Are you familiar with the Theoretical Facebook Authentication Attack Vector? Well, in this post we’re going to look at a theoretical attack vector using Facebook notifications sent to one’s email address.
Update: Since the date that this was originally posted, it appears Facebook has partially fixed the problem. We’ve conducted subsequent test and an attacker is no longer able to authenticate into a victim’s Facebook account via the shared notification link. However, as per Facebook’s response, if an attacker is able to compromise a victim’s email account then, yes, it is still possible for the attacker to gain access to the victim’s Facebook account via shared notification links without being checked for valid authentication. Thus, the theoretical attack vector still exist. Albeit, per Facebook, it’s intended functionality.
Update: As of 11/10/2019, I doubt this still works.
And the story begins….
Once upon a time when there was a student who had been up all night burning the midnight oil. The clock was well into the wee hours of the morning and he thought he’d just have one last look at his incoming emails. This was to be his last task before retiring to bed. Unbeknownst to him, his night was about to get a little bit longer….
Me: Time zones. It’s morning time in your neck of the woods, right?
Pete: (sends picture of clock-The hands on the clock point at 9 ) AM. Been up 3 hours working and getting kids ready for school. Editing 2 more books for the RSA conference.
Me: Yep. It’s 2 a.m. here. I was about to call it quits for the night, checked my Gmail, and under the social tab I had an alert from FB. I saw one where you’d shared the link to the Cyber-Security Playbook. I don’t know why but I clicked the “view” link. Now mind you, I’m not logged into my FB account anywhere on my computer- no closed nor forgoten tabs or nothing. So I click the link and it opens in FB and it has me logged into my account.
Pete: WTF?!
(end dialogue)
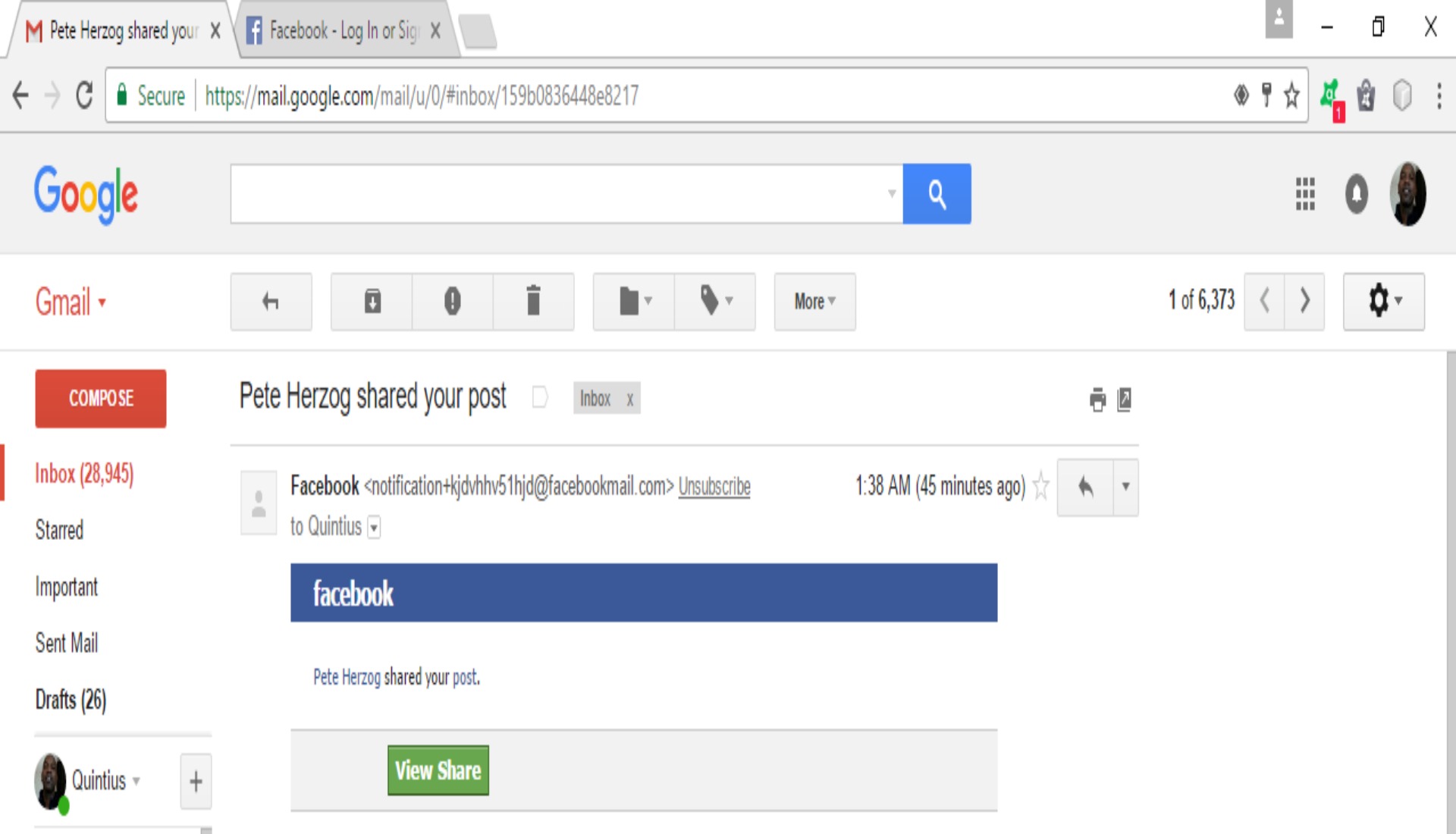
The following screenshots are of:
- What’s suppose to happen under the above circumstances.
- What actually happened.
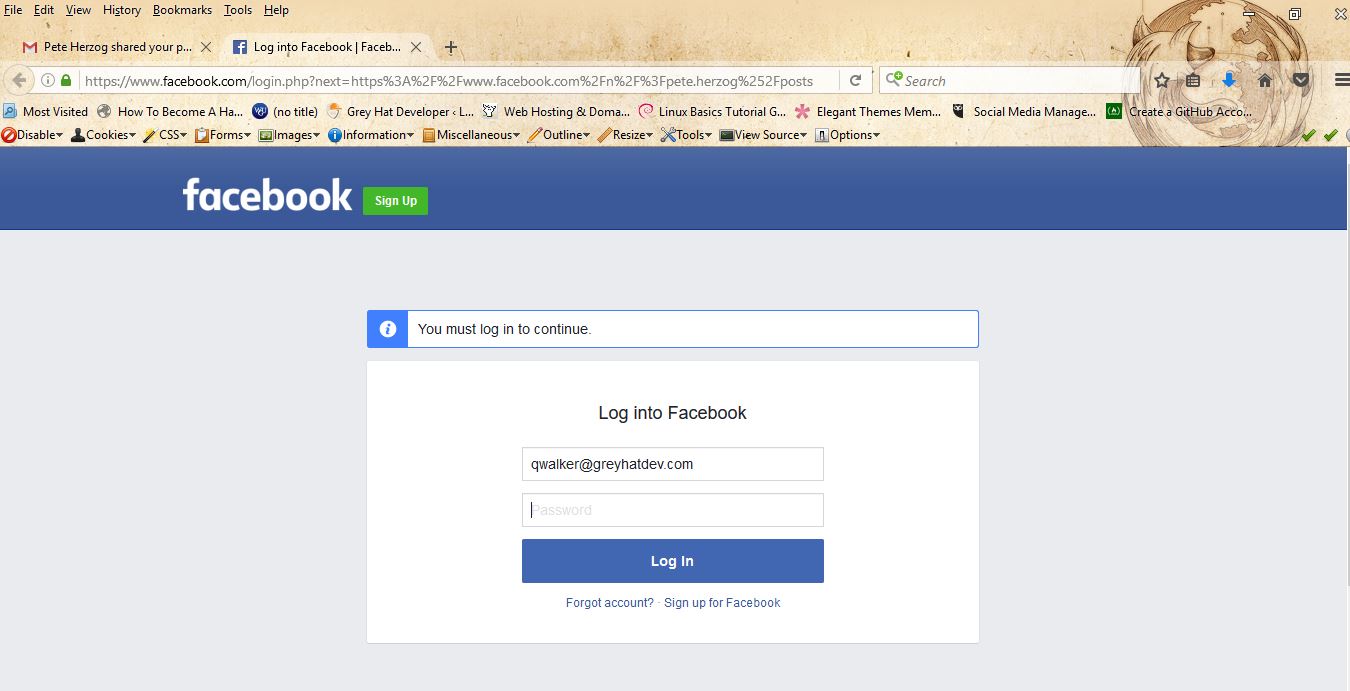
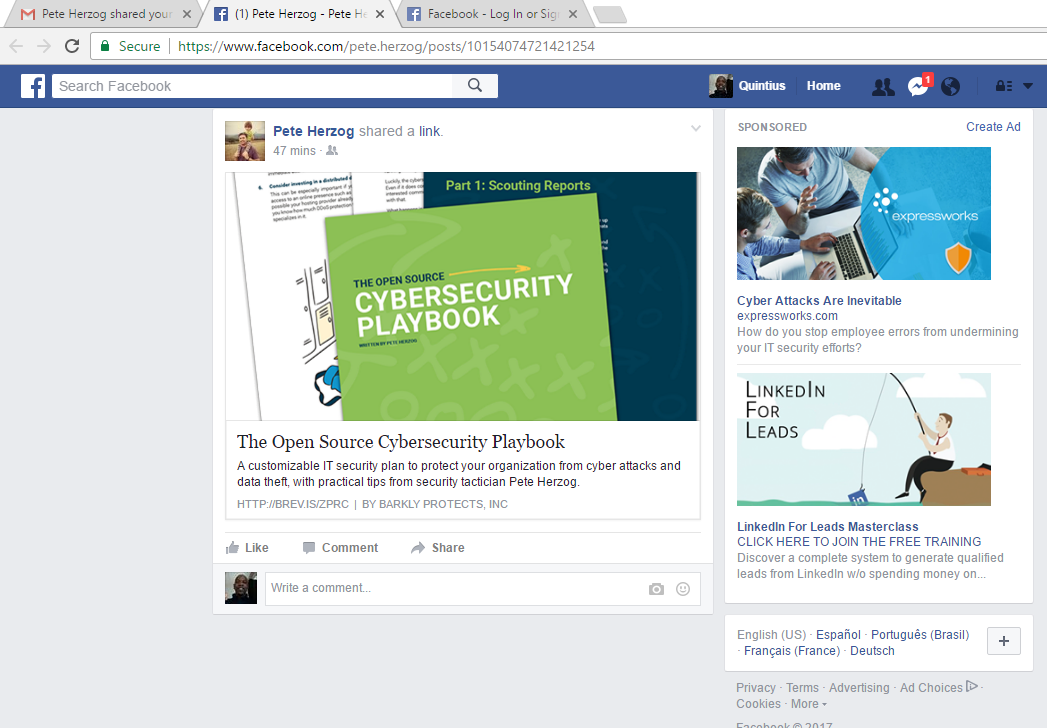
This is not suppose to happen! Being that it did happen I undoubtedly spent the next several hours searching, researching, and conducting as many test scenarios that I could think of to verify that I was not going crazy and that what happened sure enough, actually happened. (The series of test conducted will be included in the summary that was submitted to the folks whom you’d notify at Facebook if you think you may have stumbled up on something impactful.)
Me: Before I change the passwords on my account, let’s do this. I’m going to forward the same email to you and we’ll see what happens on your end when you click the “view” link. Thing is, how do we demonstrate to the world the mechanics of what’s going on here?
Pete: Not sure yet. I’ll think it over when I see it. You’re safe with me. Won’t pry into your stuff. Promise.
(end dialogue)
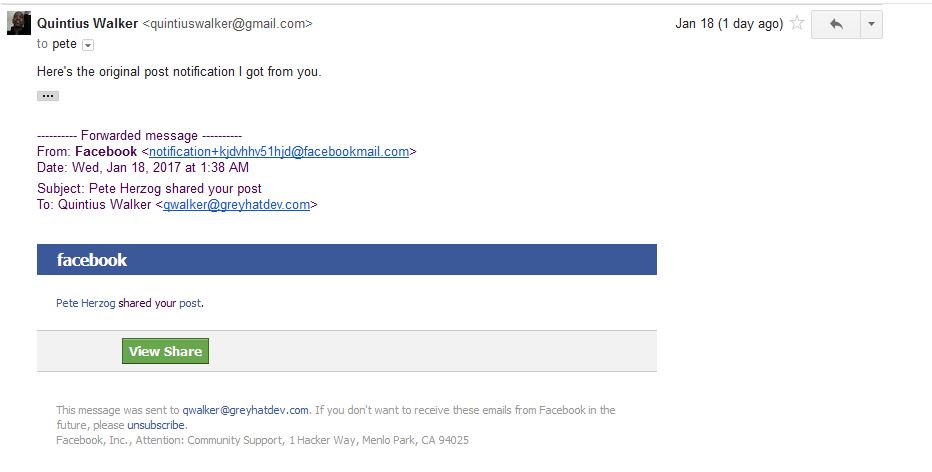
Well, given the title of the post it doesn’t take a rocket scientist to figure out what happened next. What happened next was, the attack that was only plausible in theory just became an exploit!
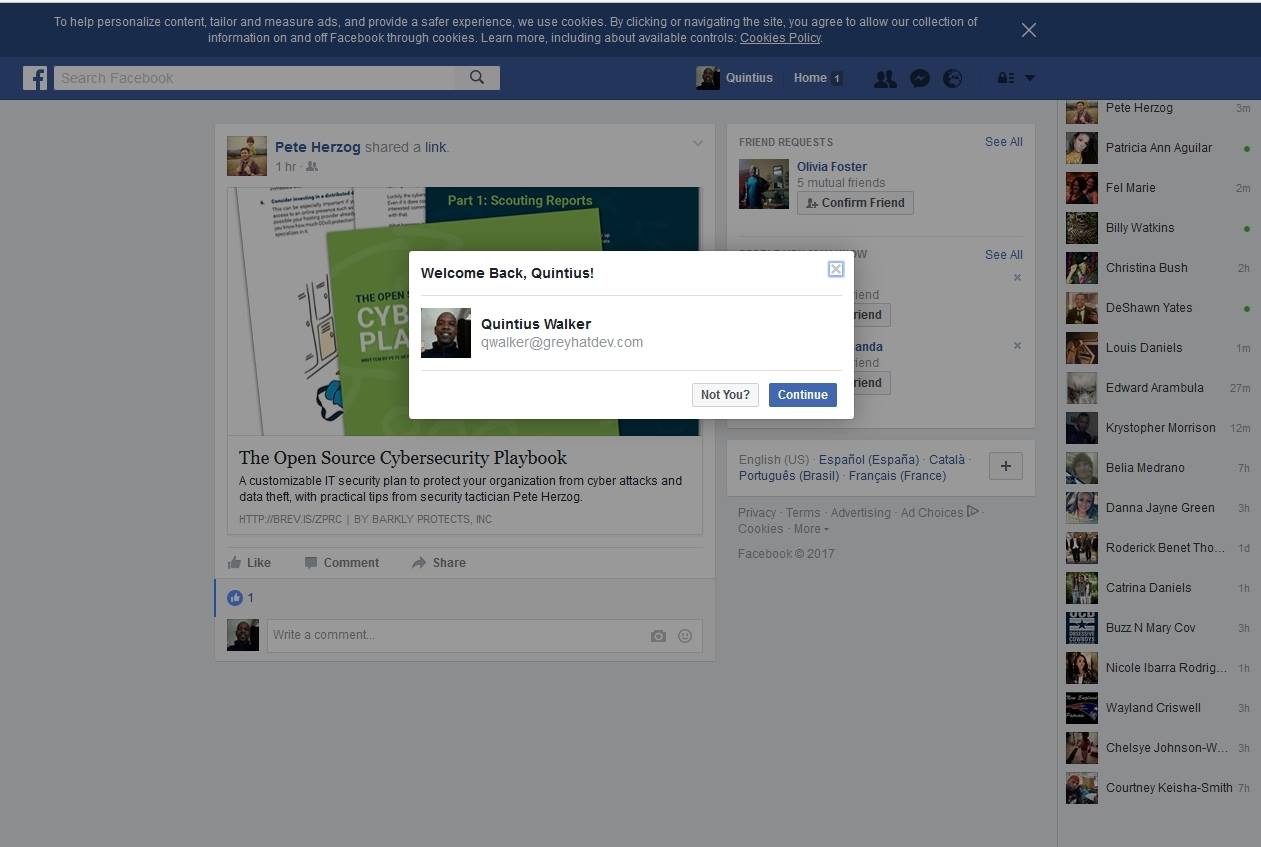
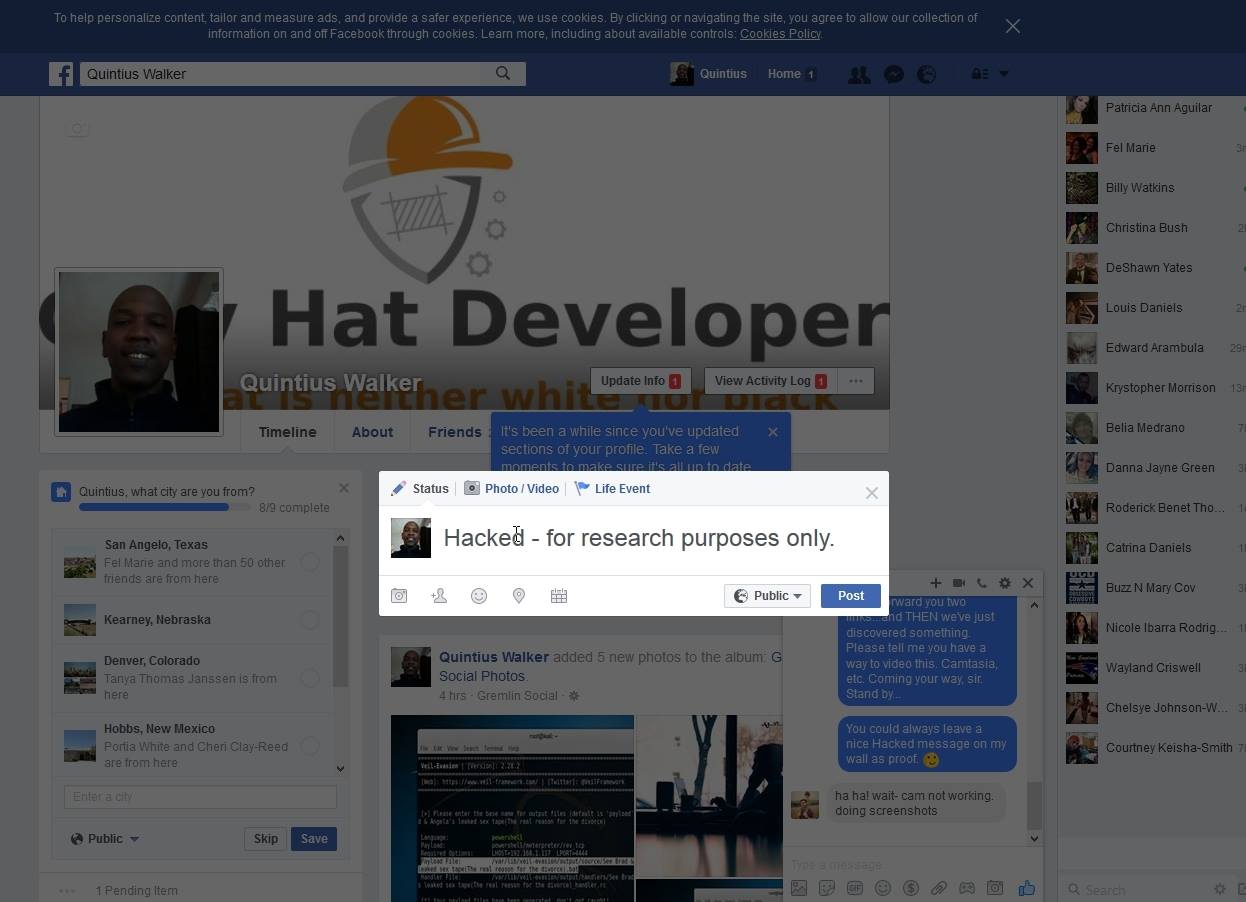

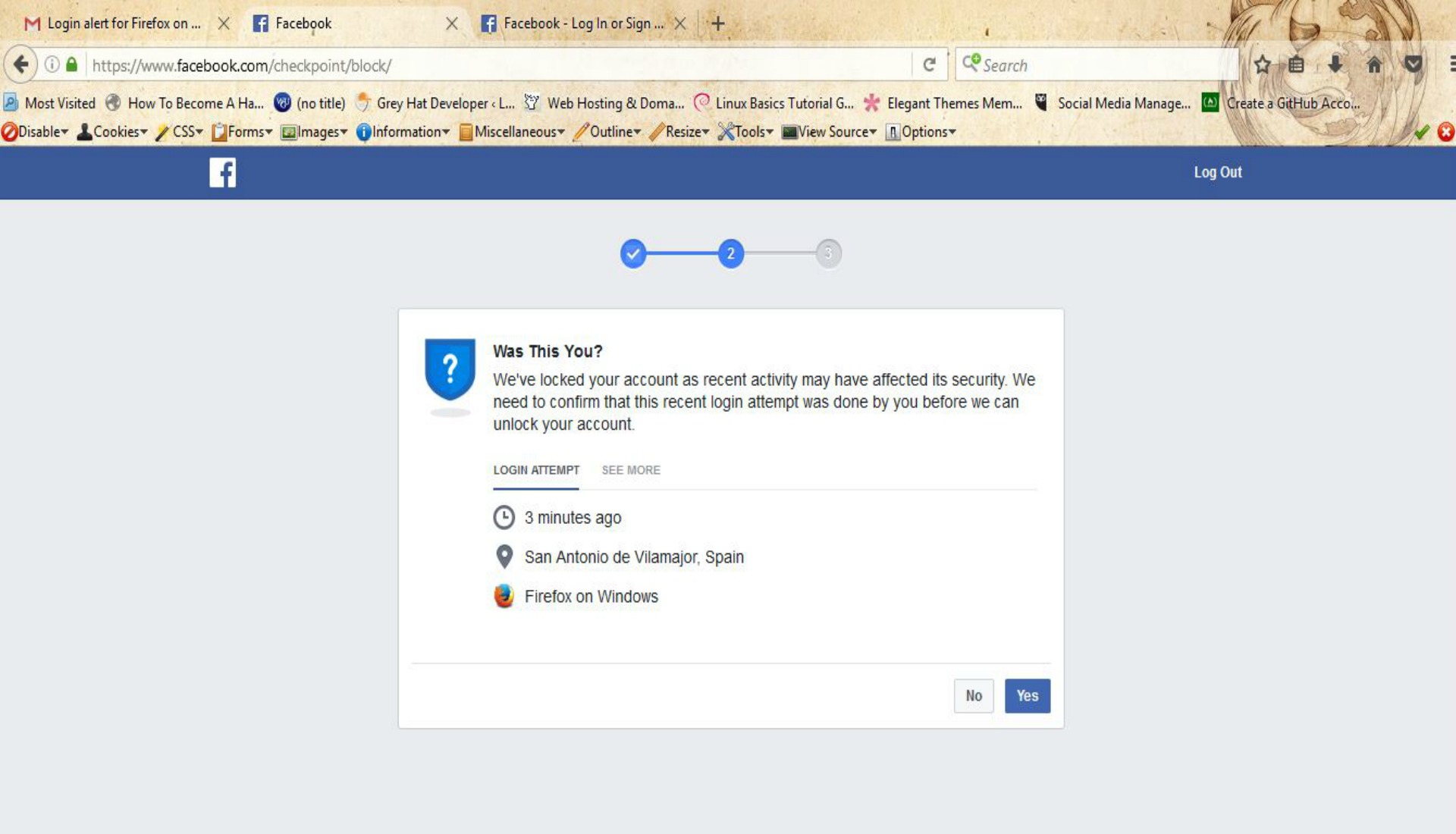
Just in case you’re reading this and thinking that all was due to some “feature” that I have enabled on my devices that logs me into my Facebook account automatically, you’re wrong. Clearly the above screenshots show that my friend was able to log into my account from Catalonia. I’m in the United States! True, the last screenshot shows that Facebook did indeed send me a “checkpoint” notification; however, what the screenshots doesn’t show is when the notification was sent. There were a chain of events that happened between the first email that I’d forwarded and he was successful to log into my account. Most notably is the fact that we even tried with an entirely different Facebook notification to ensure that there wasn’t something fishy going on with the initial link that deemed to allow the authentication. Interestingly, after I changed my Facebook password and tried to duplicate the events I wasn’t successful. Ironically, 24 hours later….it is still happening! Below is the summary of the report that was submitted to Facebook. (It’s worth noting that I wasn’t able to replicate the activity on mobile devices. At least not on any running Android. Didn’t have an Apple device to test with).
There is a flaw in the authentication check between Facebook notifications sent to one’s linked email account. For instance, if I have my Facebook notifications set to be sent to my email, although I may be logged into my email account at the time I receive and view the email message, if I am “nowhere” logged into my Facebook account on the same device that I am logged into my email account, and I click the “view message” option from within my email then I should be taken to my login page and forced to authenticate into my Facebook account before I can view or access the message….let alone…BE GRANTED ACCESS INTO MY ACCOUNT. (Granted, considering that I am not currently logged into my Facebook account anywhere on the same device nor browser).
The issue that I found is, when clicking the “View Share” button from within the email notification it not only took me to view the message but it also logged me into my account without any authentication checks.
Here’s what I find seriously flawed about that. I not only was able to access my Facebook account in the above manner but I was also able to access my Facebook account via a forwarded email of my Facebook notifications FROM my wife’s email account on…an entirely different device. Even if say, the first scenario should in some way be possible…there’s is entirely no way the second scenario should be possible unless I was logged into my Facebook account on her device within the same web browser. Now granted, this was not possible on any mobile device that I tried.
1. Log into email account (in this case it was my Gmail account, to where I had the address that is linked to my Facebook account forwarded to).
2. Click Social tab within Gmail to view Facebook notifications.
3. Click on the notification in question to open it.
4. Click on either “post” link or “View Share” button
5. I’m sent to the link AND successfully logged into my Facebook account without any authentication checks.
Reproductions Instructions:
1. Logged out of both Facebook and Gmail accounts
2. Cleared browser cache/cookies
(Repeated steps 1-5)
Same results.
Browser-Mozilla Firefox
OS- Windows 10 Ultimate
Next:
1. Logged out of both Facebook and Gmail.
2. Cleared browser cache/cookies
3. Closed Firefox.
4.Opened Google Chrome web browser.
5. Cleared cache/cookies
(Repeated steps 1- 5 above). Same result.
Next:
1. Logged into an entirely different computer and repeated all above steps.
Same result.
Next:
1. Forwarded the email notification to my wife’s email account.
2. Had her check her email on an entirely different computer than the two previous computers above
3. Repeated the initial steps 1-5 above.
(Result: From her email account she was able to authenticate into my Facebook account. Mind you, I did not receive any suspicious activity notices from Facebook when this authentication from her account/computer happened).
Next text:
1. Forwarded the same emails containing the notifications to a trusted friend who lives in another country.
2. Had friend repeat the initial steps 1-5.
Result: Friend in other country was able to successfully log into my Facebook account without any authentication checks.
Below is the response that I received from Facebook:
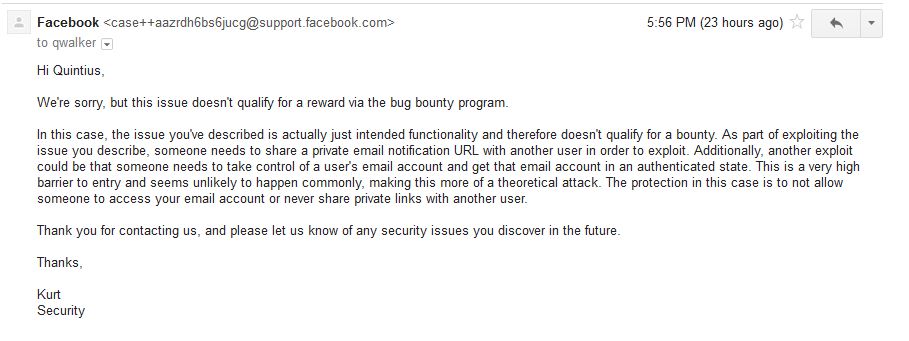
Well, then, according to Facebook this isn’t an issue in as much as it is an “intended functionality”. Unless I’m not understanding the response correctly, I take it to mean that by the email account being successfully authenticated, that in turn would indeed authenticate one’s Facebook account? Hmm. Yeah, I can see that being possible if Facebook had a “SIGN IN USING YOUR EMAIL ADDRESS” option. Maybe they do and I’m just not seeing it and blindly allowed that option somewhere in my account settings. (Albeit, usually that type of functionality is on the login page itself). Which would also mean that my wife and friend in another country whom I shared the link with would’ve had the same functionality enabled on thier Facebook accounts, right? But, wait- if that were the case wouldn’t that authenticate them into their own Facebook accounts when clicking on the notification to view the message? If I’m missing something here then by all means (clearly I am missing something), I beg you to PLEASE reach out to me and explain what functionality that I have enabled on my account so that I can promptly disallow such a function. In the meantime, for those of us that are not comfortable with the thought of this theoretical attack being exploited we’ll just not allow notifications to be sent to our email accounts.
I hope this has been informative to you and I like to thank you for viewing this post. Subscribe or follow me on Twitter. Until next time, Hack On, gents!