Fuzzing with Ffuf- Part 2
100 Days of Hacking
We’ve been given an online academy’s IP address without any further information about the site. Thus, this is essentially a black box scenario. As normal and always, our first step is to locate all pages and domains linked to the IP to perform a proper enumeration.
We are to fuzz the pages that we identify during enumeration searching for any parameters that can be interacted with; if any active parameters are found, we must try and retrieve any data from them.
Attacking Web Applications with FFuf – Part 2
Day 36 – 37
Web Fuzzing Assessment
Run a sub-domain/vhost fuzzing scan on ‘*.academy.htb’ for the IP shown above. What are all the sub-domains you can identify? (Only write the sub-domain name)
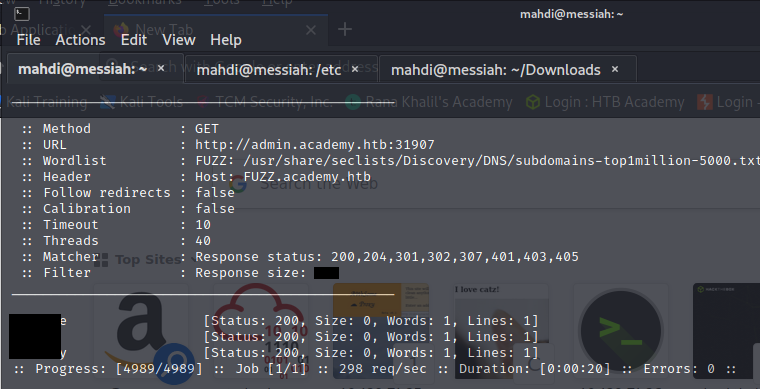
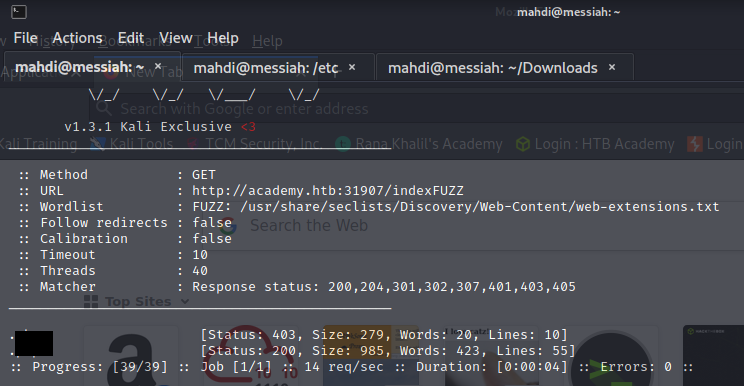
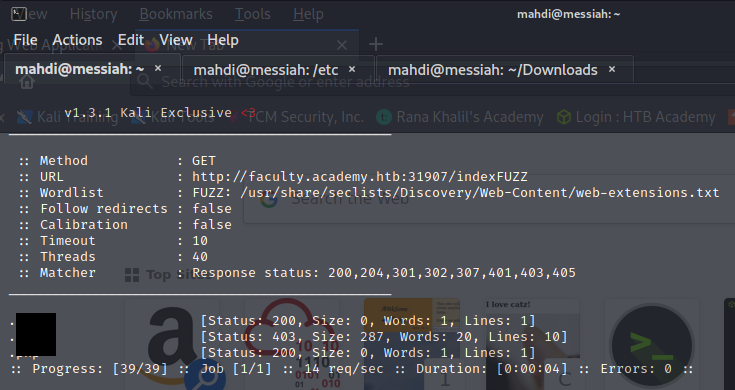
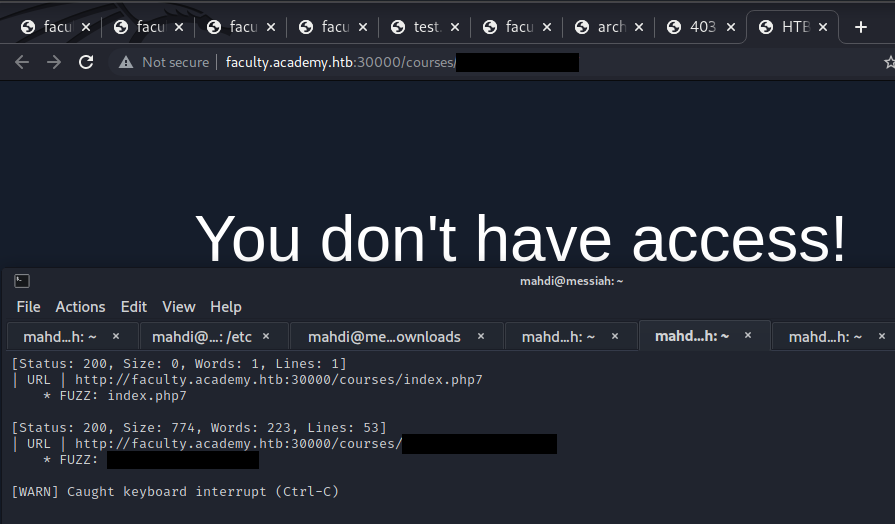
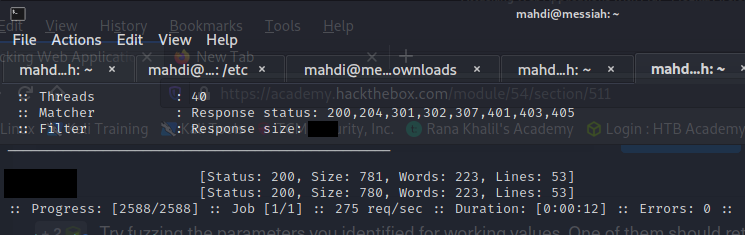
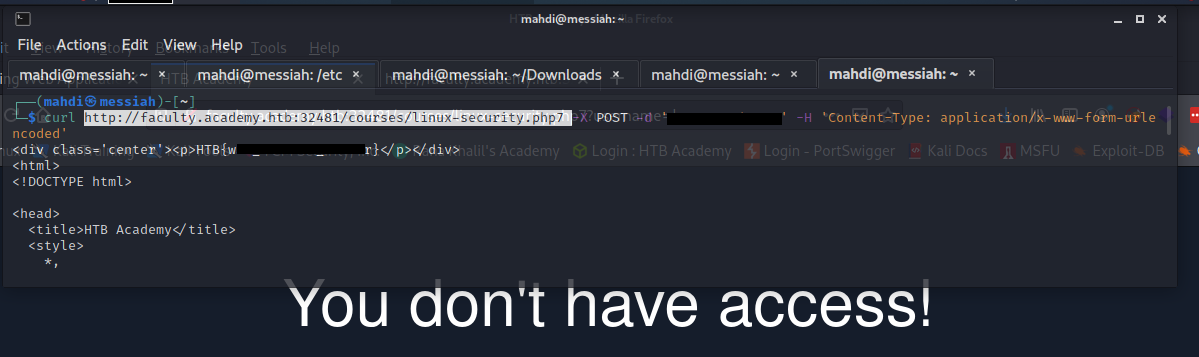
Our assessment was a success. By tackling it we familiarized ourselves with enumerating web applications for hidden pages, directories, and parameters and fuzzing parameter values.
I hope this article has served as a source of enligtenment as opposed to a source of confusion. If there’s something you’d like a bit more insight into and think I may be of some help, please don’t hesitate to reach out.
As always, thanks for reading. Hack On, Ladz & Gentz!


