Attacking Web Apps: Fuzzing with Ffuf
10
July, 2022
Days 30 – 35
Attacking Web Apps: Fuzzing with Ffuf
100 Days of Hacking
This post will cover Fuzzing a web application. Fuzzing is fundamental when testing web applications. Tons of info, clues, assets can be discovered through Fuzzing.
More specifically, we’ll be using the automated web fuzzing tool called ffuf. We are still grinding along HTB’s Bug Bounty Job Role Path, Attacking Web Application with Ffuf.
Attacking Web Applications with FFuf
Day 30
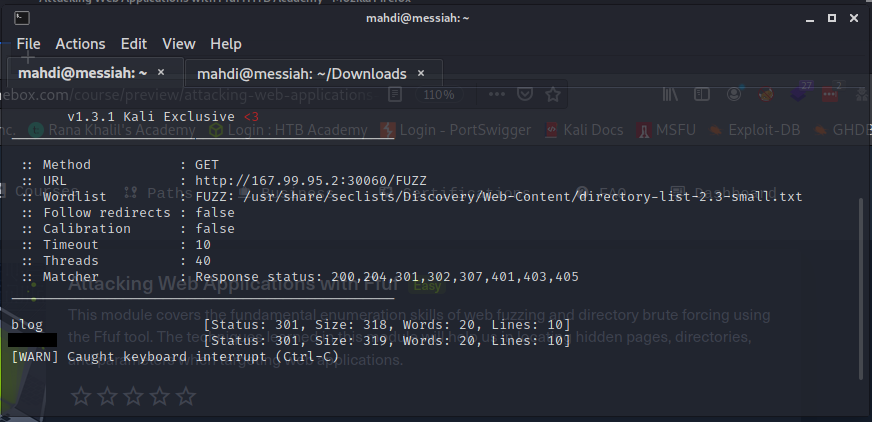
Directory Fuzzing
In addition to the directory, we found above, there is another directory that can be found. What is it?
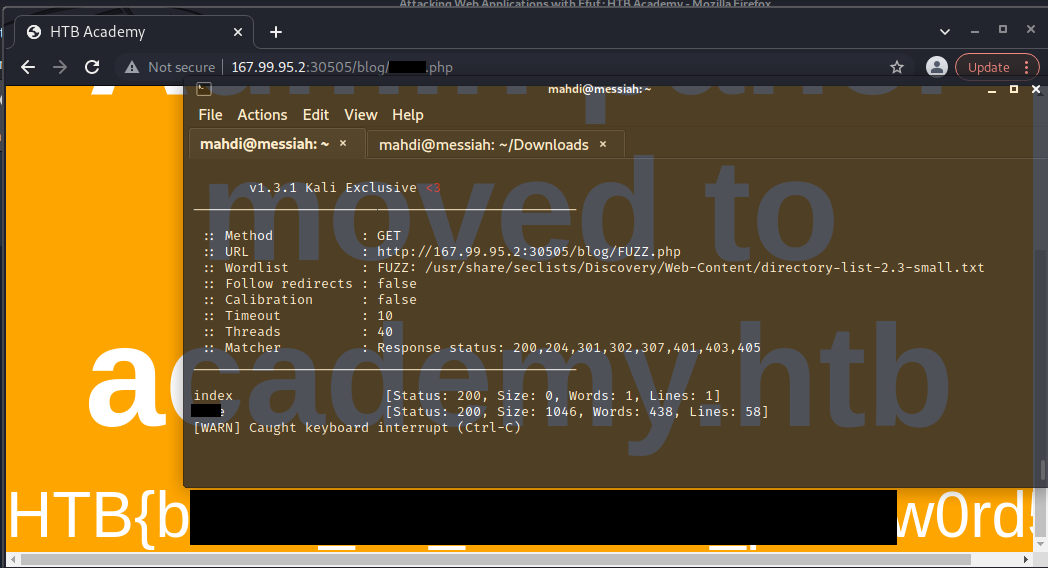
Page Fuzzing
Try to use what you learned in this section to fuzz the ‘/blog’ directory and find all pages. One of them should contain a flag. What is the flag?
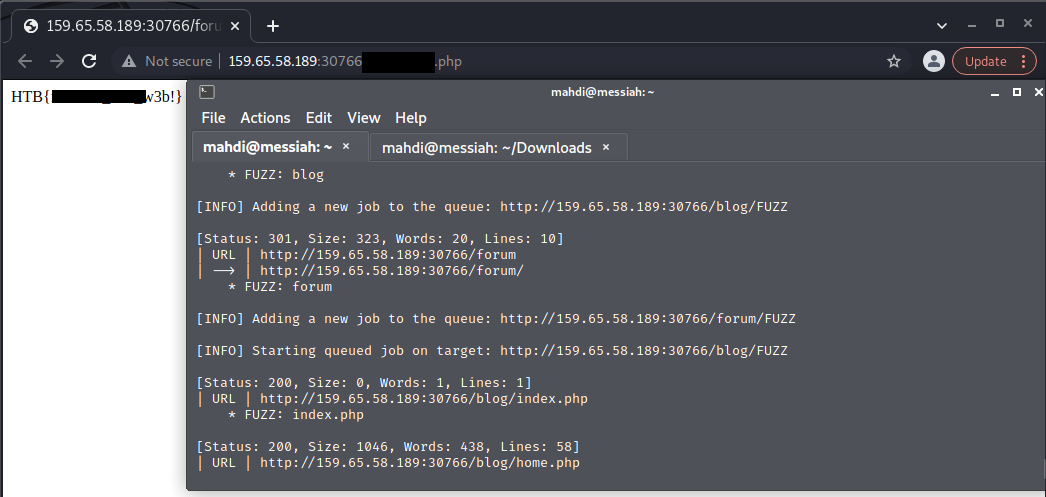
Recursive Fuzzing
Try to repeat what you learned so far to find more files/directories. One of them should give you a flag. What is the content of the flag?
Day 31
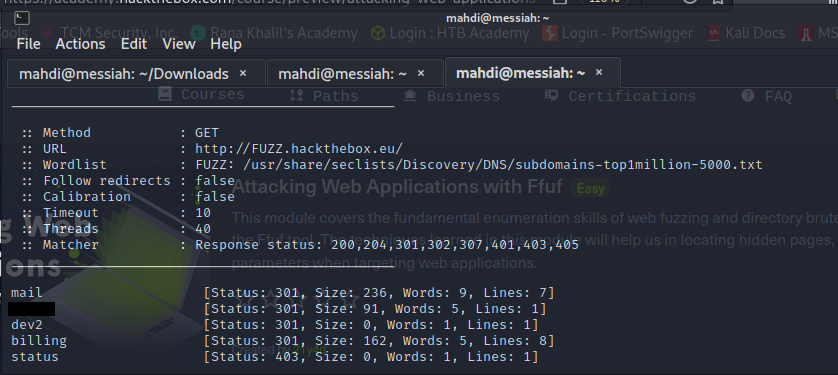
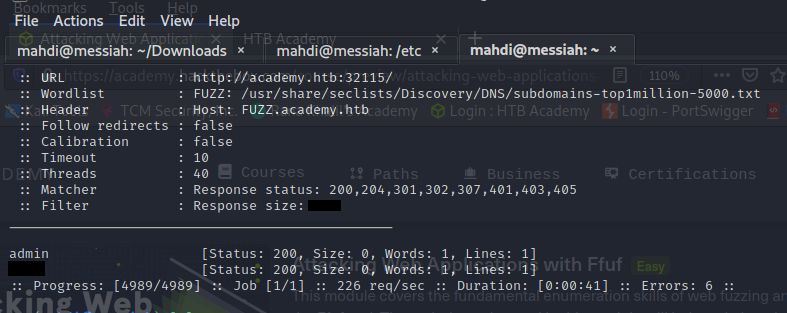
Sub-Domain Fuzzing
HackTheBox has an online Swag Shop. Try running a sub-domain fuzzing test on ‘hackthebox.eu’ to find it. What is the full domain of it?
Filtering Results
Try running a VHost fuzzing scan on ‘academy’ and see what other VHosts you get. What other VHosts did you get?
Day 32 – 33
Parameter Fuzzing – GET
Using what you learned in this section, run a parameter fuzzing scan on this page. what is the parameter accepted by this webpage?
Day 34 -35
Try to create the ‘ids.txt’ wordlist, identify the accepted value with a fuzzing scan, and then use it in a ‘POST’ request with ‘curl’ to collect the flag. What is the content of the flag?
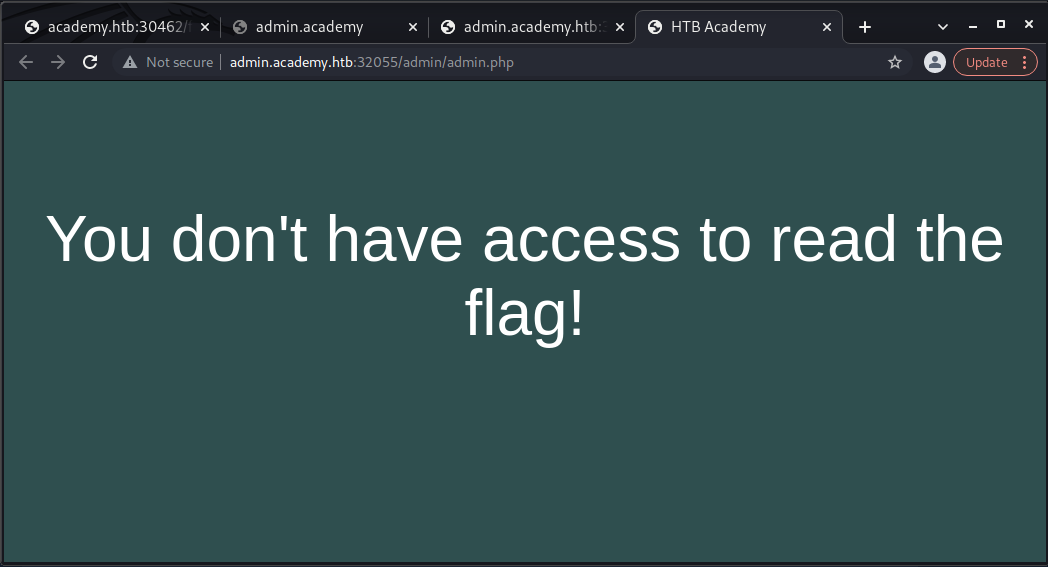
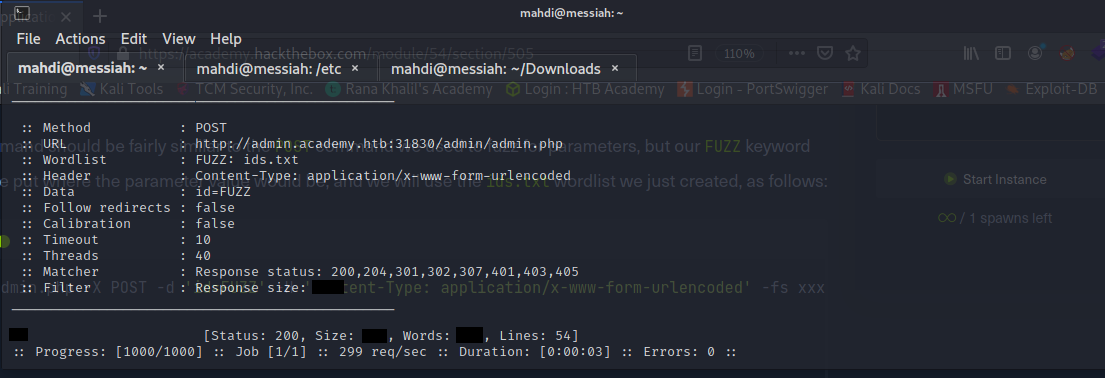
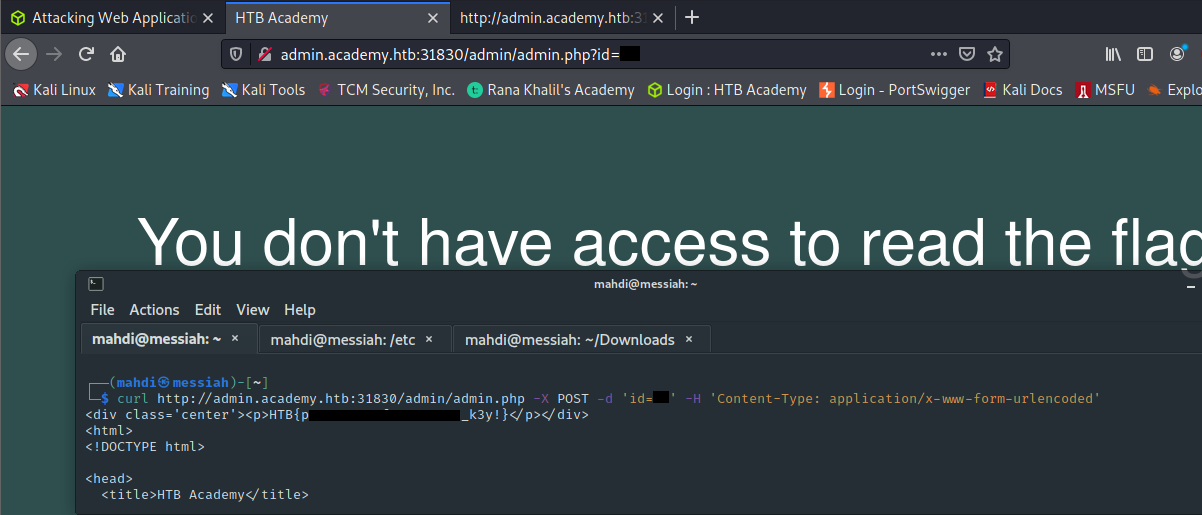
As a Penetration Tester a skill that you must have is being able to manually navigate websites, clicking all the links available and also finding ones that may not be made public and quite possibly, may not be secure.
In the Ffuf module we learned how to locate those pages, directories, and params. Most importantly, how to use our findings to leverage an attack on an application.
As always, Hack On, Ladz & Gentz!
“Beyond the regular rules…one must use subtler origins.” – Cao Cao


