What’s Beef? BeEF is when I see you
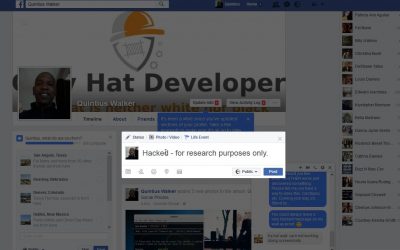
Today the enemy has a name for me-Target 23 MAY, 2017 Grey Hat Developer In a space that's on constant alert for a nasty ransomware attack, the ninja looks past the hardened network perimeter and the client system, and walks straight through the open door- the web...
Theoretical Facebook Authentication Attack Vector
19 January, 2017 Grey Hat Developer Are you familiar with the Theoretical Facebook Authentication Attack Vector? Well, in this post we're going to look at a theoretical attack vector using Facebook notifications sent to one's email address. Update: Since the date that...
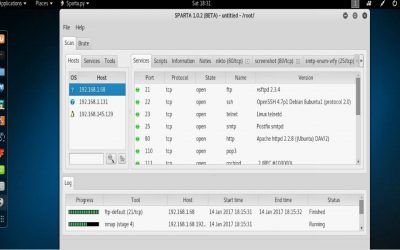
Performing Automated Reconnaissance with Sparta
Automated Reconnaissance with Sparta Grey Hat Developer 16 January 2017 As a security tester you should ensure that you understand a tool before using it in an actual security test. Some tools may return information that is out of scope, or out of agreed upon terms of...
Your Anti-Virus Software Won’t Save You
Your Anti-Virus software won't save you Grey Hat Developer 18 December 2016 You ever start your computer and have a message waiting for you that's from your anti-virus program that says something along the lines of "You are protected...everything is up to date"? If...
Scanning and Exploiting the Purposely Vulnerable
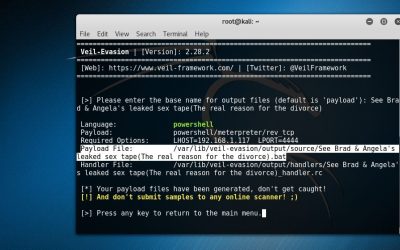
Vulnerable on Purpose Part 2- Scanning and Exploiting 9 DECEMBER, 2016 Grey Hat Developer In this post we're not only going to do some more scanning but we're also going to do some more exploiting of our target just to get a bit more familiar with running exploits...
Vulnerable On Purpose: An Introduction to Metasploitable
Because attacking live systems is never a good idea Your enemy has the same weaknesses as you do In our last post we did some scanning and enumerating on a target so you're already familiar with that process and how all of it works. Now we're going to look at it from...
“Wax on, wax off.”- Getting to know your target
Brick by brick the patient thief carries away the rich man's house in a single night Thus far we've covered a lot of stuff that, admittedly, may not have seemed fun nor sexy. In the initial learning stages of getting to know your target, any of it rarely is. But trust...
Scanning and Enumerating: Secrets Bleed Like Blood
It is widely held that the Romans successfully built their own novice navy into a formidable fighting force after capturing and "reverse-engineering" a Carthaginian warship that had run aground. This would be not only yet another example of how "chance favors the...
Cutting-At-The-Edges: Exploiting Human Weaknesses
Bleeding my enemy is the next greatest joy to burying him I'm sure a lot of us are familiar with Miyamoto Musashi- the Buddhist, the Samurai, the artist, the writer. Yes, no, maybe so? Well, to some he's become known as the greatest swordsman to ever live. With over...
Reconnaissance: The Streets Is Watching
As a hacker, intelligence will be the bread and butter of your power Before I ever even considered pursuing a career in penetration testing, I use to snuggle up in bed breathlessly reading The Art of War by Sun Tzu, just wondering how it was going to end. Yes, I took...
-

Unisex t-shirt
$25.00 – $29.50 -

Unisex Hoodie
$35.00 – $39.00 -

Unisex eco raglan hoodie
$45.50 – $49.50 -

-

Glass jar soy wax candle
$17.00 -

Short-Sleeve Unisex T-Shirt
$18.00 – $21.50 -

Embroidered Beanie
$19.50 -

Snapback Hat
$21.00 -

Champion Hoodie
$56.00 – $58.00 -

Embroidered Champion Packable Jacket
$49.00 – $52.00 -

Backpack
$44.50 -

Snapback Hat
$21.00