Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
22 April 2024
Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
If you’ve been following along with our web hacking posts then you’re undoubtedly aware of the many aspects of IDOR vulnerabilities that we’ve covered thus far. In this post we’ll be looking at a simple example of bypassing encoded references, and staying the course of the Bug Bounty Job Role Path over on HTB.
Bypassing Encoded References: The Hidden Code and How It Can Be Cracked
Many websites today use clever tricks to protect sensitive information. One common method involves “scrambling” data using a process called hashing. Imagine you have a secret recipe, and instead of writing it down, you turn it into a jumbled code only you can understand. That’s kind of how hashing works!
However, even with these protections, sometimes there are ways to crack the code, especially if some of the secret recipe ends up accidentally left in the open. In the world of websites, this “open recipe” could be code that reveals how the scrambling is done.
Take the following scenario- we have a web app where can download contracts. The IDOR vulnerability isn’t as obvious as the previous ones we’ve encountered where say, we had UIDs being passed in cleartext, for example. Here, we can see that our UID is being hashed and thus, we are not able to determine it’s original value. Sure, there’s things we can attempt.
We could for instance determine the hashing algorithm being used, make a hash of other values in the application and then compare them for a match; then, if we hit the jackpot we’d just rinse and repeat for the other users. However, this isn’t the case here. Let’s look at this a little closer.
U-I-D’S in clear text
makes it easy to enum,
I hate to eat my cubes
but they easy to consume.
Web apps that make them hashes
or encode they object refs
might be difficult to enum
but the trick is what gets left.
As Bug Hunters we also know that along with the clever tricks used to scramble data, many websites today are built using tools called JavaScript frameworks (like Angular, React, or Vue.js). These frameworks help developers make the “front-end” (the part you see and interact with) of the website look great and function smoothly.
But sometimes, developers accidentally put things they want to keep secret in the front-end code. This is like leaving a recipe for your secret sauce out in the open! Anyone who can see the code could figure out how to do the same thing themselves.
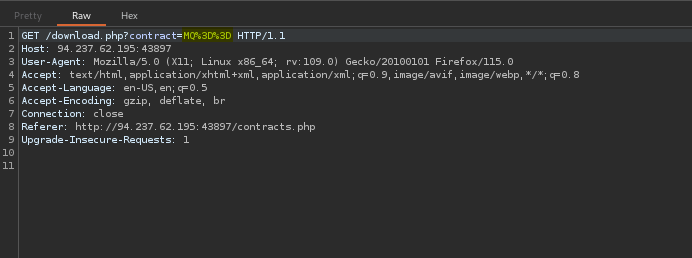
In our example, the website lets us download a document. The secure way to do this would be to have the website itself handle the download process behind the scenes. However, in some cases, the code that controls the download might actually be visible in the front-end. This could allow someone to figure out how to bypass the website and download the document themselves, which could be a security risk.
Let’s have a look at the source code:
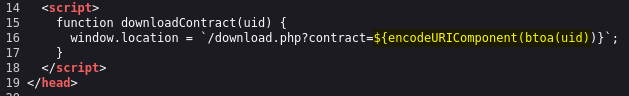
Some developers mess up
and put their functions on the front,
Forgetting it be hackers just like us who like to hunt.
If your hash is calculated…..
then we can replicate it,
Be happy that we finding bugs
stop acting like y’all hate it.
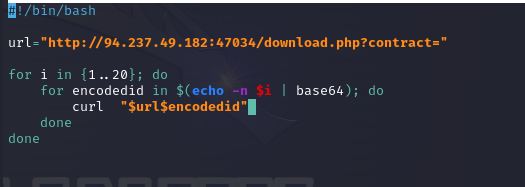
Now let’s say that we wanted to download the contracts of the first 20 employees, one of which contains the very sensitive information that we are searching for, in this case, our flag. To do so, we first have to find which “scrambling” method is being used. Then, we simple need to calculate the same thing for each employee’s UID.
For that purpose we can use this handy little script. (Courtesy of one of the awesome community members in the academy).
It’s your function that’s gone snitch you out
and give up what you do,
That source code won’t commit
and it looks like it trust you too.
When we click on Edit Profile
we are taken to a page,
to change some information on that user that you made.
Name, Email, and About Me
those are common in some apps,
change the details, click on Update, now let’s see what we get back.
Look at that….
The hashes match the ones in our request,
Submit this to the triage team so they can run their test.
To bypass encoded refs…..
Keeping Websites Secure: It’s All About Keeping Secrets Safe
In the world of web development, there’s a constant battle between keeping things secure and making websites user-friendly. We’ve talked about how websites use special tricks (like scrambling data) to protect sensitive information. But just like a secret recipe, these tricks can only work if they’re kept secret!
Well, community, that’s all I have for now. As always, thank you for reading. I’m including a link to the forums which also links to the module in the academy that we took a look at in case you’d like to take a more in depth. By all means give it a try cause as one of my mentors always says, “It ain’t real unless you put your hands on it!”
Hack On, Ladz & Gentz….


