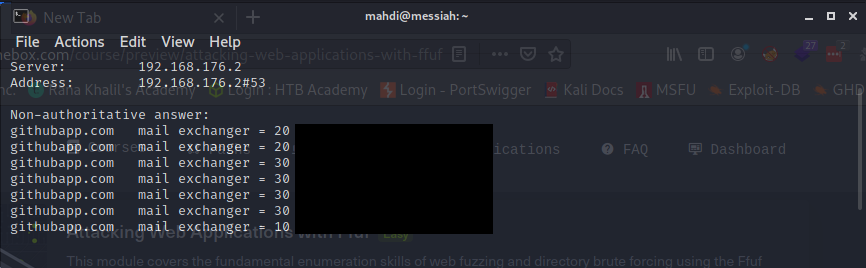
What is the last mailserver returned when querying the MX records for githubapp.com?
Summary
In this two part post series we looked at various techniques for passive and active information gathering from domains and web servers. We will be able to use what we’ve learned on real world penetration test and even bug bounty programs if we chose that route. What’s most important is our understanding of the difference between the two types of Recon.
Here’s what we covered:
- WHOIS
- DNS
- (Sub)Domain Enumeration
- Infrastructure Identification
- Virtual Host Enumeration
- Crawling
Next up we’ll be looking at attacking web applications with FFUF. Until then, Hack On, Ladz and Gentz!
Develop intuitive judgement and understanding for everything…Perceive those things which cannot be seen…Pay attention even to trifles.” – Miyamoto Musashi