Intercepting Web Requests Part 2:
Web Proxies
12
June, 2022
Days 12-20
Web Proxies
100 Days of Hacking
Ultimately we’ll be looking into Web Proxies as the main focus of this post. But first we’ll look at Encoding/Decoding, Web & Zap Fuzzer, and Zap Scanner. To accomplish these tasks we again will make use of Burp and OWASP Zap.
Encoding/Decoding
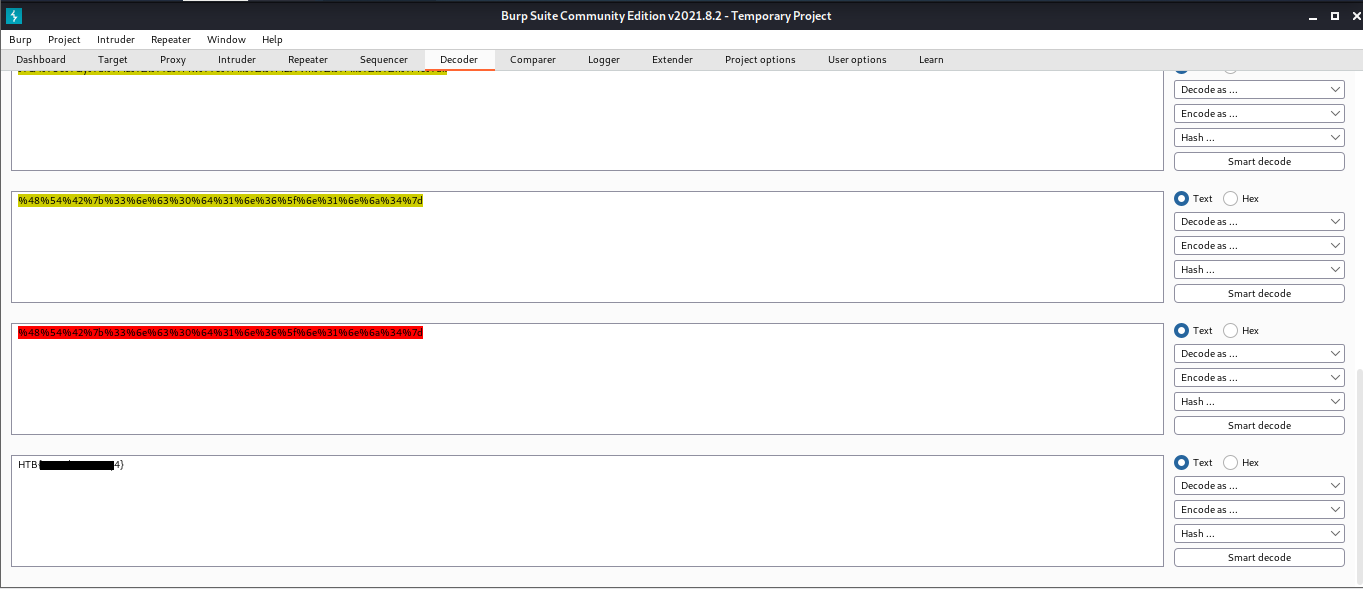
The string found in the attached file has been encoded several times with various encoders. Try to use the decoding tools we discussed to decode it and get the flag.
Day 13 –
Proxying Tools
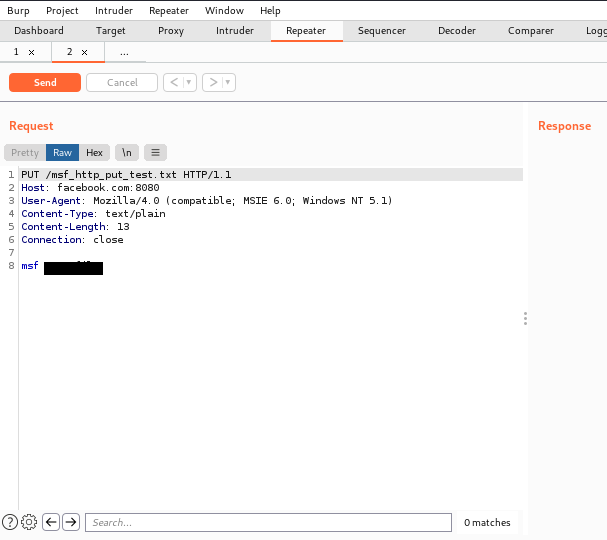
Try running ‘auxiliary/scanner/http/http_put’ in Metasploit on any website, while routing the traffic through Burp. Once you view the requests sent, what is the last line in the request?
Web Fuzzer
Using Burp Intruder, fuzz for ‘.html‘ files under the /admin directory, to find a file containing the flag.
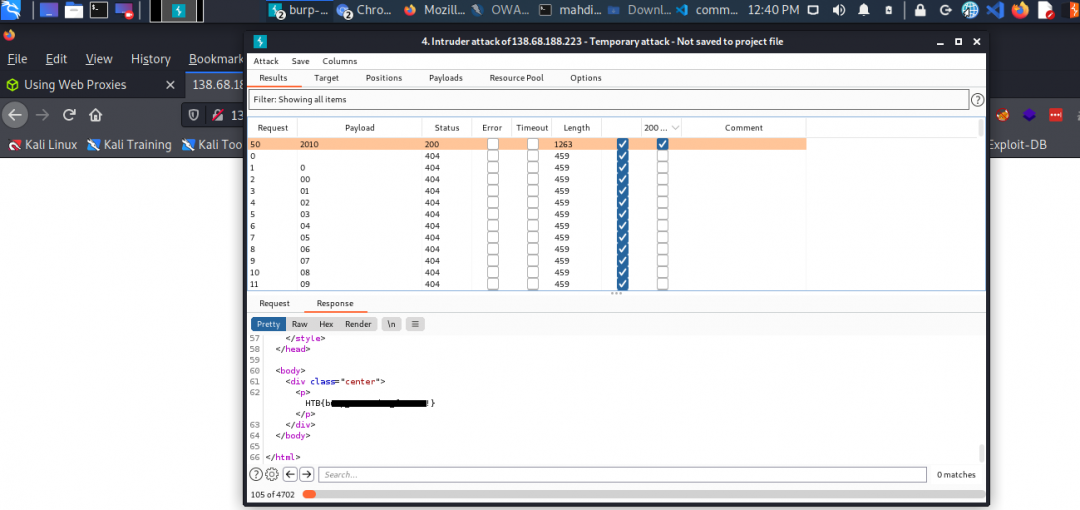
“There’s a price to pay, but that price lies in the interest one is willing to spend learning it.”
Day 14 –
Zap Fuzzer
The directory we found above sets the cookie to the md5 hash of the username, as we can see the md5 cookie in the request for the (guest) user. Visit ‘/skills/‘ to get a request with a cookie, then try to use ZAP Fuzzer to fuzz the cookie for different md5 hashed usernames to get the flag. Use the “top-usernames-shortlist.txt” wordlist from Seclists.
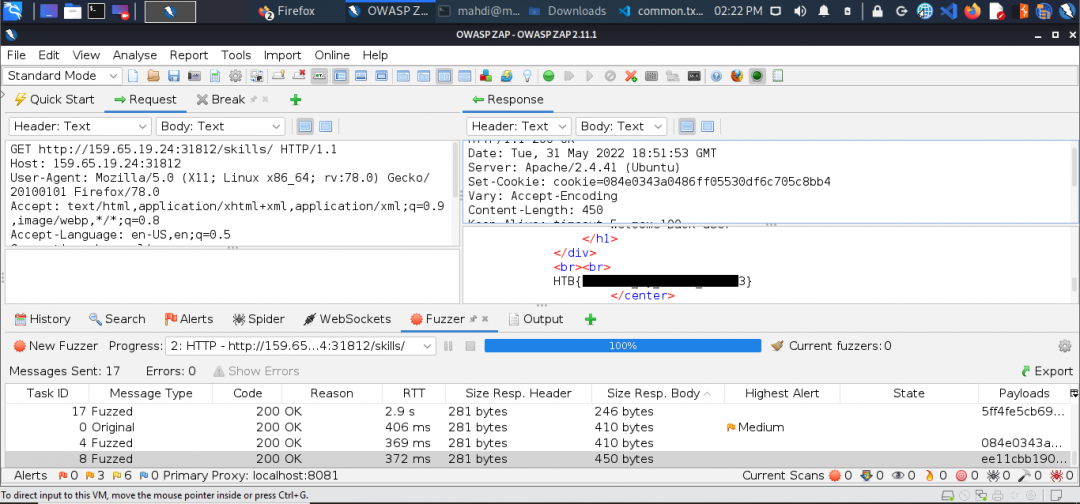
Day 15-
Zap Scanner
Run ZAP Scanner on the target above to identify directories and potential vulnerabilities. Once you find the high-level vulnerability, try to use it to read the flag at ‘/flag.txt‘
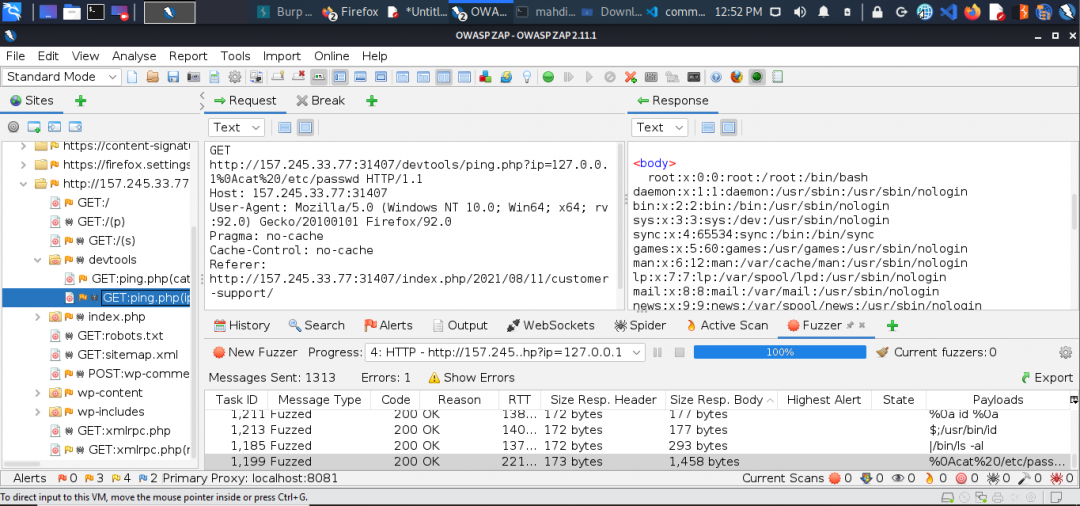
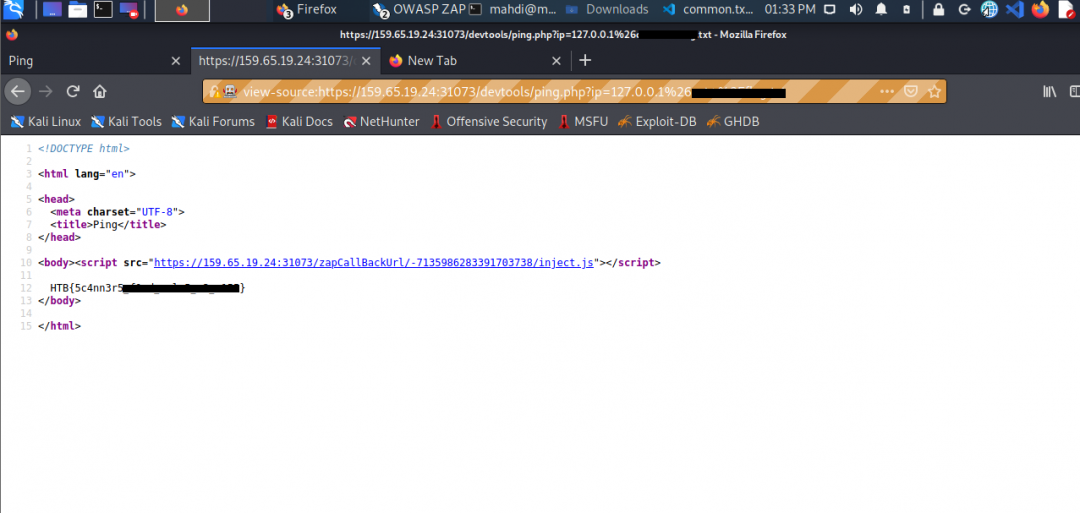
Day 16
Covered extensions and how they extend the functionality each of the tools. For instance, repeating the previous exercise, I was quickly able to locate the vulnerable injection point using the newly installed FuzzDB Files extension.

Days 17 – 20
Using Web Proxies
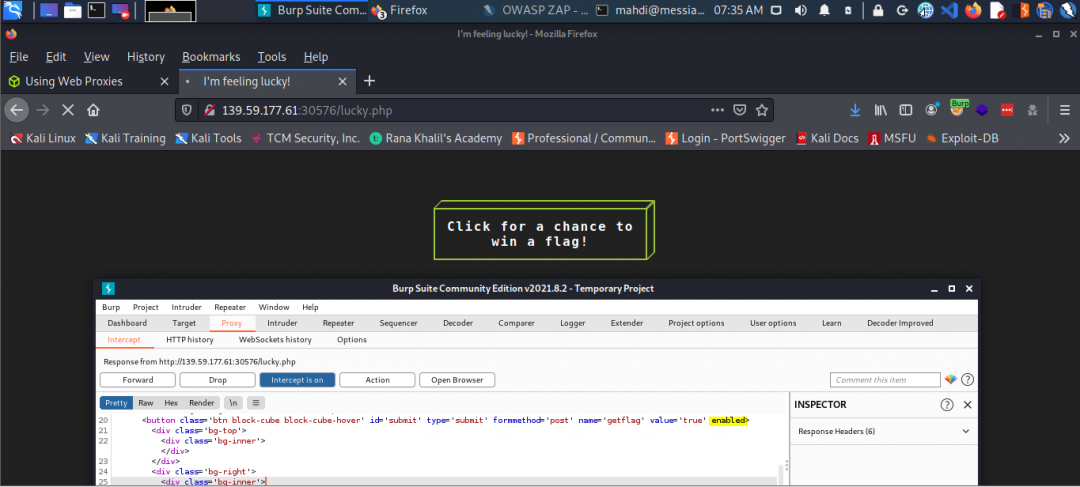
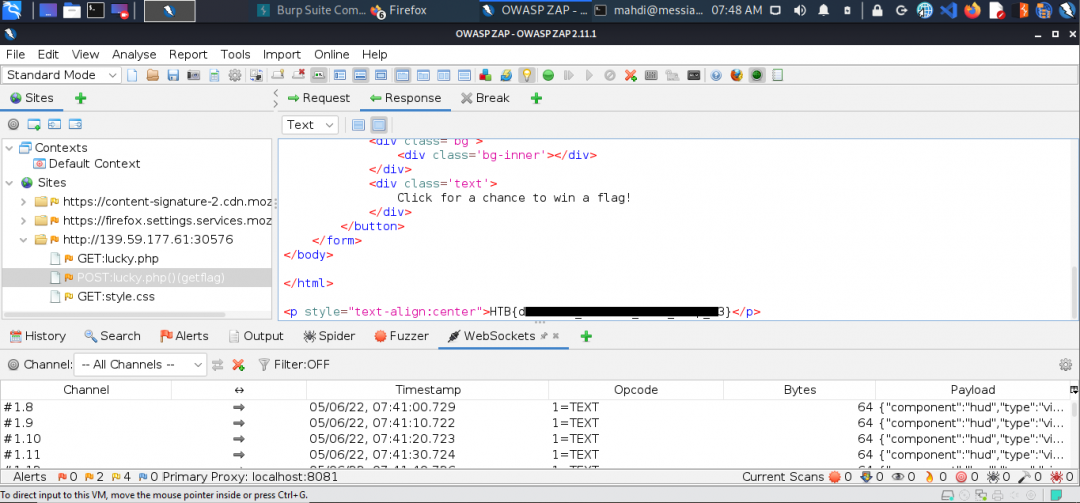
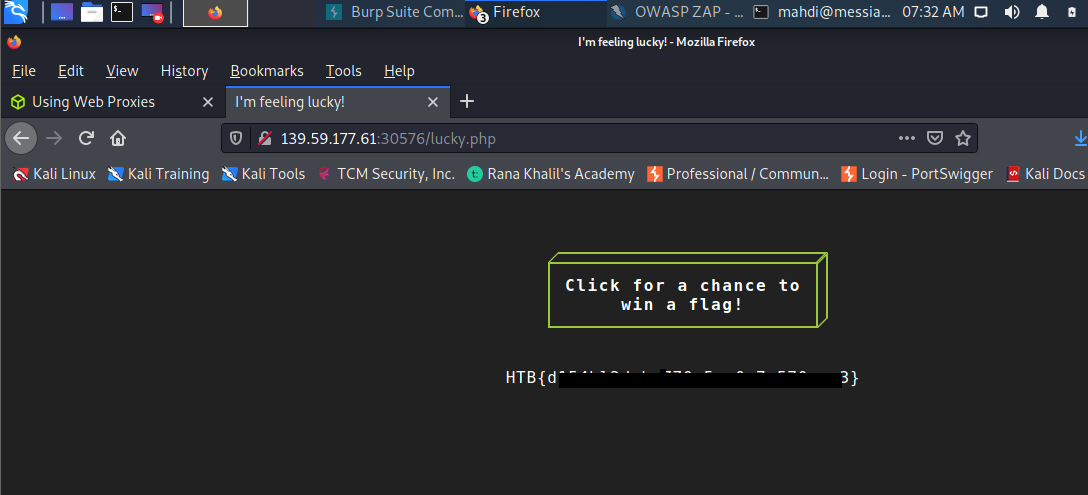
The /lucky.php page has a button that appears to be disabled. Try to enable the button, and then click it to get the flag.
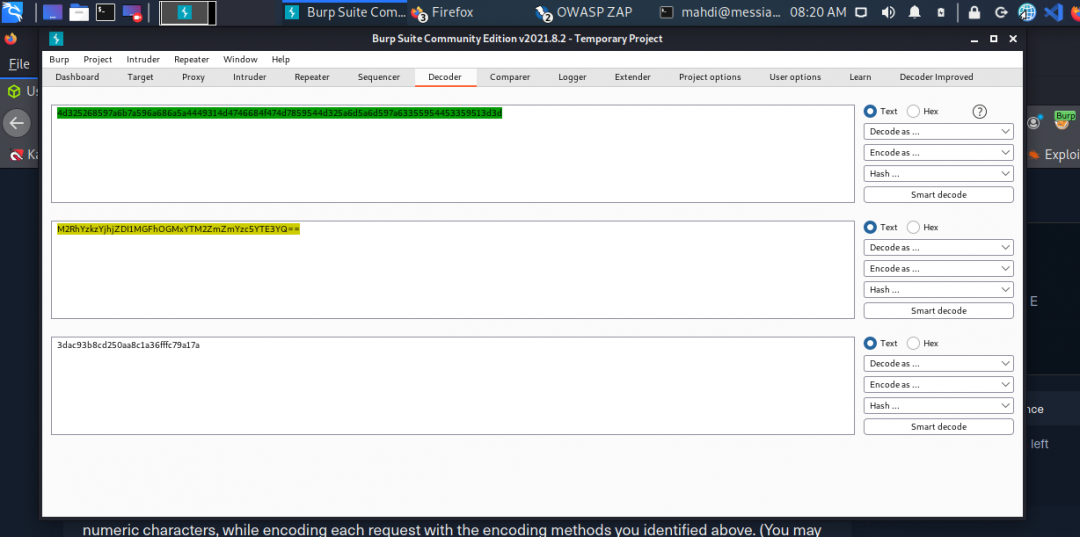
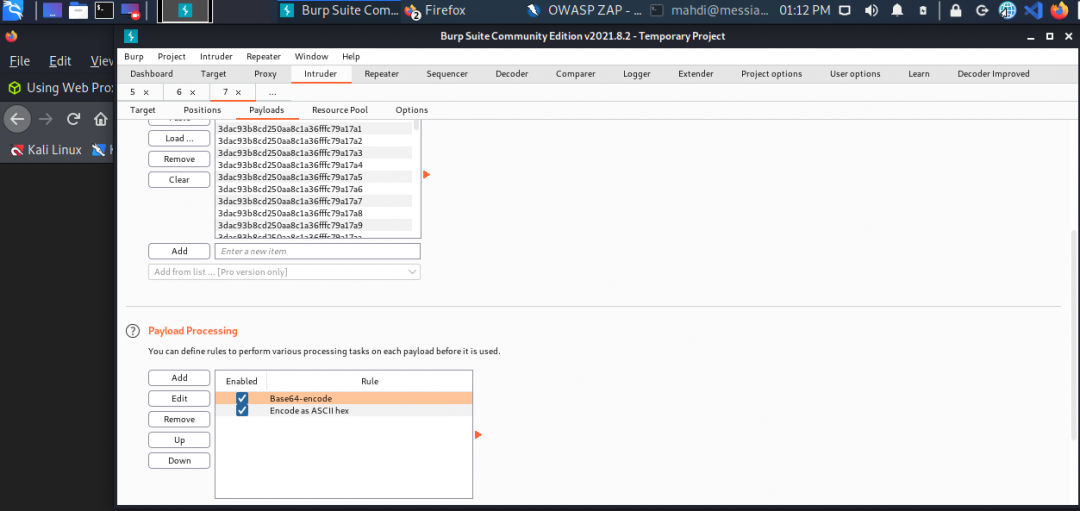
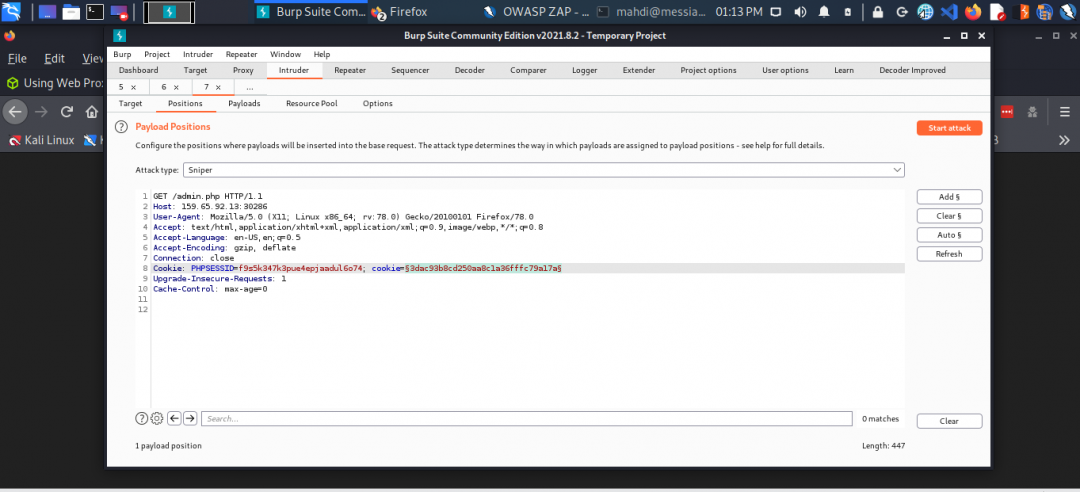
The /admin.php page uses a cookie that has been encoded multiple times. Try to decode the cookie until you get a value with 31-characters. Submit the value as the answer.
Once you decode the cookie, you will notice that it is only 31 characters long, which appears to be an md5 hash missing its last character. So, try to fuzz the last character of the decoded md5 cookie with all alpha-numeric characters, while encoding each request with the encoding methods you identified above. (You may use the “alphanum-case.txt” wordlist from Seclist for the payload)
This deserves some explanation. The way I ultimately solved this was:
- Created a new word list by using the decoded md5 hash as a prefix to each entry in the alphanum-case.txt. Why? Well, the hash is missing the last value so using the hash itself as the prefix effectively makes each entry in the wordlist the missing value to fuzz for. (At least that’s how I understood it).
- Next went Burp > Intruder> Payloads > Payload Processing and added encoding in the reverse order which the has was decoded.
- Finally, Burp > Intruder > Positions and selected the entire md5 hash.