Quintius Walker, Grey Hat Developer, Cybersecurity Consultant
28 June 2024
Photo by Jakob Owens on Unsplash
Absolutely everything on this blog pertaining to the term “hacking” is meant for training and educational purposes only. WE DO NOT ENGAGE IN NOR PROMOTE ANY ILLEGAL HACKING ACTIVITY!
I get asked a lot about what I did before Ethical Hacking and Cybersecurity.
It was during a career change from the down South Texas music industry, that I discovered the rewarding and exhilarating field of Information Security.
Back in those days we produced real country rap tunes.
This was during an era when rap was still what Gen Xer’s are ranting about today, “good music before these youngsters touched it“. ![]()
How To Hack A Rapper…or anyone else for that matter.
I remember learning about Reconnaissance when I first got into the field.
The Information Gathering stage is generally understood to be the beginning phase of all penetration testing methodologies.
I would vividly imagine ways to apply my new found Recon skills to my former industry.
You may not believe it but in those days it took a lot of creativity to patch the vulns that were being discovered in Hip-Hop. Unfortunately that’s not the case these days.
But like, what earthly benefit would an ethical hacker be to a rapper?
So I’d sit by practicing passive Recon. My epic discoveries amounting to naught by themselves but when… paired with circumstance, could very well be hell to tell the captain.
“Peace, God”
Allow me to salute you,
You’z a vet,
But dudes
be out here slipping
When they’re tripping
on this net.
Posting pictures,
Flics and videos
But you can bet…
Ain’t nothing
they can do
once they confuse
‘um with the threat.
Let’s walk through a hypothetical scenario.
I want you to imagine that the rapper Mysonne The General has been the targeted by a group of Hacktivist who are opposed to the causes that The General stands up for.
Multiple accounts of The General have been compromised.
His team is working dilegently to pinpoint how a breach of this magnitude occurred.
They’re especially concerned because the breach is widespread across many platforms.
They’ve requested you to investigate the incident.
Two months earlier. Somewhere on the other side of the planet
“My friend, it is a relatively simple thing to do, to obtain the email address of the rapper. Do you not have Instagram?”, says Vlad to Sergio.
“To get email address of rapper, on Instagram, you just need follow the account.”
Sergio replies, “No es posible, chico. El rapper would have to follow me tambien.
Ademas, no vale you have email, entonces que? No can do nada. Es email no mas.”
Well, it turns out that Vlad es correcto en ese scenario Sergio.
If ever you’re in search of the email address linked to your target’s verified Instagram account, an easy way to get it is to follow the account.
Yes. It is absolutely that simple.
And as we know, in the Era of the Influencer, a brand’s social media account is equivalent to a Threat Actor’s C2 center.
But back to Sergio’s response.
You have the email address. Big Deal, you say.
Well, a Threat Actor having an active email address of it’s target, kind of IS a Big Deal.
Think of it as what’s referred to in the office as Business Email Compromise. Yeah, it’s kind of a big deal. ![]()
Let’s look at Step One:

But do
we listen?
We upload shows
and we forget,
that to a cyber-criminal
we’re nothing but a lic.
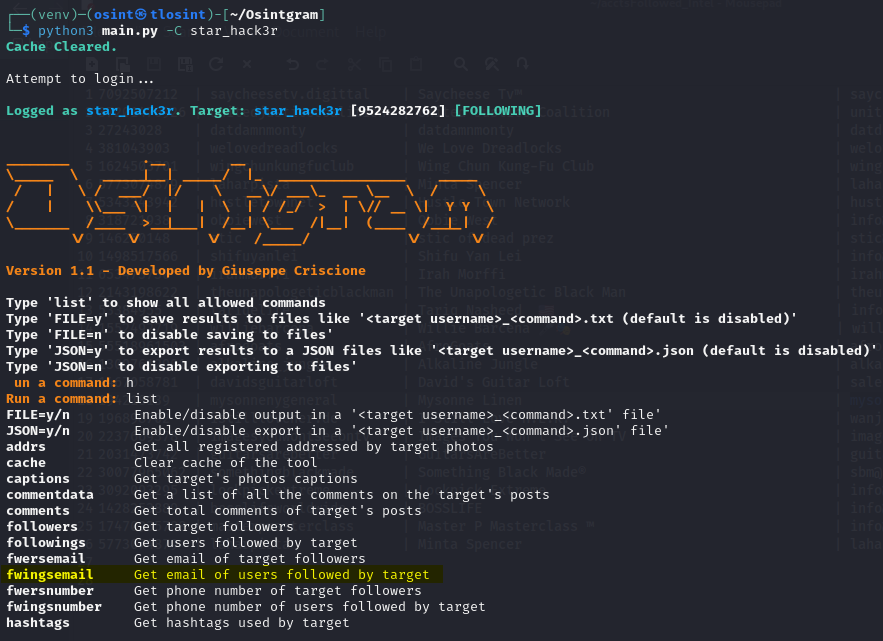
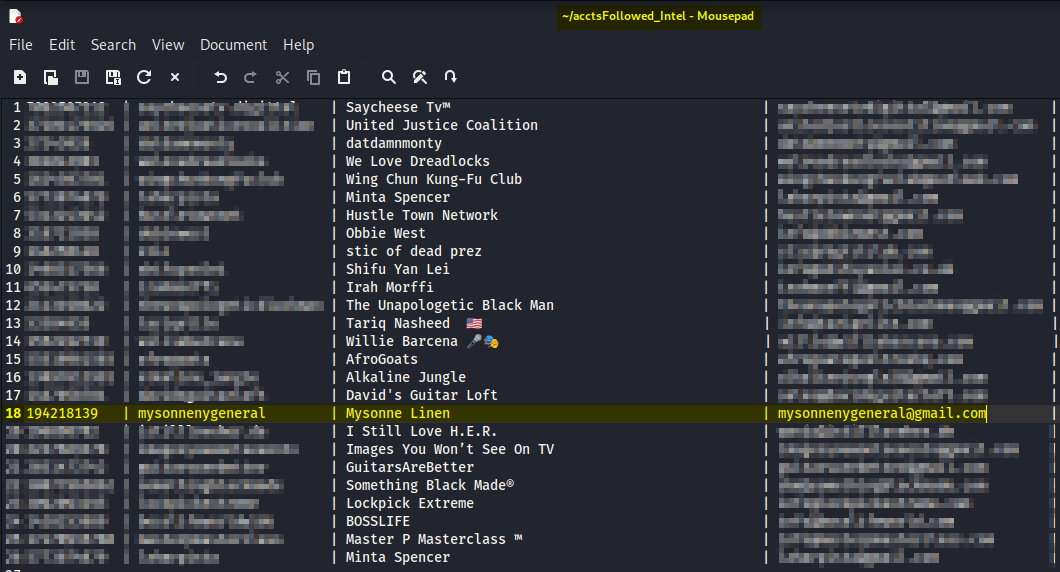
In the above screenshot, I used an OSINT for Instagram tool called OSINTgram which, among other things, fetches the email addresses of accounts that I follow.
So if a Threat Actor wanted The General’s email, they’d only need to download the tool, follow his account, then run the tool.
Again, objectively, in light of it all there’s still no vulnerability nor threat.
However, one of the most fundamental checks that Vlad and Sergio can do now is check the email address against a tool like Have I Been Pwned for any recent breaches and leaks to the internet.
Like in the following screenshot. Step Two:

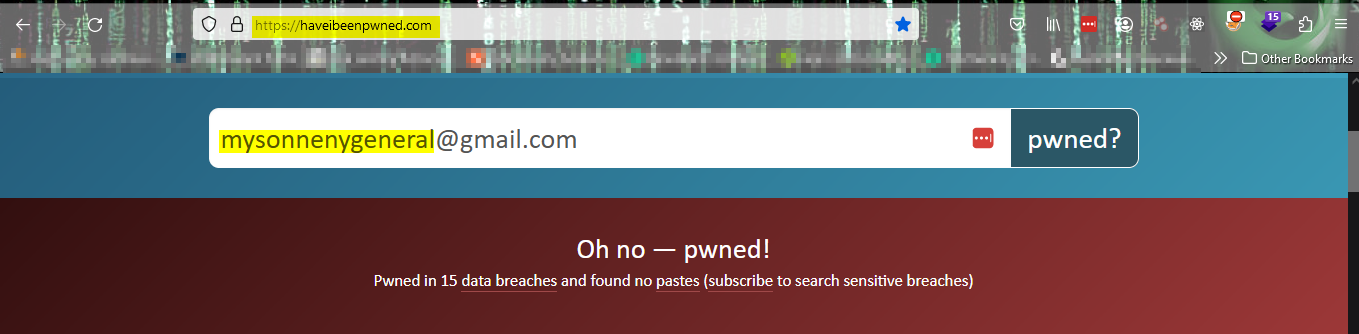
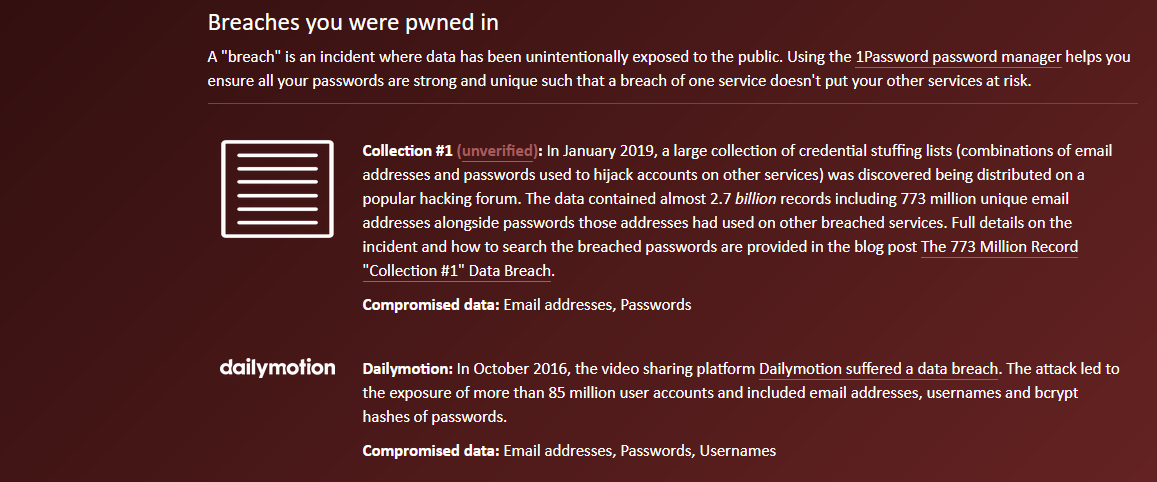

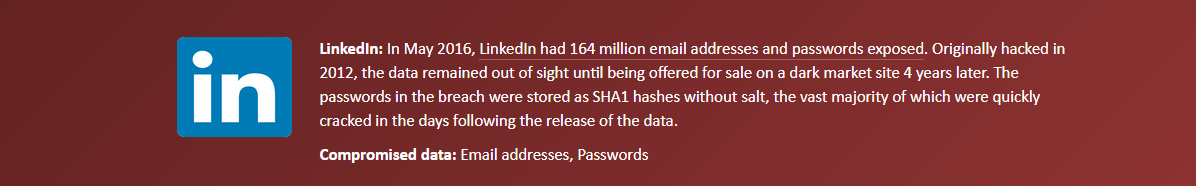
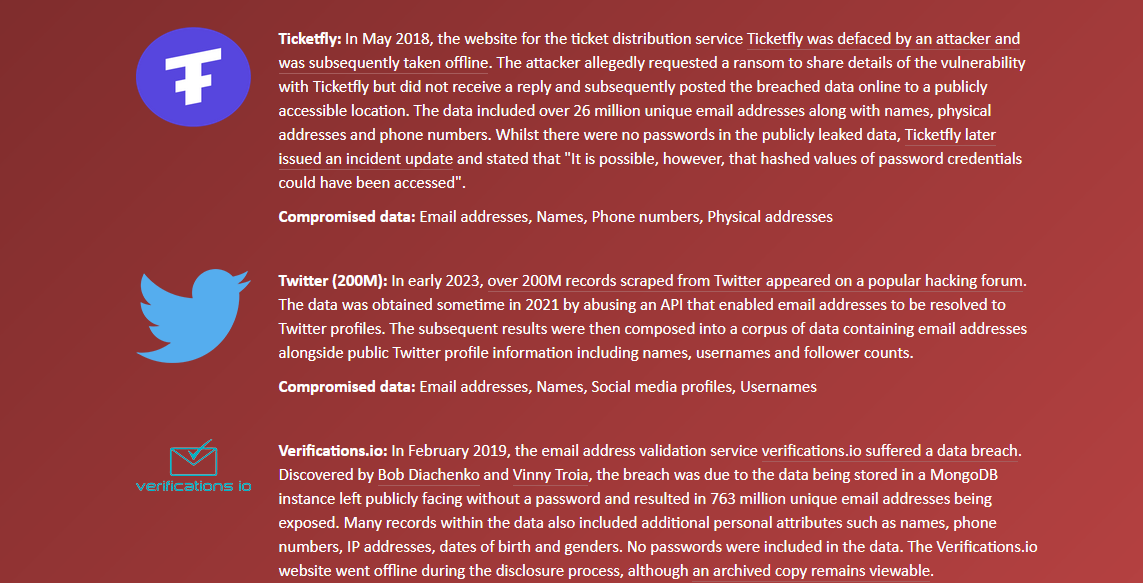
As you can see, The General’s email has been involved in quite a few breaches. Some of which are breaches that happened on big named platforms like LinkedIn and Twitter.
Again, just knowing this much alone doesn’t seem alarming.
But I think that what a lot of people fail to consider is the next step the Threat Actor can take.
Vlad and Sergio can also plug the email address into a service that hosts databases of breached data.
Often, access to this data can be obtained on the internet for fees as low as only $5.
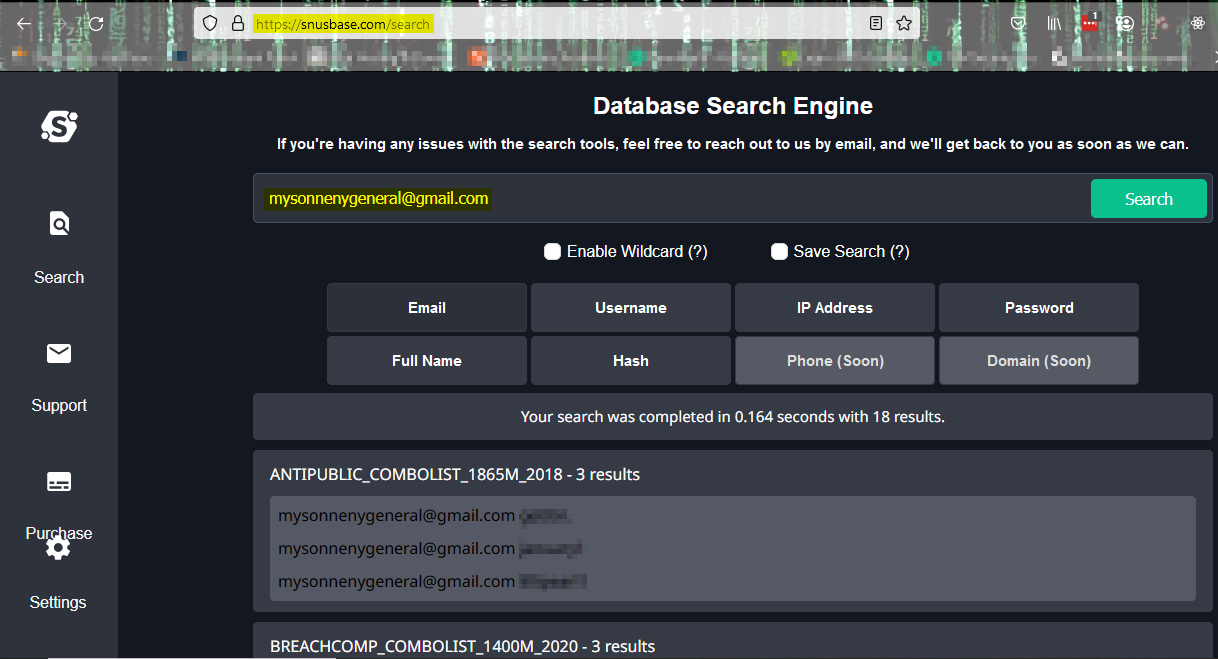
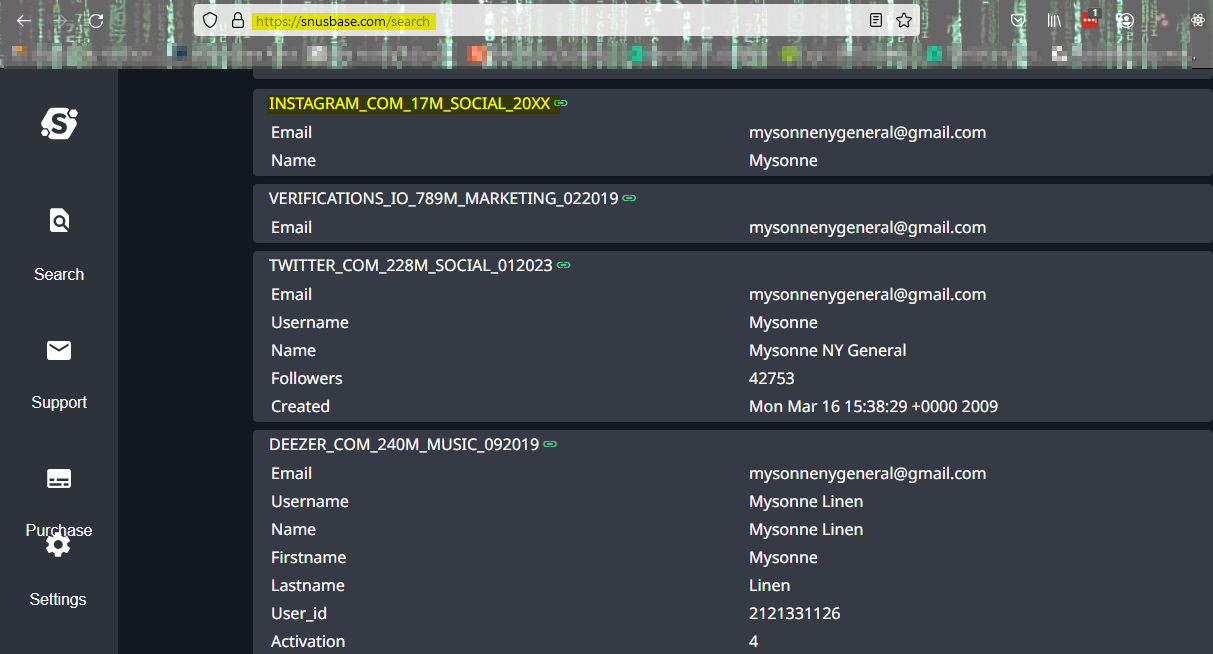
After taking the additional step to access the credentials, the Threat Actors can launch password attacks against The General’s accounts.
It’s just
another dollar
you holler
but where I set,
I’m just
trying to lace you
I don’t mean no disrespect.
Groupies want your autographs,
while they’re asking you for sex….
Au contraire,
Hackers want your email address.
There’s a lot to be noted here.
First, although the data involved in this example is authentic, the scenario is hypothetical.
However, I do follow Mysonne The General on Instagram and thus, used his account as an example.
But the key takeaway in the example is that none of this is exclusive to just Mysonne The General. Hence…. the “or anyone else for that matter” in the subtitle.
This was written with the person in mind who isn’t familiar with tactics and techniques routinely used by Threat Actors.
In fact, the reader can now use these steps on themselves or someone else as a Proof-Of-Concept.
Total transparency here. Before writing this I performed these steps on some of my accounts and needless to say, those accounts came back in the red. They’d all been involved in breaches.
Something else to be acknowledged is that the target in the example didn’t do anything wrong.
The issue lay with the platforms who’ve suffered from a data breach.
It’s worth pointing out that there’s an additional step required in order for there to be an issue, that would be- “using those credentials from the dump to log into an account unauthorized“.
A BIG Word of caution here. Should you decide to follow along with the steps in this article, DO NOT attempt to log into any account without express consent from the owner of the account!
That is an unethical act that will place you at risk of being criminally charged.
In a future post we’ll look at helping the client minimize damages and ensure they’re immune to this type of low-hanging fruit attack in the future.
Hack On, Ladz & Gentz!
Thank you very much for reading.
Subscribe for future posts and by all means Share this article with anyone who’d benefit from knowing what was covered.
Here’s some key sources mentioned in the article:


