A Hacker’s Top 10 Rules For Success
A hacker is not so much an entity, a being, a title as it is a mentality. Most people are familiar with Tupac the rapper/actor. But I wonder how many people ever looked at him as being a hacker? That's right. Tupac was indeed a hacker. Evan Carmichael carved out...
What’s a handle all about?
@The_StarHack3r Lesson 1: Being a Hacker - Choose a handle for yourself In Lesson 1: Being a Hacker there's a section that talks about handles and the different reasons that hackers use them. In sum, hackers use them: For fun (<-- this mostly applied to hackers in...
Hacking Kung-Fu: Aims and Objectives- Part 2
“ Test your systems with fire and ice, sand and sea, bile and blood....before your attackers do! ” In this post we're going to wrap up the Hacking Kung-Fu series. We're still digging in and focusing on aims and objectives so this will be a bit lengthy. Thus, without...
The Generals 6 Movers of Hackers
A long time ago there was this guy who, some claim to be one of the greatest generals of all time. Of course, we've seen a lot of great generals which leaves this claim up for much debate. However, that debate is not what we're going to tackle here. Instead, what I am...
The Three Requirements For Attainment
The Three Requirements for Attainment Part 2 of Hacking-Kung Fu: Its Aims and Objectives There are countless reasons why students fail to achieve their objectives in their Kung Fu-Hacking training, but to help us understand the factors that contribute to...
Hacking-Kung Fu: Its Aims and its Objectives
Part One In this post I will be using the term “ Hacking-Kung Fu ” to point out the similarities that exist between hacking and Kung Fu. Thus, when you see the words hacking or Kung Fu, realize that I'm intending to use these two words interchangeably. Getting Better...
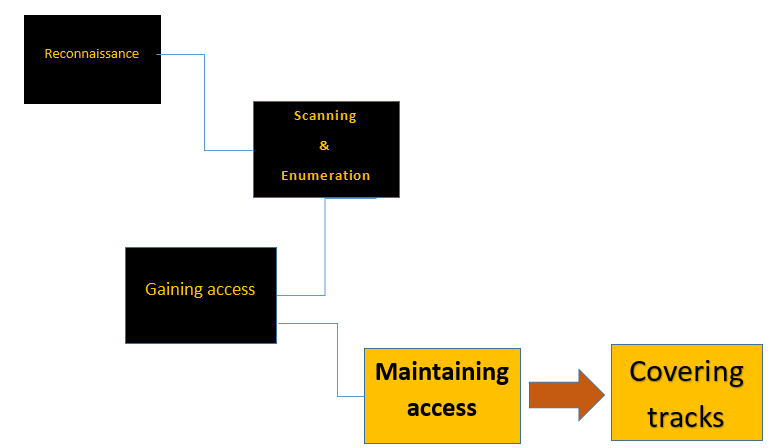
The 5 phases of a standard hack
Before we go further into any more of the technical aspects of hacking, I want to point out that normally, hacking is a process. This remains true for the individual hacker as well as for the collective hacker group. The majority of people I meet, before being...
Setting up a vulnerable application
You've decided to wear a hat, now what? Now it's time to start getting our game up. Remember I said that we'd be getting back to the "what" of hacking? Well, that time has arrived. As I recall, we came to an agreement that the word hacker itself implies a state of...
You’ve decided on a hat to wear-Now What?
In a previous post, What Color is Your Hat? , we discussed taking a look into the "whys" of wanting to become a hacker. (relax, it's safe to use that word over here. We get it.) Now we're going to start addressing the "hows" of becoming a hacker. Hold on. Back up. Let...
What Color Is Your Hat?
It's been 6 long years that I've journeyed onto the path of becoming a professional penetration tester/certified ethical hacker. A somewhat rather lofty ideal if you must. Along this journey I've managed to step away with quite a few jewels that I believe would be...
-

Unisex t-shirt
$25.00 – $29.50 -

Unisex Hoodie
$35.00 – $39.00 -

Unisex eco raglan hoodie
$45.50 – $49.50 -

-

Glass jar soy wax candle
$17.00 -

Short-Sleeve Unisex T-Shirt
$18.00 – $21.50 -

Embroidered Beanie
$19.50 -

Snapback Hat
$21.00 -

Champion Hoodie
$56.00 – $58.00 -

Embroidered Champion Packable Jacket
$49.00 – $52.00 -

Backpack
$44.50 -

Snapback Hat
$21.00