Analyzing Unknown Binaries- Dynamically

Quintius, Day 2, 100 Days of Hacking
22 May 2022
When I said this journey was not going to be linear in nature, Day 2 is an example of that. Although I’m writing this on Day 5, the events occurred on Day 2. My initial curiosity was sparked when I came across a position of interest that potentially involved analyzing malware. At times that I need to get up to speed on a skill that I have absolutely no experience in, I do what’s carried me to where I’m at today; I seek out the shoulders of giants to stand on. What better shoulders than Practical Malware Analysis and Triage?
You remember that feeling you got when you were about to root your first box or pop your first web shell? Or running Nmap or Wireshark for the first time? As cool and super far out techie that analyzing malware sounds, there’s comes with it a feeling just as rushed. The awareness that one is willingly about to release a malware specimen onto their client and network.
There’s the obvious question of how to handle the malware safely? Admittedly another cool thing for me jumping into the unknown world of malware analysis was being exposed to new tools. Namely Remux and Flare, two systems which up until this course I had no clue even existed. The next coolest thing was building out an isolated environment and getting into the habit of creating snapshots. And to top that all off, using and predicting tons of scenarios where I can use inetsim in the future.
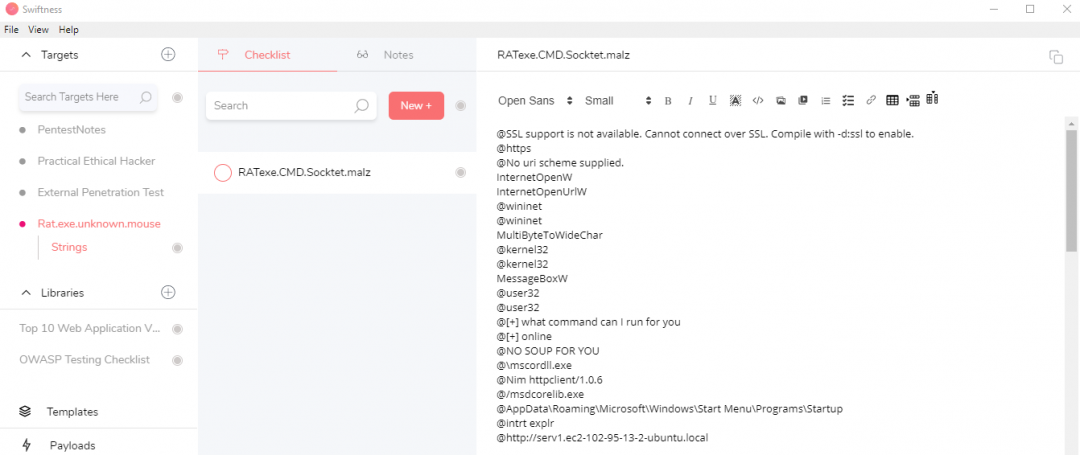
The methodology was to write the output of FLOSS to a file for easier consumption. Extract the interesting strings that may become useful during the dynamic analysis phase. At this point, when enumerating the output of FLOSS, I translate this activity to be equivalent to looking for “low-hanging fruit” during the Recon phase of a penetration test.
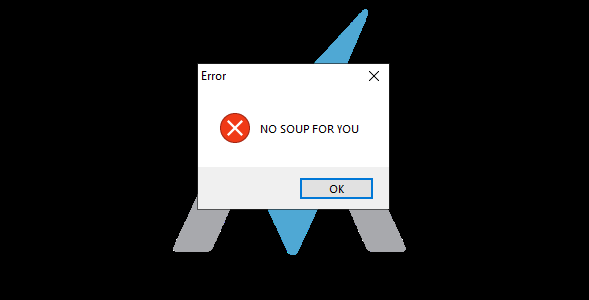
After arming the malware and executing it, the initial detonation revealed a pop-up box with a message. This isn’t to say that delivering a pop-up box to the user’s screen is the “only” thing the malware does, but this is undeniably something that it did.
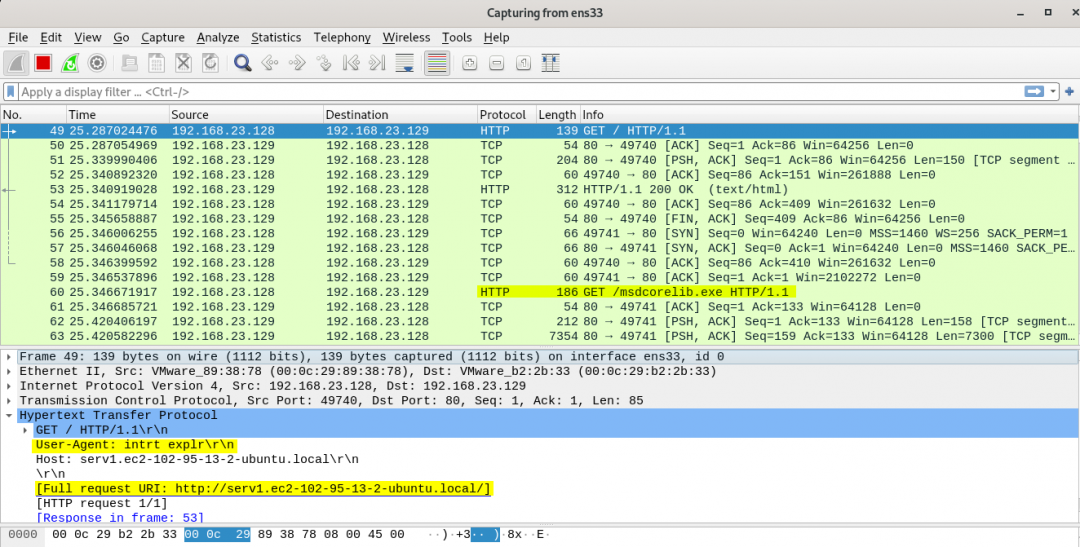
At this point we dig for more information. For instance, are there any network-based indicators? A way to figure that out was to monitor activity through Wireshark upon execution.
Interestingly we discover there’s a uri, a GET request with a USER AGENT worthy to be taken note of, and another GET request to a .exe. Combining these discoveries from those above, we can surmise that when the binary has somewhere to reach out to on the internet, the error message is not displayed.
Although this information isn’t enough to definitively say we understand the malware, we do have pieces that correlate- for instance, we now again see some of the strings we discovered doing string analysis with FLOSS.
Potential File Download – msdcorelib.exe
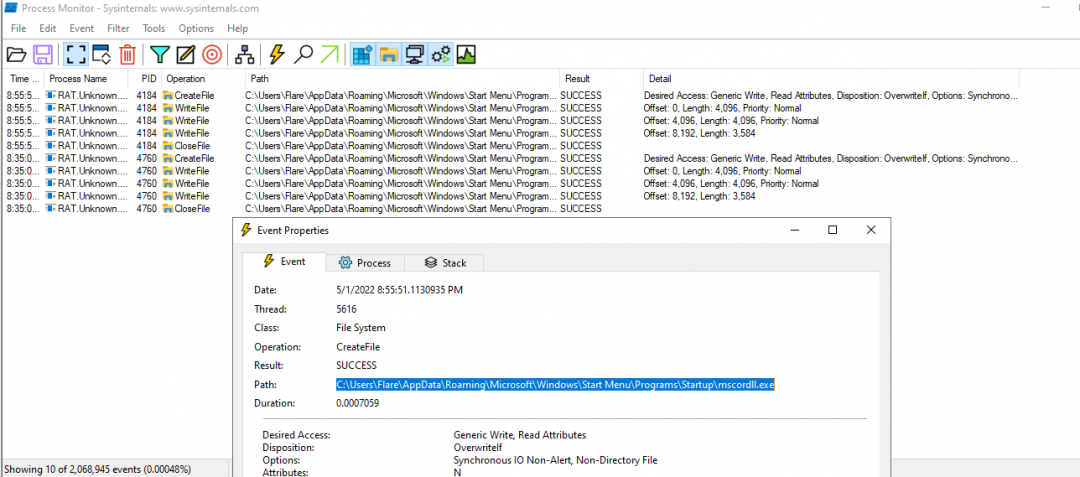
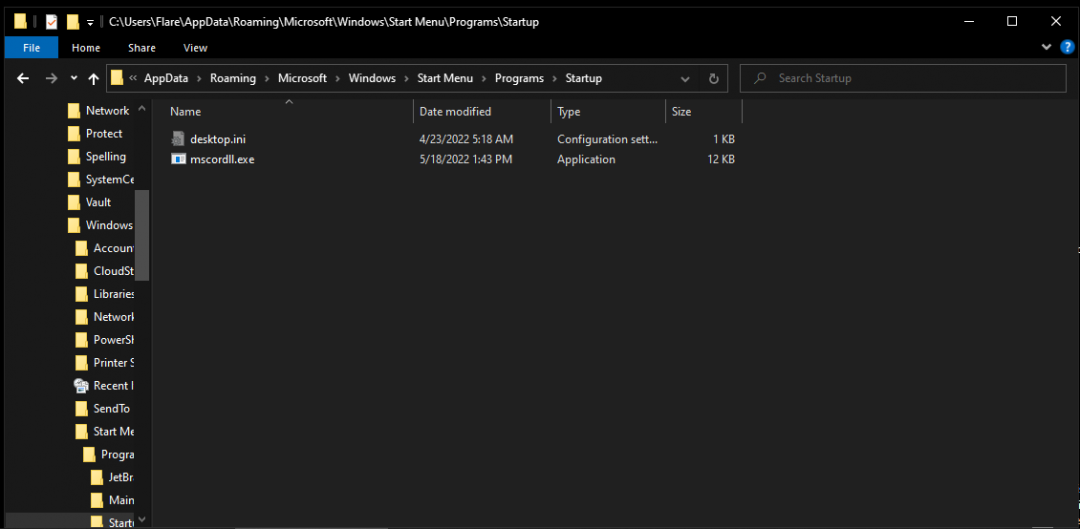
It could be that msdcorelib.exe gets written to the start up directory. Of course that would be a hypothesis. To test such hypothesis we could use another super tool that I now know how to get some practical use out of. We could filter on “operations” in Promon. If we go back to our notes and grab the interesting file path, we can run the malware and see if something happens in that path.
Indeed we find that there has been something written to the file system. Thus, we have evidence of a persistant binary.
We’ve uncovered quite a lot of useful information but the analysis task is far from complete. In another post I’ll finish the dynamic analysis but for now I just wanted to pivot to something that I came across in this morning’s reading assignment. It’s from Lesson 6: Hacking Malware in the Hacker Highschool cirriculum. While dissecting this malware I was struck with the same thoughts reflected in the lessons. It’s tough to understand how malware writers use these wonderful techniques that software giants don’t.
“It’s tough to understand why malware writers use these wonderful techniques that giant software makers don’t.”
Again, my interest and encouragement aren’t to build and unleash malware on the world nor on acquaintances. It’s all about seeing how malware works and gaining an understanding of the methodology and tools associated with Malware Analysis. Stay tuned for Part 2 as where I continue my investigation into analyzing unknown binaries.
Hack on, Ladz and Gentz!