API- A Poetic Interpretation of Broken Access Control
Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
3 November 2023
Photo by Walter Gaspar on Unsplash
Everything on this blog that surrounds the term “hacking” is used for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
In this post we’re still examining vulnerabilities that fall in the category of Authorization and Authentication, only this time we’re looking into API’s and Broken Access Control. If you recall, we are sharpening our axes in preparation of becoming practical web hackers who’ll someday successfully find some bugs and help companies patch up any gaps in their web security. And if that sounds like a win-win, my friend…let’s dig in. (See what we did there?) ![]()
API: A Poetic Interpretation of Broken Access Control
Contrary to the title of the article, API doesn’t stand for “A Poetic Interpretation”. API simply stands for Application Programming Interface and if you’re trying to grasp what an API is, just know they aren’t really different from what you already know of what happens when a client requests a resource from a web entity.
However, in terms of testing, what’s different is how API driven applications behave and likewise, our methodology for testing them also differs.
Let’s get some information,
About the Cats Facts
A P I,
Some devs be thinking
they can stop this hacking
so they try…
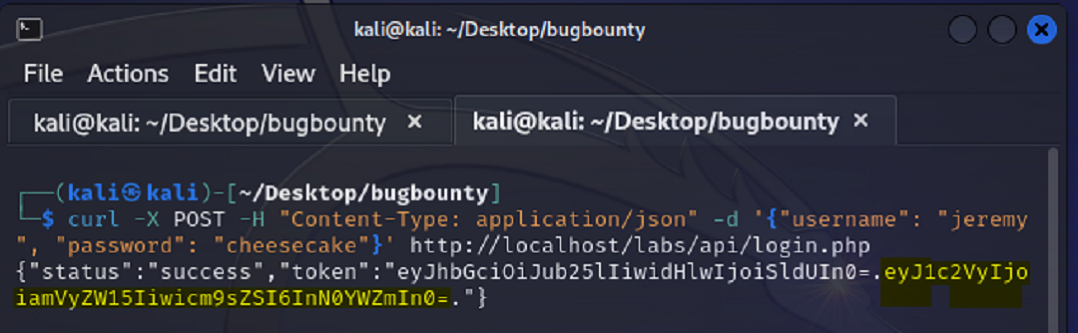
In the following screenshot where we are sending a POST request to a web entity, if you look right after token: there’s a long line of gobble-d-gook separated by two periods. This is our JWT, or Json Web Token.
The part before the first period, the unhighlighted part, is the header, the part after the period, highlighted in yellow, is the body, and there should be another part after the second period, called the signature. Which in our case is missing.
To break me…
And contemplating ways
To make me cry,
They hope the culture cancels me
But they just rate me high.
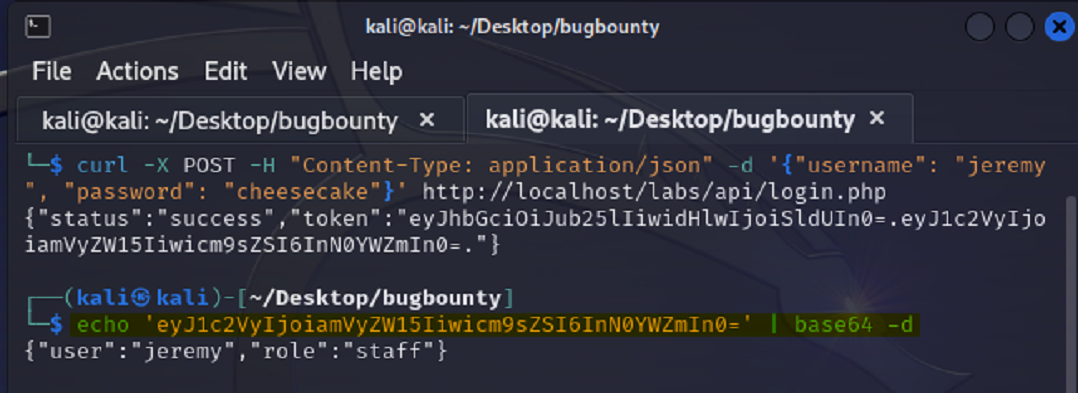
The gobble-d-gook is what’s called Base64 encoded and can be decoded in a number of ways. One being right in our terminal like the following screenshot. To do so, all we need to do is copy the body of the token and run the command highlighted in the screen shot.
So to test it,
Let’s make some basic calls
To peep the structure,
Wit’ Curl to make a Get requests
No need to use our fuzzer.
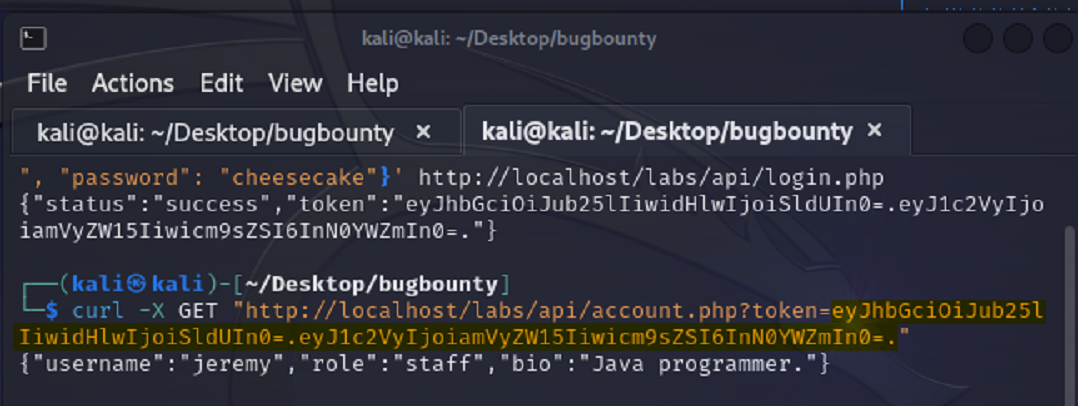
Now this time we’ll send a GET request and use our JWT as the value for the token parameter in the url. (token=)
So we move into our lab,
Get introduced to tokens,
If we can change the signature
That means control is broken.
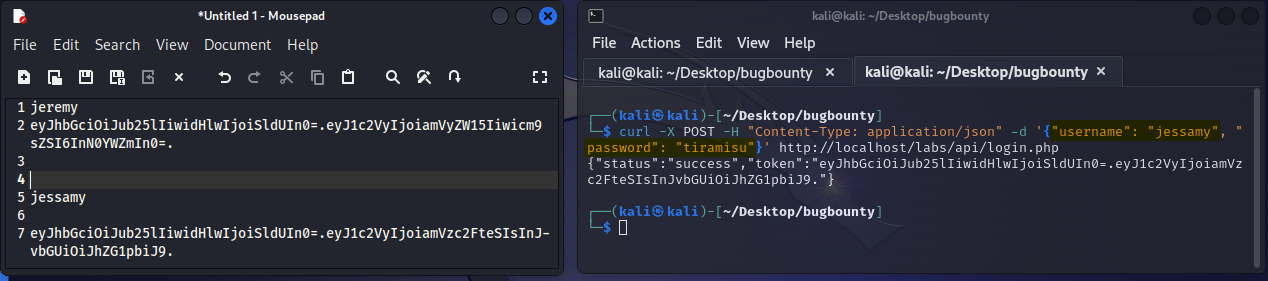
Once again we’ll run our POST request but this time we’ll use a different username and password. This of course returns a different JWT as seen in the following screenshot. (Also, as you can see, we’ve placed both users along with their respective JWT’s in a notepad for clarity.)
Don’t mess with the JTW’s because they’re out-of-scope,
We hunt these bugs just like a fiend
When he be out of dope.
Now. What is our goal? Our goal is to test if we are able to update the account information of the user Jessamy by means of Jeremy’s JWT.
The PUT method is used to update so we’ll start by verifying that Jeremy is able to update his bio.
Then we’ll use our GET method again to verify the changes as shown below.
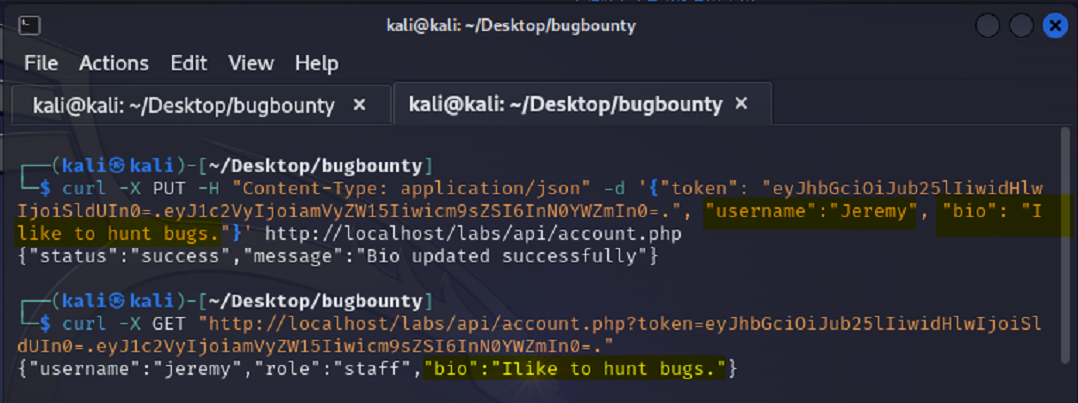
For this token we send Jessamy
Then verify it worked,
And make sure it’s the user Jeremy’s bio
That get twerked.
If the update is successful then it’s Broken Function Level,
But don’t get too bogged down with all these details in the devil.
Next, we’ll send the same request and token but only this time we’ll be targeting our other user Jessamy. So, in this case we’ll change both the username and the bio fields then we’ll verify that we were able to update with our changes.
Now we’ll once again send our GET request, but this time we’re going to use Jessamy’s JWT. What we’re after is evidence that Jessamy’s bio was indeed changed to our desires.
(Notice the JWT’s in the PUT and GET requests aren’t the same.)
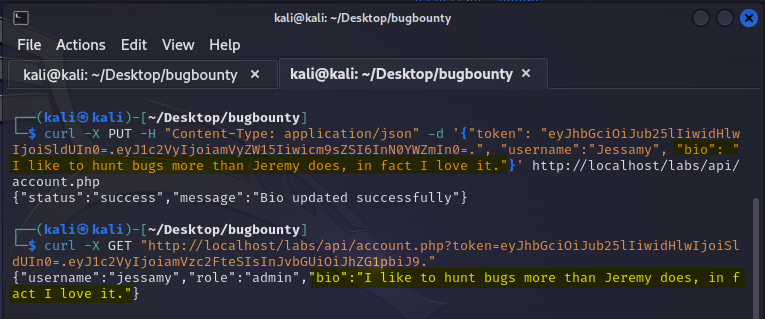
We now can see that our efforts were successful. This is an example of Broken Access Control.
Or the devils in the detail’s,
the same with A P I’s
Blue Team be dreaming,
screaming that they scheme.
can take these guys.
If you’ve made it this far, thank you very much. If you liked the article please share it with your network and by all means return back to the blog in a few days where we’ll be continuing on with our journey to becoming practical bug bounty hunters.
As you may already know if you’ve kept up with our most recent articles, TCM Security has partnered with Intigriti to put together and release an official Practical Bug Bounty Course. Big ups to TCM Academy for blessing us with another gem. Shouts out to Heath and special shouts go out to Crypto Cat and Alex Olsen both – who I hadn’t checked out until this course.
Hack On, Ladz & Gentz!


