About Grey Hat Developer
When we polled people of a certain demographic, we asked them why they were not taking advantage of free and open resources to educate themselves in the rapidly growing field of IT/Cyber-Security? The response we heard most was that the time needed to train until actually gaining employment is too long and too expensive.
Grey Hat Developer is an organization that provides Free IT/Cyber-security training to ex-felons, adult learners, minorities, and disadvantaged youth. Our mission is simple: To help as many people who feel that they are trapped but who possess the desire and willingness to change, be open to the idea that change can be fostered through learning IT/Cybrary security skills.
We Are An Organization That Trains, Certifies, and Employs.
We Help Clients Get Trained, Get Certified, and Get Working. Its Simple.
How We Got Started
At home in Texas, we noticed a trend. Initially, we noticed that there’s a lot of people with a blemished past who have reformed, rehabilitated, and out of either sheer drive to become their own bosses or being forced to start their own companies due to society not giving them the opportunity to advance themselves beyond positions that pay very low wages (or jobs that may pay high wages but are very labor intensive and require them to spend more time away from their families), these people have managed to start reasonably successful businesses for themselves. The constant variable that we noticed among this demographic was their failure to properly implement the use of IT/Information Systems. These entrepreneurs were lacking something that every business needs to remain competitive, evolve, and remain successful.
We also noticed there was a huge desire among not only convicted felons, but also among minorities (i.e., Blacks, Latinos, etc.) to learn and secure employment in the IT/Cyber-Security fields.
It didn’t take long to consider that this trend is not unique to the Southern state, but also applies to individuals in similar situations across the United States, if not globally. We set out with the vision to bridge the gap between these two demographics. We arm the second group with the knowledge and skills necessary to be employed by the first group. Everybody Wins!
Answers to Your Questions
What is Grey Hat Developer?
Grey Hat Developer is a company that offers managed IT services. We also offer IT and Cyber-Security training to those who request us to provide it.
Isn’t “Grey Hat” a hacker term?
Yes, that is correct. While we do embrace the spirit of such term in the sense that we believe that hacking isn’t good nor evil, that isn’t what Grey Hat Developer is about. We see IT and Cyber-Security skills as a viable path for someone to forge a very promising future for themselves. Unfortunately one mishap in someone’s past could derail that person from ever having a career as a White Hat Hacker. But that doesn’t mean that person should turn to the allure of becoming a Black Hat Hacker. So that’s where that grey area has become a part of our philosophy. We have witnessed Cyber-Security completely change a person’s life around. That fueled us with inspiration and Grey Hat Developer was born.
Will you teach my child to hack?
No. Your child already knows how to hack. 🙂
How do I sign up for training and what do I need?
Signing up is simple. Just contact us and let us know that you’re interested. One of our reps will guide you through the on-boarding process. In most cases, all you’ll need is a solid internet connection, a compatible device, the patience of Job, and the desire to learn.
Are your services expensive, there aren’t any rates listed on any of your products or services?
As mentioned, we understand that everyone’s budget and requirements are unique. At this time there are no “fixed” prices on any of our services. We aim to get a feel for your project as a whole before we throw any numbers in your face. Contact us for a quote on your next project or idea.
Blog / Latest News
Scanning and Enumerating: Secrets Bleed Like Blood
It is widely held that the Romans successfully built their own novice navy into a formidable fighting force after capturing and "reverse-engineering" a Carthaginian warship that had run aground. This would be not only yet another example of how "chance favors the...
Cutting-At-The-Edges: Exploiting Human Weaknesses
Bleeding my enemy is the next greatest joy to burying him I'm sure a lot of us are familiar with Miyamoto Musashi- the Buddhist, the Samurai, the artist, the writer. Yes, no, maybe so? Well, to some he's become known as the greatest swordsman to ever live. With over...
Reconnaissance: The Streets Is Watching
As a hacker, intelligence will be the bread and butter of your power Before I ever even considered pursuing a career in penetration testing, I use to snuggle up in bed breathlessly reading The Art of War by Sun Tzu, just wondering how it was going to end. Yes, I took...
A Hacker’s Top 10 Rules For Success
A hacker is not so much an entity, a being, a title as it is a mentality. Most people are familiar with Tupac the rapper/actor. But I wonder how many people ever looked at him as being a hacker? That's right. Tupac was indeed a hacker. Evan Carmichael carved out...
What’s a handle all about?
@The_StarHack3r Lesson 1: Being a Hacker - Choose a handle for yourself In Lesson 1: Being a Hacker there's a section that talks about handles and the different reasons that hackers use them. In sum, hackers use them: For fun (<-- this mostly applied to hackers in...
Hacking Kung-Fu: Aims and Objectives- Part 2
“ Test your systems with fire and ice, sand and sea, bile and blood....before your attackers do! ” In this post we're going to wrap up the Hacking Kung-Fu series. We're still digging in and focusing on aims and objectives so this will be a bit lengthy. Thus, without...
The Generals 6 Movers of Hackers
A long time ago there was this guy who, some claim to be one of the greatest generals of all time. Of course, we've seen a lot of great generals which leaves this claim up for much debate. However, that debate is not what we're going to tackle here. Instead, what I am...
The Three Requirements For Attainment
The Three Requirements for Attainment Part 2 of Hacking-Kung Fu: Its Aims and Objectives There are countless reasons why students fail to achieve their objectives in their Kung Fu-Hacking training, but to help us understand the factors that contribute to...
Hacking-Kung Fu: Its Aims and its Objectives
Part One In this post I will be using the term “ Hacking-Kung Fu ” to point out the similarities that exist between hacking and Kung Fu. Thus, when you see the words hacking or Kung Fu, realize that I'm intending to use these two words interchangeably. Getting Better...
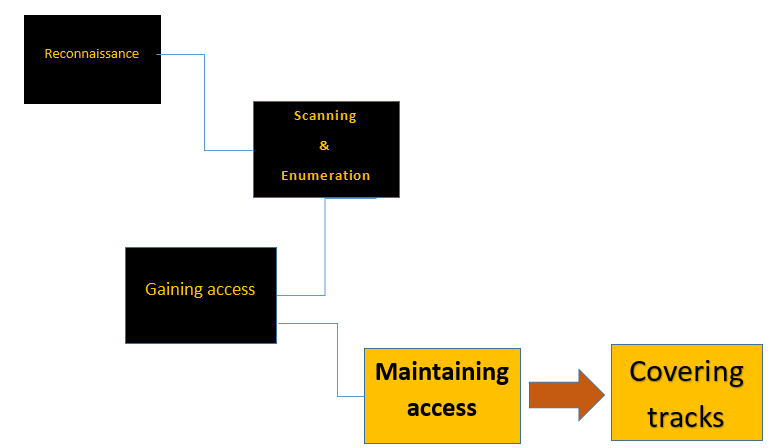
The 5 phases of a standard hack
Before we go further into any more of the technical aspects of hacking, I want to point out that normally, hacking is a process. This remains true for the individual hacker as well as for the collective hacker group. The majority of people I meet, before being...
Get In Contact With Us
Office
704 W. 15th Street
San Angelo, Tx. 76903
Hours
M-F: 8am - 10pm
Sat. 10am - 3pm
S: Closed
Call Us
(432)212-8959