Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
Since this post is going to serve as another “Poetic Proof-Of-Concept” of us finishing another assessment along the HTB Bug Bounty Job Role Path, (links will be at the end of the post), there will not be a detailed walk through. This of course is done so as not to spoil anyone’s learning experience.
What this will be however, is our experience with the Web Attacks module recapped poetically along with screenshots of us completing the Skills Assessment that goes along with the module.
Objective: The skills assessment ask us to put ourselves in the role of a security professional who’s been hired to perform a web app penetration test for a software company. The company wants us to test the latest build of their social networking web application.
A Poetic Reflection Of XXE Injection

He woke up
kind of feeling
like
he’d been
through Hell
and back
But that quickly
went away once
he got into web attacks.
It’s through scribing
in his journal
that
he’d live
to tell the facts,
But this one’s
for the scratch
So he feels
like his head
is cracked.
“Go in
and gain their
trust,
make ’em’ think that
that you won’t crack,”
Before
the crew
went black
He’s job
was to
dispel the hack.
Can he
dupe it?
Hit the Dark Web
to get a Root Kit,
Searching for a shell
so he can
try and execute it.
Now he’s
stirring at a blinking
cursor,
looking stupid,
The tool
ain’t gonna help him
cause he don’t
know how to use it.
Exactly
like the data
cause he don’t know
what to do with it,
It’s not gone matter,
But see,
That’s where we confuse it.
Imagine that
a web app
accepts X-M-L input
But doesn’t
place restrictions
on the values
that we can put.
Or validate the input,
Nor handle the exceptions….
Most likely
what we’re looking at’s
an
XXE Injection!
Vulnerabilities
are not always
straightforward to exploit,
And all the ones that are
they can be found
with Metasploit.
So some formats
won’t be readable
through basic X-X-E,
And if you think
your payload
is repeatable
Let’s see.
Since the web app
may not show us
any values through reflection,
we cannot
see the output
like we did
in other sections.
No denying….
that we must hide
our variables
with filters,
En-code our files
like Jesus did
in parables
through scriptures.
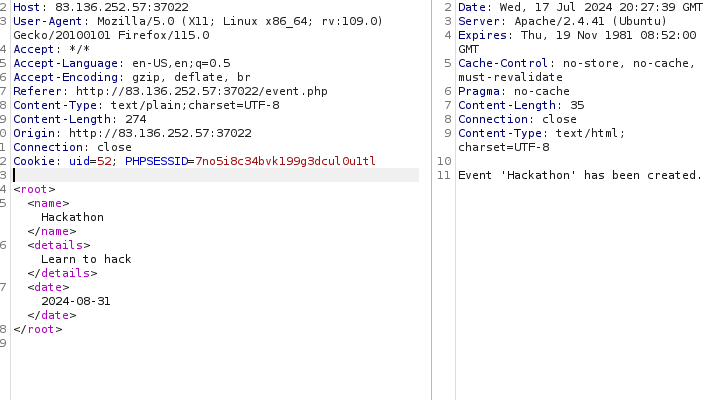
If an app
displays an error
but don’t handle
the exception,
Then we can circumvent
this flaw
and use it
as our weapon.
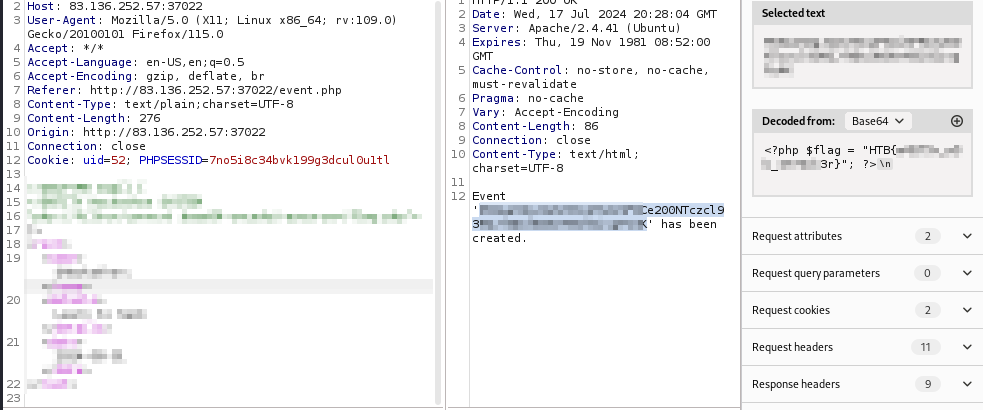
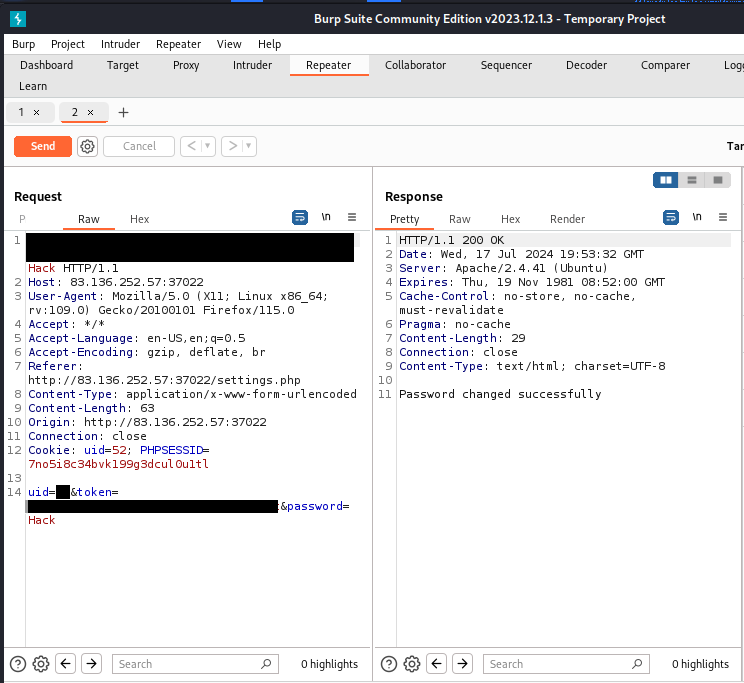
Send some
badly formed data,
if we produce
an error,
This may reveal
the web directory
and
cause some terror.
So let’s host
a D-T-D file
on a server
that we own,
And try to
read the content
of a file
that can’t be cloned.
Get this bounty,
then we will
still be dancing
while it’s over,
Cause this was
all made possible
through Ad-Vance File Disclosure.


