
Brick by brick the patient thief carries away the rich man’s house in a single night
Thus far we’ve covered a lot of stuff that, admittedly, may not have seemed fun nor sexy. In the initial learning stages of getting to know your target, any of it rarely is. But trust me, in the broad scheme of things, it’s necessary.
You’ll often times hear me make the analogy of learning how to hack to learning a martial art. The overall learning process of the two disciplines are very much alike. Think back to the movie The Karate Kid. Daniel-San shows up at Mr. Miyagi’s crib all psyched up to learn the secret art of karate and what happened? For what I’m sure seemed like an eternity to Daniel-San, all Miyagi had him doing was chores that were filled with tons of tedious, boring, and repetitive actions. This went on so long to where eventually Daniel-San was like, “Screw this, I’m out!” At which point Miyagi stopped him and demonstrated the method behind what was perceived as his madness. As it turned out, the time that was spent doing things that didn’t seem so important ended up being the very fundamentals that were needed for Daniel-San to be successful at his craft.
If you’re a regular visitor to this site then you’ve undoubtedly heard me say over and over that I would be demonstrating the techniques that I’ve posted about in the form of an actual pen test. Forgive me if I’ve come off like Kesuke Miyagi. I applaud you for your impeccable patience. It is with great pleasure that I now present to you these four words, “Wax on, wax off!” 🙂 If you haven’t been following any of the preceding post, I would strongly suggest you go back and wax the cars in the previous post- you’re going to need it moving forward.
The patience of sand overtakes all things
We obviously won’t be conducting this exercise against a real world target. Nonetheless, our target is conducive for our purpose. Coming into this exercise, the only information we have on our target are the following four IP addresses:
- 10.5.0.1
- 10.5.0.254
- 10.5.1.254
- 10.5.1.10
So, reflecting on some of the techniques we’ve covered up to this point, we know that the logical thing for us to do is run a ping sweep to see what systems are live on the network and to see if maybe we can identify any other systems that could be hanging around. For a quick review see here.
Note that the * in the scan syntax means the same thing as does /24. We conduct our sweep and nmap tells us that 4 host are up.
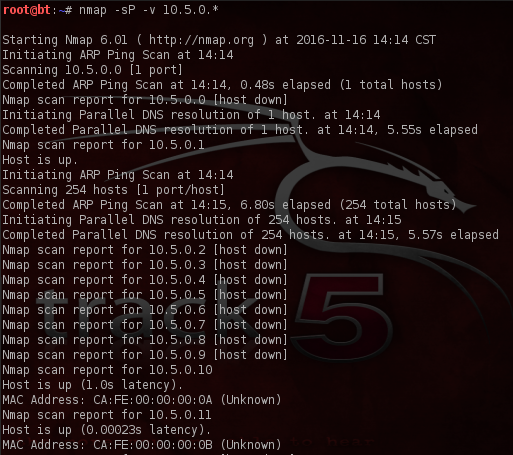
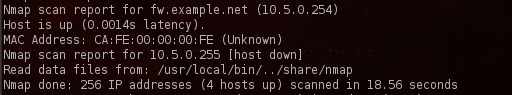
And for good measures, ensuring that we hit every device, we’ll also do a TCP sweep using the -PT flag.
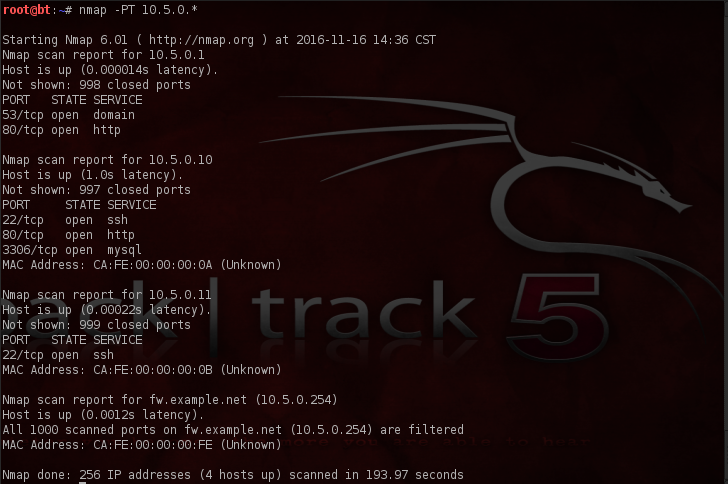
Although we didn’t detect any new hosts, we now have a much nicer and cleaner output that also contains more revealing information.
Each thought of man is but a single grain of sand. Yet a single grain of sand can ruin the best of bowman’s aim, a single grain of sand in the eye can turn the greatest of war-beasts from its task!
So what do we have thus far? We’ve gained 2 additional IP addresses and we now know what ports are open on the identified hosts. Very valuable information.
Continuing on, let’s repeat the previous steps for our other subnet and also we’ll do an OS scan on both of the subnets as well. (The following screenshots reflect our combined efforts respectively).
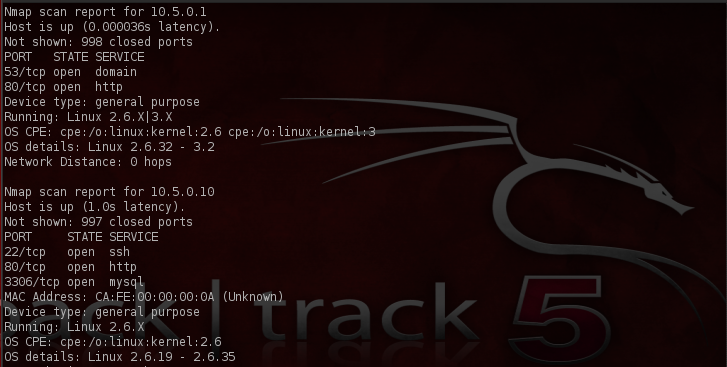
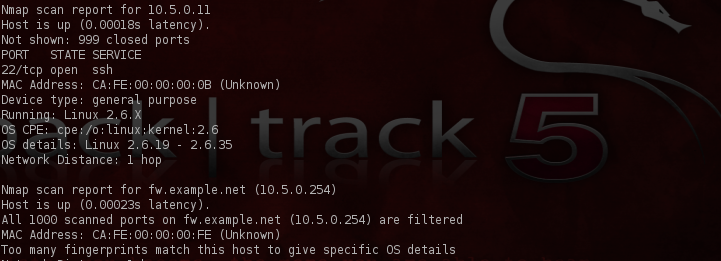
And once again for our 10.5.1* subnet…
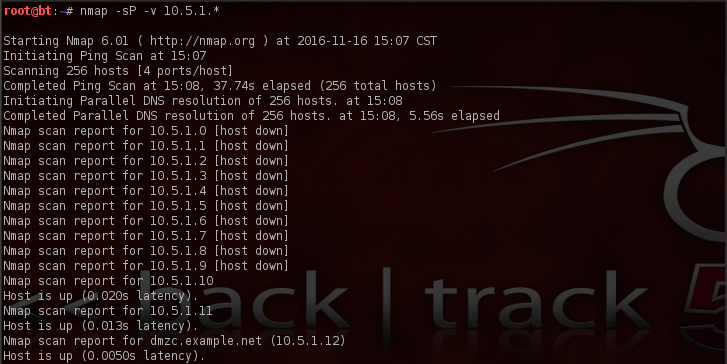
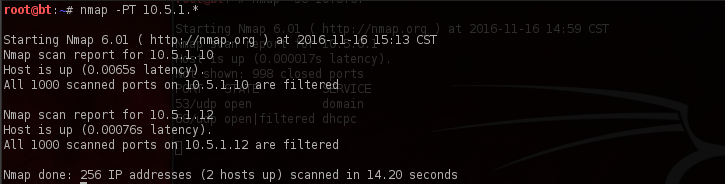
Here it’s important to note that a return of “filtered” like in the output above indicates the system is protected by a firewall.
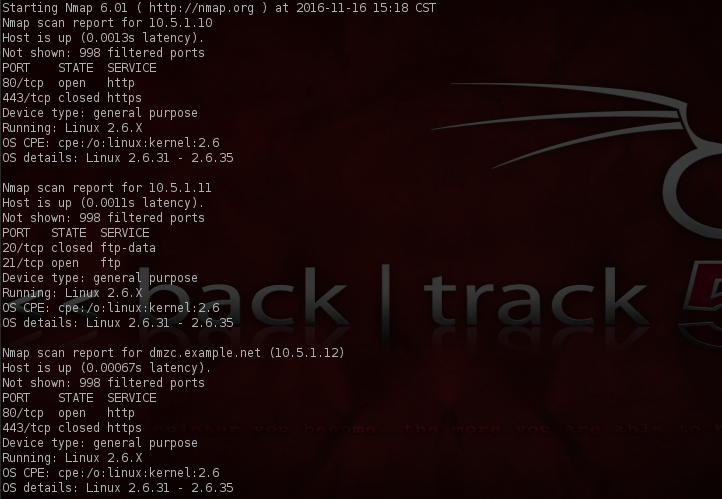
Fabulous. Not only did we come away with two more discovered host, we also came away with a wealth of useful information in regards to what services are running and what ports are opened and closed on these hosts. Now, there’s something else that we’ll want to do before moving any further with our test. Let’s see if perhaps these IP address respond to any DNS names. For our purposes here, we’ll rely on the assistance of nslookup. (nslookup is an application that is used to query name servers for IP addresses of a specified domain or host on a domain. You can also use it to query name servers for the DNS host name of a supplied IP address.)
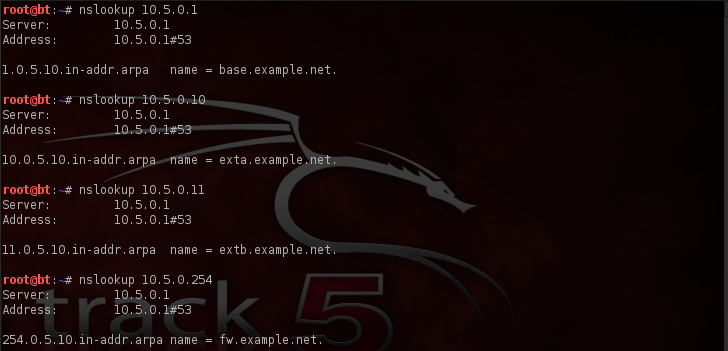
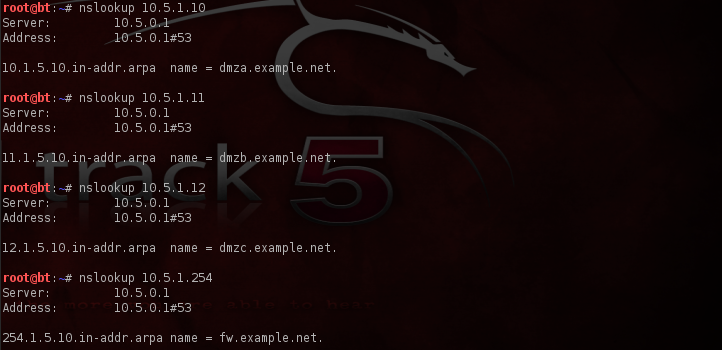
And just to be on the safe side, I went ahead and scanned for host on the subnet above 10.5.1*, following the line of reasoning that if there was something on .o and .1 there may very well be something on .2. Amazingly, I was not disappointed. Sometimes it pays to go out on a hunch as such.
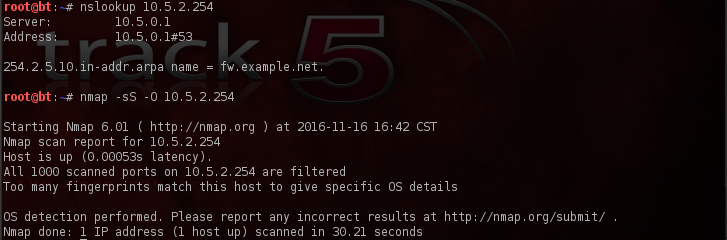
Finally, with the information that we’ve managed to stack up on our target we should be able to put together a nice looking network diagram detailing what our target’s network potentially looks like. If nothing else, we’re armed with a substantial amount more information to proceed with than we had coming into our engagement. Armed with such information we can move confidently into our next phase of testing.
Until next time, Hack On, gents!


