5
November, 2017
Ever been fascinated by the thought,
“what if there was a way that I could just search the inter-net and see all the different interconnected devices?”
Afterall, isn’t our world nothing more than a seemingly infinite number of human beings who inter-be? That being the case, there’s bound to be an almost equal amount of devices that inter-are. It would be nice to just, see them. There’s a search engine for that!
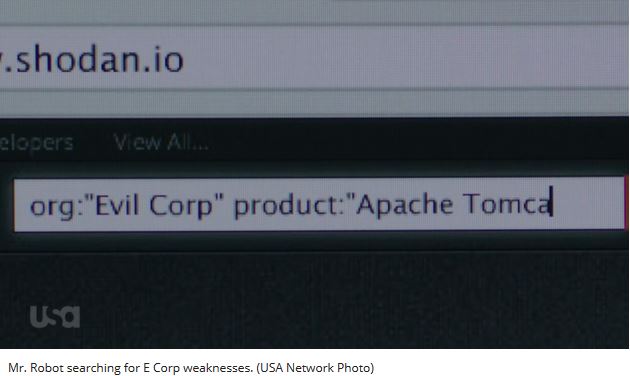
Seriously, there’s a search engine for that. Not only does such an engine exist, but even Mr. freaking Robot himself uses it. How’s that for cred? 🙂 I’m kidding. But for those who are not in the know, I’m going to briefly turn you on to a tool called Shodan.
Shodan, b.k.a “a Hacker’s Google”, is a search engine for interconnected devices on the internet. And before you even ask, the answer to your question is yes! Yes this means that if you have a system on your network that is being publicly displayed, there’s a 100% chance that Hacker X and the gang will come along and ya know, check things out. And yes, this also means that you as a security tester can use this tool to identify rougue devices that Hacker X and the gang have installed as a result of the above activities. (Snarls- Gosh darn kids.)
It is illegal to access or manipulate systems that you do not have express permission to do so.
Shodan can run right from your web browser without the need to install anything on your system. Some handy features available with the tool are:
Shodan Exploits– a database to help you learn about existing vulnerablities and how to exploit them.
Shodan Maps– provides a beautiful gui that displays your returns on a global map.
Shodan ISC Radar– shows a worldwide display of directly accessible Industrial Control Systems on the web.
Simple enough, right? Granted, there are more advanced ways to interfce with Shodan. One of those ways is the Shodan CLI.
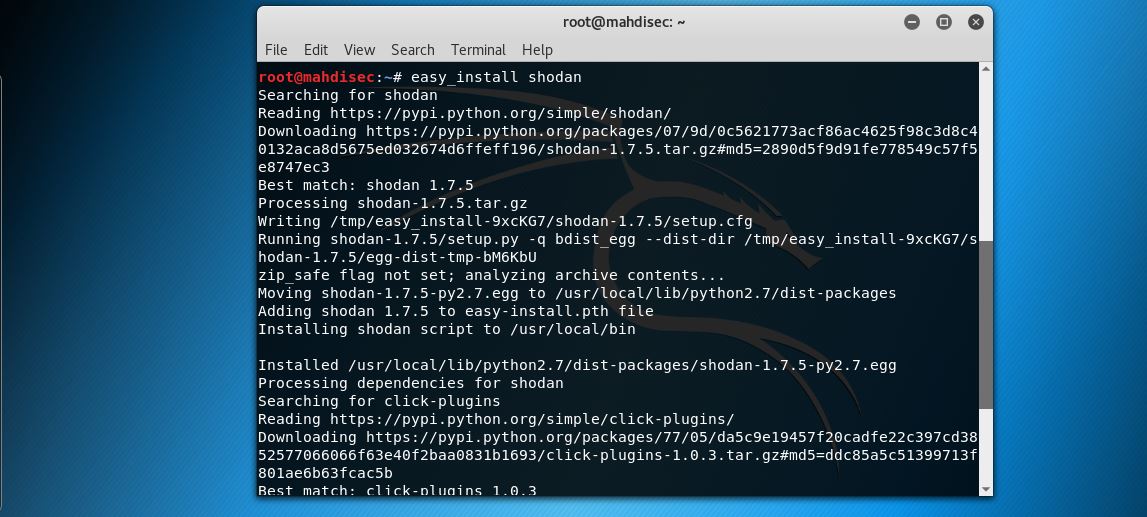
Since the Shodan CLI isn’t installed in Kali by default you’ll need to install it and initialize the program with your API key.

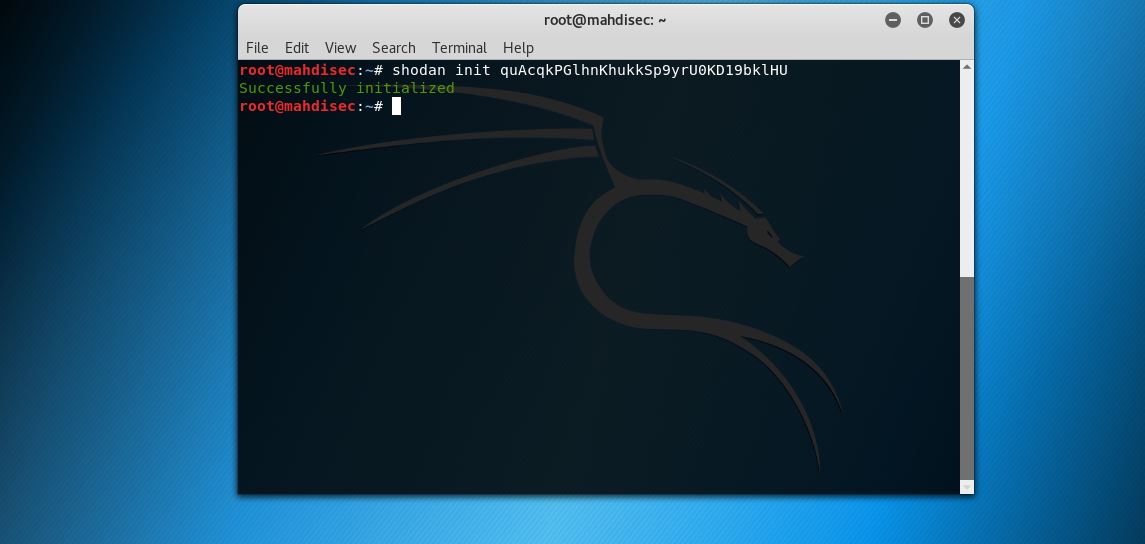
Now you are ready to use Shodan directly from your command prompt. Type “shodan -h” to see the help menu. Using shodan in this manner, not only will Shodan return location information about your target, and the number of open ports, but it will also show you if the system that you search has a known vulnerability. If a vulnerablility is found, Shodan will issue the CVE number for it.
In conclusion, if you’re looking for a quick and easy way to find a companies exposed systems online that are outdated, open, or not properly secured, Shodan is the tool that you’ll want to use.
In parting, Shodan is definitely a recon tool that you’ll want to get to know and keep in your arsenal if you need to gather information on devices that are online. But what about devices and sites behind those devices that are “seemingly” off of the radar? Ya know, like, on the Dark Web? Fortunately, there’s now, you guessed it….a search engine for that! It’s called Ichidan.
Hack On, Gents.