Practical Web Application Security and Testing
15
September, 2022
Days 49 – 54
Practical Web Application Security
100 Days of Hacking
Photo cred – Markus Spiske
For these Days of Hacking I wanted to take a break from the Bug Bounty Job Role path on HTB and turn my attention to a curse that had dropped over on TCM Security called Practical Web Application Security and Testing. This course was loaded with both fundamental and advanced concepts. Overall, what I particularly loved about the course was the hands-on activities with docker containers and OWASP Zap. I completed the course and again, the following are from the Days of Hacking while working on it.
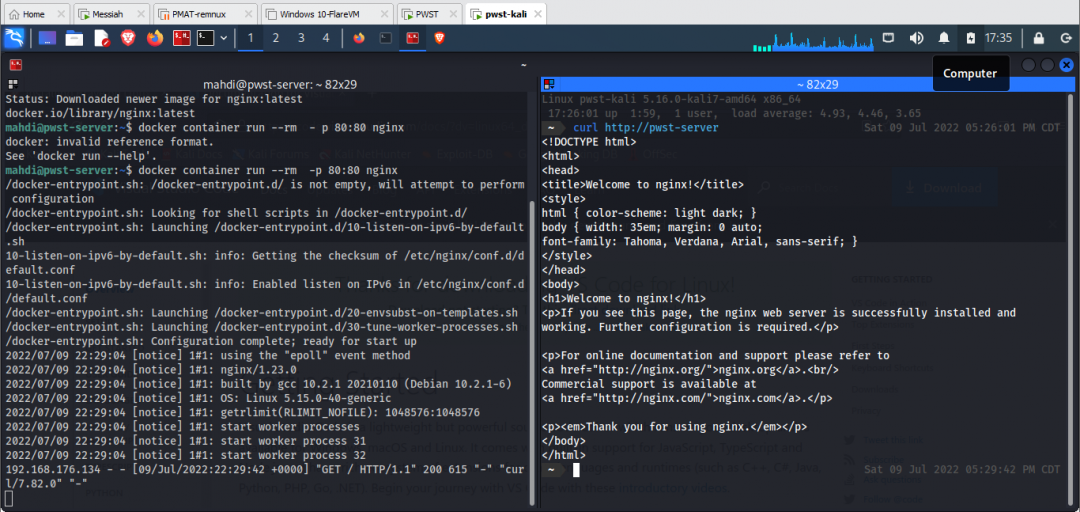
The first lab was setting up a web server running nginx inside of a docker container.
After setting up the lab, we then made a few requests from our Kali machine to the web server. Our first set of requests were made using curl. The image on the left is a web server access log. Looking at the last line we can see source ip, timestamp, http method, the uri, the protocol, the response and size of the response.
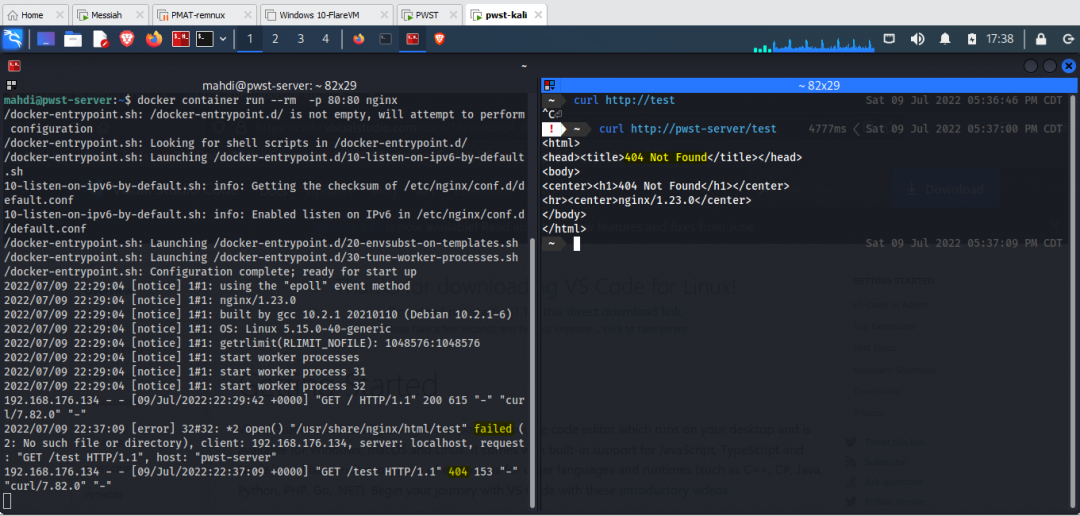
Then we made a request to the server using the path /test. Again, we see the ip but instead of a 200 response we get a 400. In addition to the 400 on the access log, we also receive an error log along with the default page that the server is configured to serve up on 404 responses.
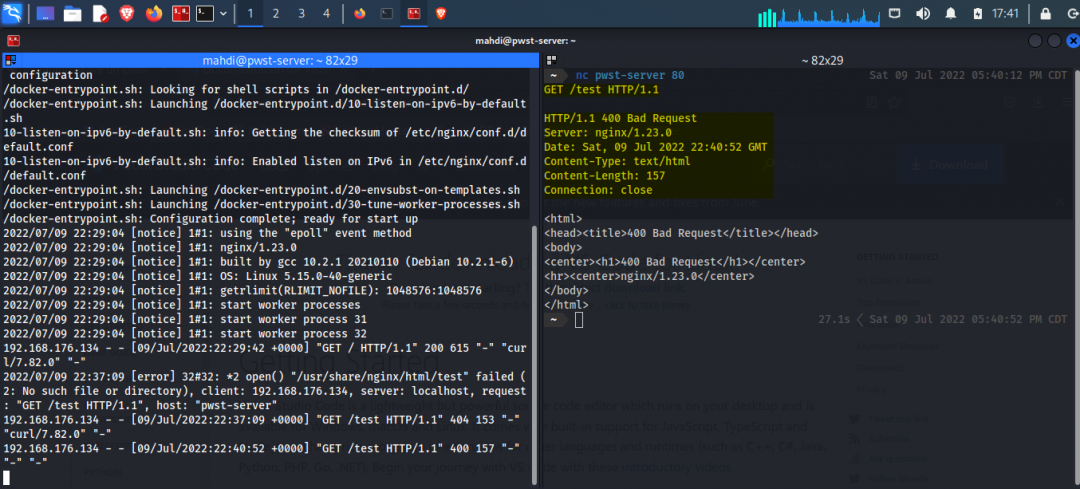
Next, we try making the same request as above but with a utility called netcat.
And then moving along, we demonstrate making a request the most common way requests are made and that’s with a web browser.
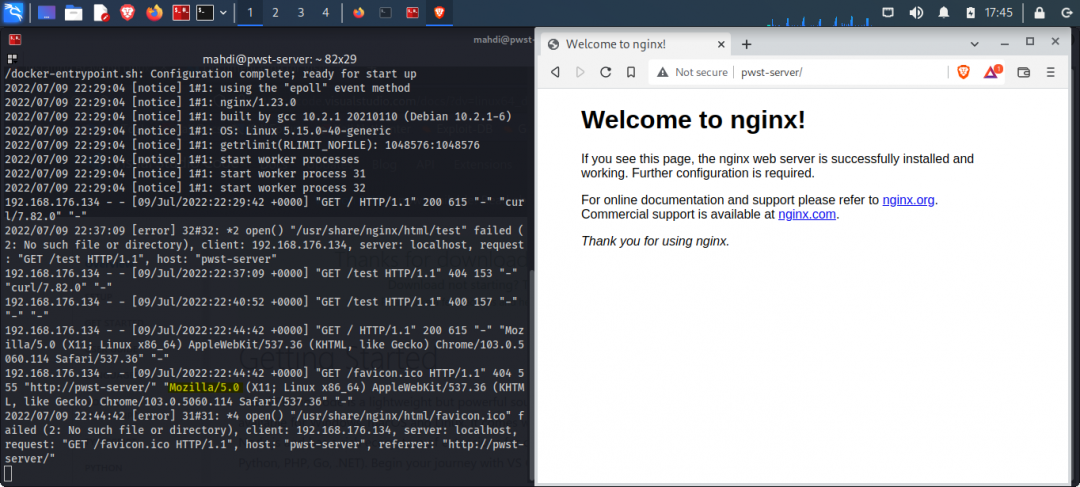
Enumerating and Fuzzing with Zap
Next we start our intro to using Zap by examining the Spider feature. Naturally, as we know from our fundamental web security skills, we must examine the source code (or view source) of our pages. What we’re doing is looking for comments that devs have left behind.
We also explored using wordlists to do Fuzzing with Zap.

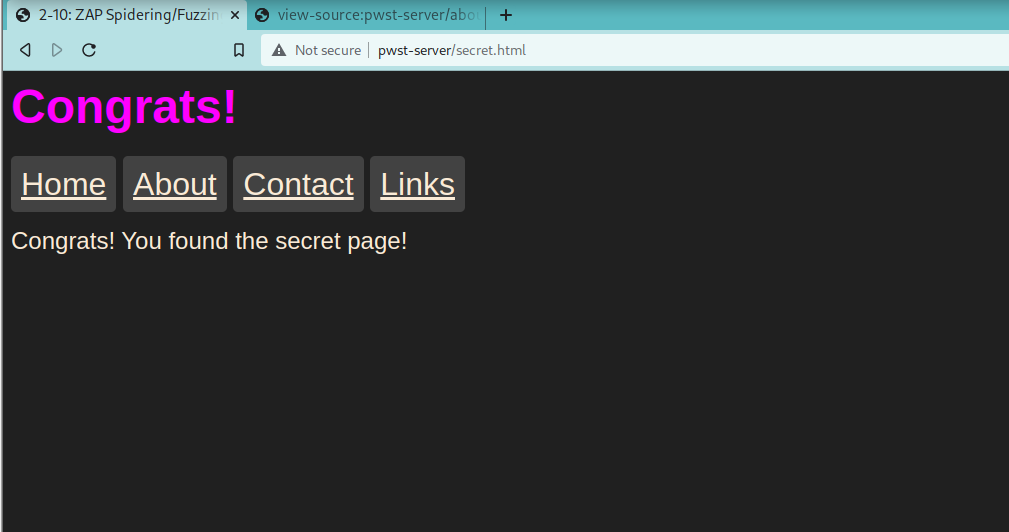
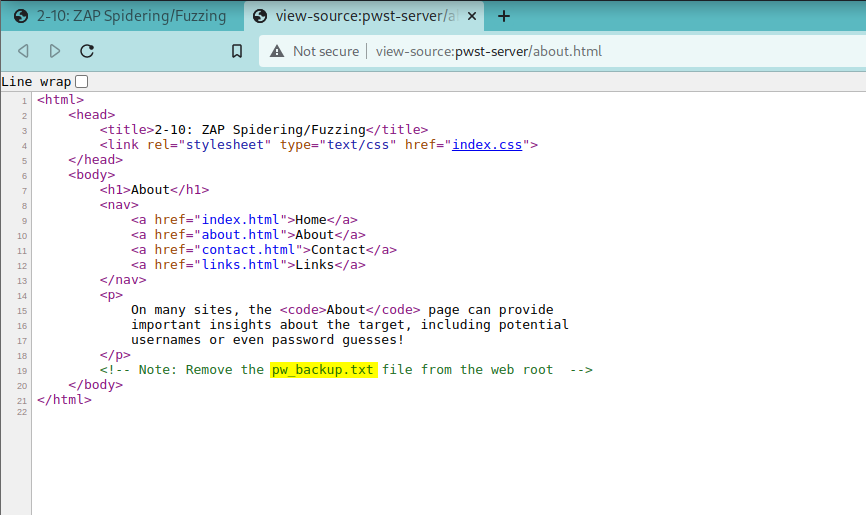
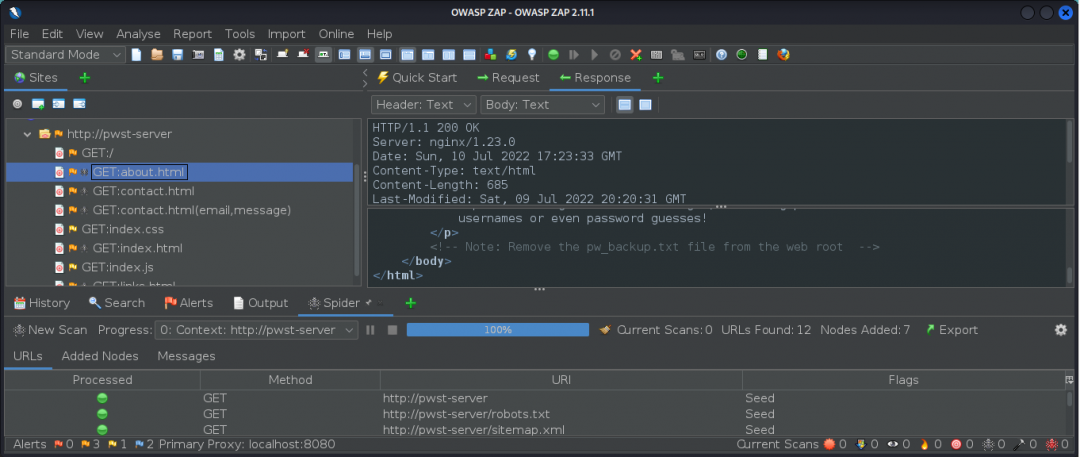
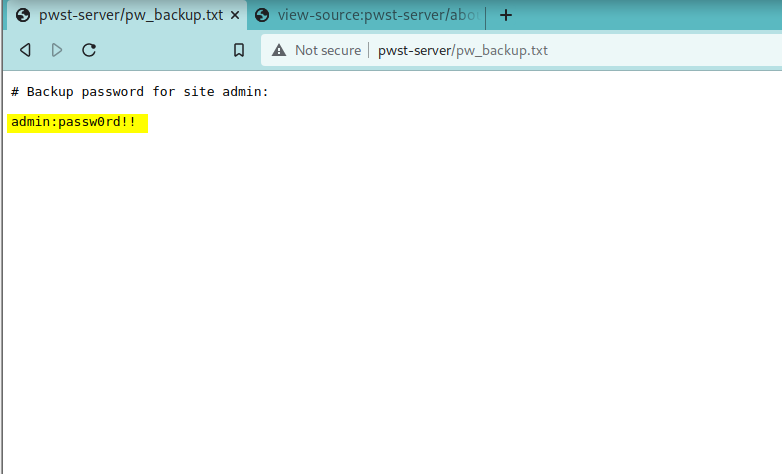
That’s about as far as I got on those days. Hopefully, it was enough of a preview that someone reading this will take interest in the course. It’s a very awesome course that I highly recommend to anyone looking to get into Bug Bounty or Web App Security and seasoned vets who’ve been away from their craft for some time and needing to vamp up.
As always, it’s been Real. Hack On, Ladz & Gentz!


