Grey Hat Developer
In a space that’s on constant alert for a nasty ransomware attack, the ninja looks past the hardened network perimeter and the client system, and walks straight through the open door- the web browser.
Actually, there’s an open door that’s far more literal here. The ninja or ninja’s are walking straight through the open doors of our offices, our internet cafe’s, and all those coffee shops that house our favorite hot spots.
Today I’d like to introduce you to Dan. Dan works in the accounting department of Company X. Good guy. Nice, friendly, and helpful. In fact, so much so that anyone who has ever been into his office knows that he just loves to stay tuned in to his Facebook News Feed while working. (Because we all don’t know anyone who does this.)
BeEF- The Browser Exploitation Framework
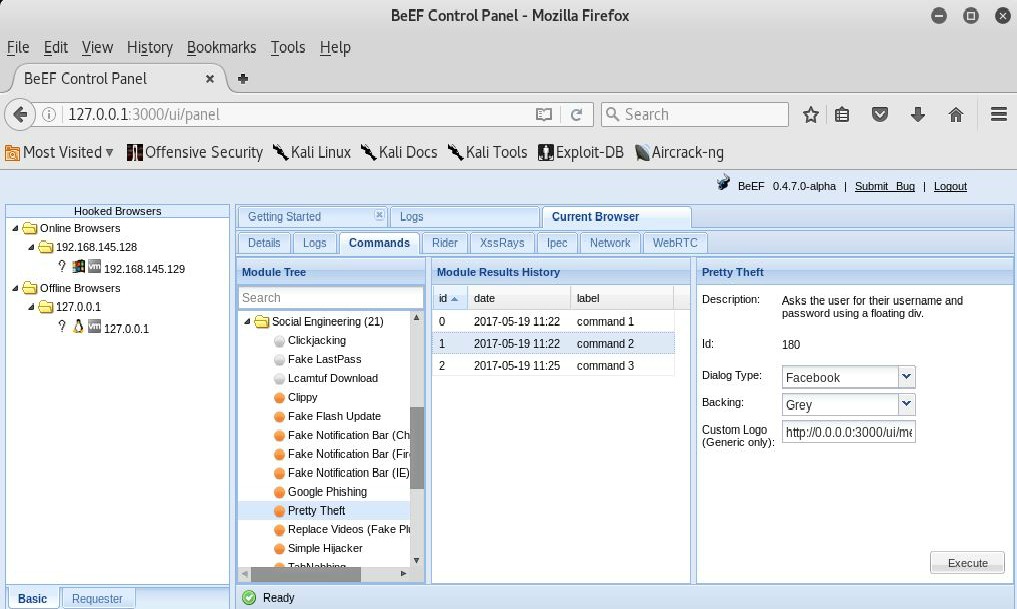
Petty Theft Module
Then there’s Dave. Dave also works at Company X and, knowing Dan like everyone else does, decides “for whatever reason” that Dan would make a perfect target to use the Facebook ruse included in the Dialog Type within the BeEF’s Petty Theft Module on. He was clever enough to trick Dan into visiting the web page that contains the browser hook.
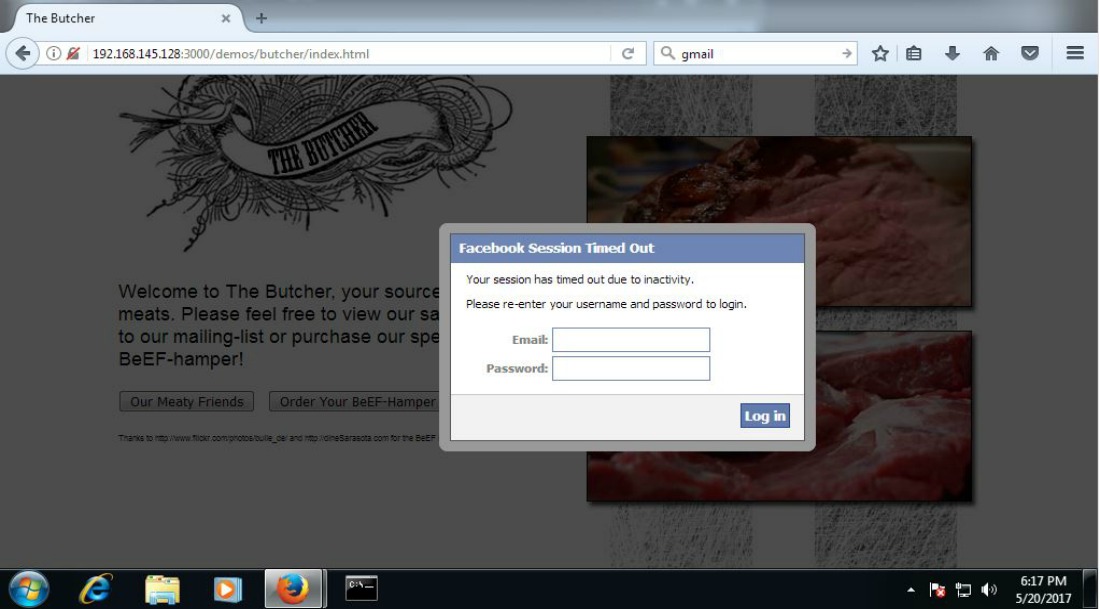
Dan, realising that he’s been logged out of his Facebook account, enters his credentials to get logged back in. BAM! Just like taking candy from a baby, right?
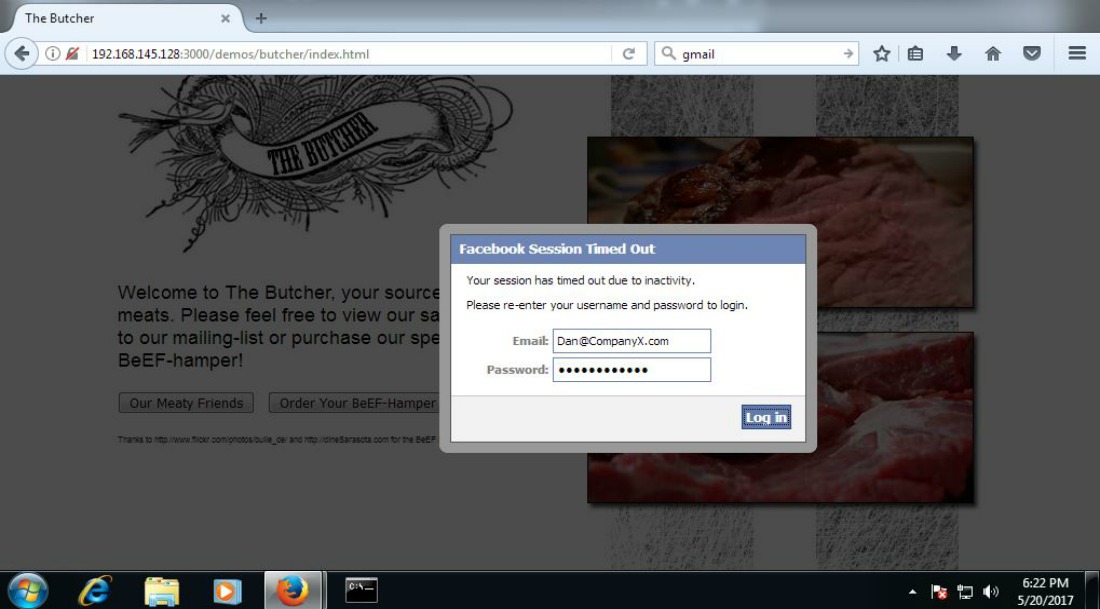
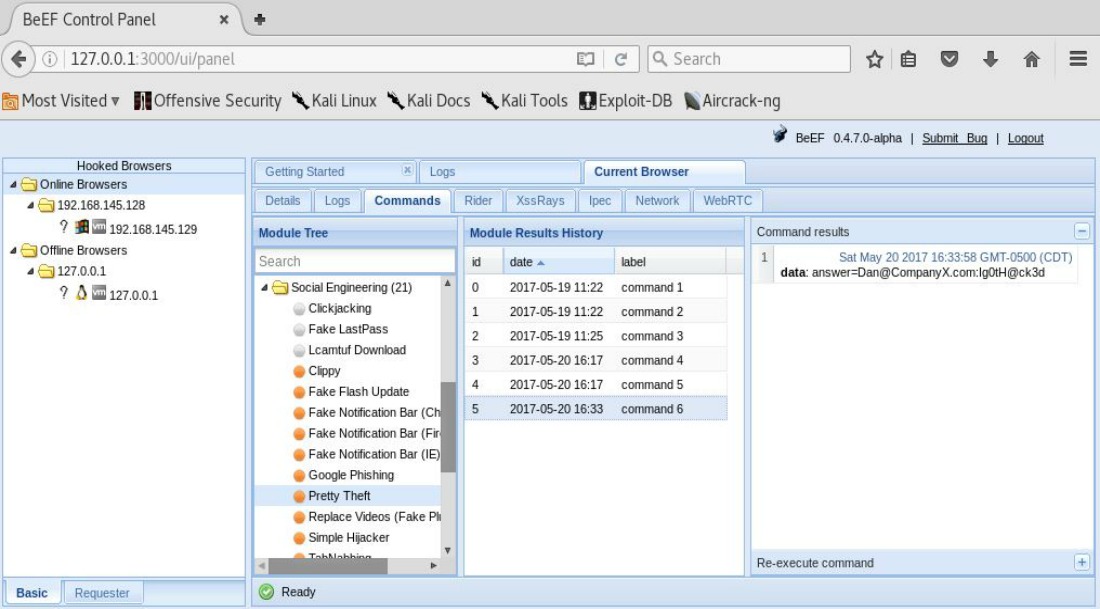
Notice the user’s name and password has been captured and is now listed in the Command results pane.
Dave on the other hand, now has Dan’s password to his Facebook account and more than likely is moving to the next phase of his attack. Depending on what information Dan stores in his Facebook account and whether or not he uses the same password for multiple accounts, the severity of this type of account has the potential to get real ugly pretty fast.
Now I can already hear the security minded one’s among us who are pointing out that all the user needs to do is have awareness of the url in the address bar. Also, the good developers who work hard to bring us Chrome and Firefox at least tip the user that something is terribly not right while entering their credentials into the dialog box of a website that doesn’t implement https. Yes. That’s correct. But I’d just like to point out that a cleverly crafted social engineering attack takes all this into account before launching it. A sense of urgency has a way of making us completely ignore warning signs that are clearly visible at the time of action.
So maybe Dave wasn’t able to dupe Dan in accounting due to the “warning signs” being heeded. Good for Dan. But what about Bob in the IT department who gets up to grab another cup of Java and comes back to his computer to find the following dialog box on his screen? Of course, this all after being socially engineered out of the break room and back to his computer with a sense of urgency scheme.
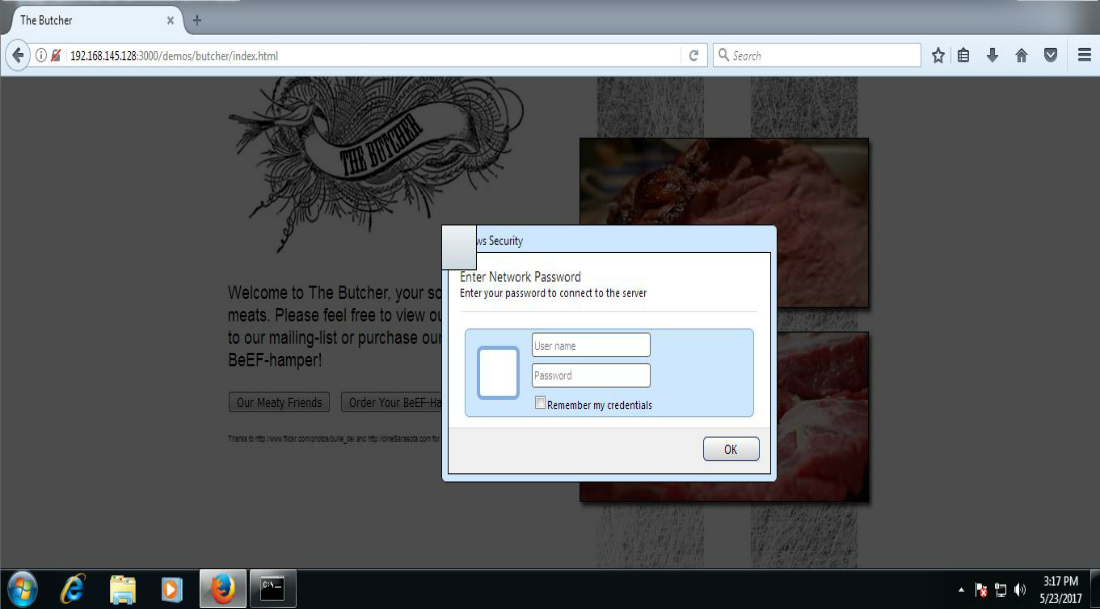
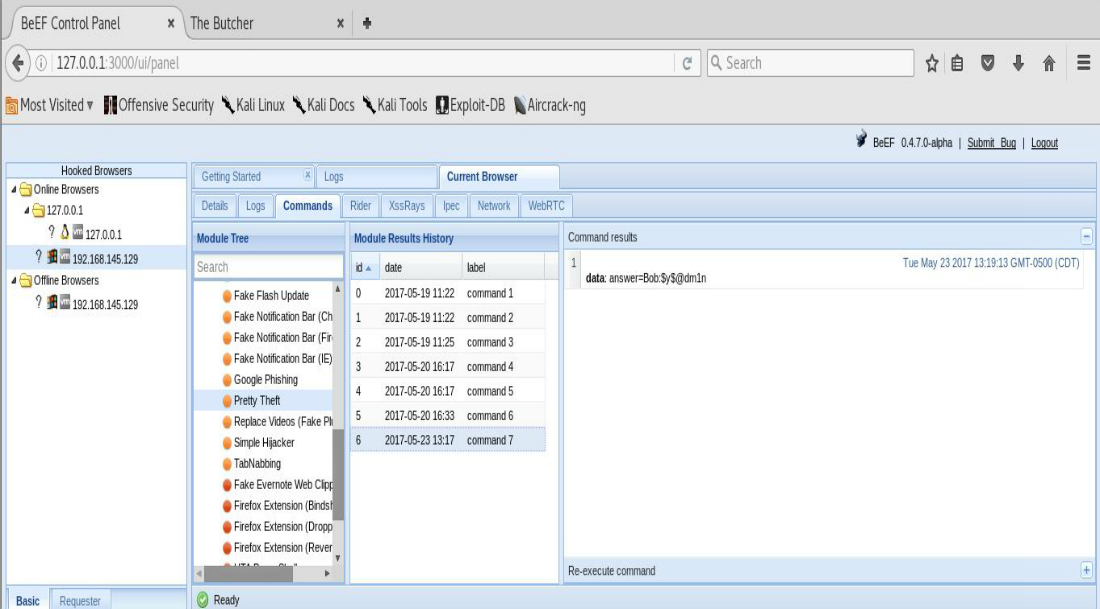
The takeaway. Educate users to the dangers’of “surfing” the web via company resources in and outside of work hours. Technically, there are script blockers available that can be used to help in thrawting these types of attacks. The success of the attack ultimately depends on the browser’s capability to be hooked. Finally, remember that cyber-security is an action verb as well as a noun. What I mean by this is that your cyber-security posture should never be “static”. You should take an active stance in ensuring the protection of your assets and resources.
And just in case you’re wondering, yes it is entirely possible to walk into the front door with a tool such as BeEF running undetected on a mobile device.
As always, you’re awesome for reading this. Please share with the world. Everyone wants to be safe, noone likes to be vulnerable. If you need help developing an active cyber-security stance don’t hesitate to contact us via email. We’re always ready to help. Hack On, gents!



