Javascript: Don’t Hate, Deobfuscate
6
August, 2022
Days 38 – 40
Javascript: Don’t Hate, Deobfuscate
100 Days of Hacking
Photo creds goes ->> @felix_mittermeier
It’s been my observance that if one’s a coder they either love Javascript or absolutely hate Javascript.
If the former, chances are you’re probably this super dope web dev that can make web apps do well, practically anything given the idea.
If you’re getting into web app security testing or bug hunting, I may sound like a broken record but trust me, Javascript chops will aid you greatly. So don’t hate, deobfuscate.
We are still grinding along HTB’s Bug Bounty Job Role Path, https://academy.hackthebox.com/course/preview/javascript-deobfuscation.
In summary-
- Deobfuscate code and analyze its main function
- HTTP requests and replicating the main function of obfuscated JavaScript code.
- Methods to encode and decode strings
Javascript: Don’t Hate, Deobfuscate
Day 38 – 40
Javascript Deobfuscation
Using what you learned in this section, try to deobfuscate ‘secret.js‘ to get the content of the flag. What is the flag?
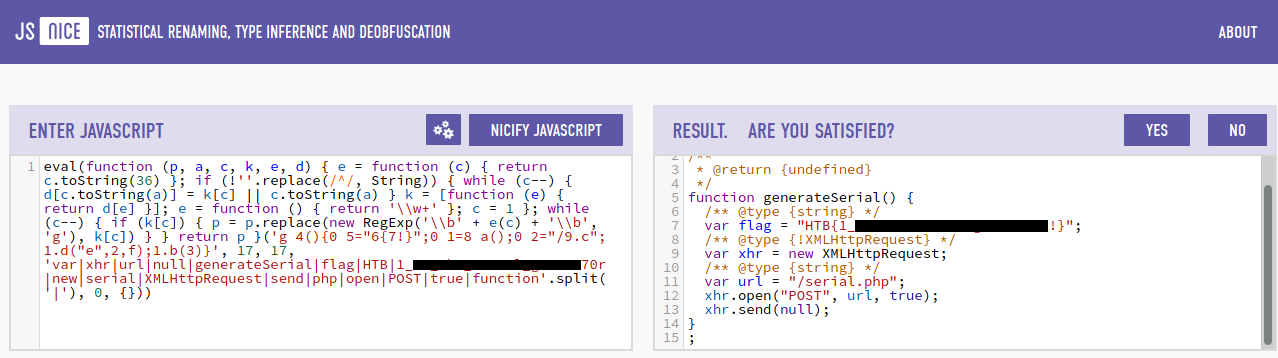
HTTP Request & Decoding
Using what you learned in this section, determine the type of encoding used in the string you got at previous exercise, and decode it. To get the flag, you can send a ‘POST‘ request to ‘serial.php‘, and set the data as “serial=YOUR_DECODED_OUTPUT“.
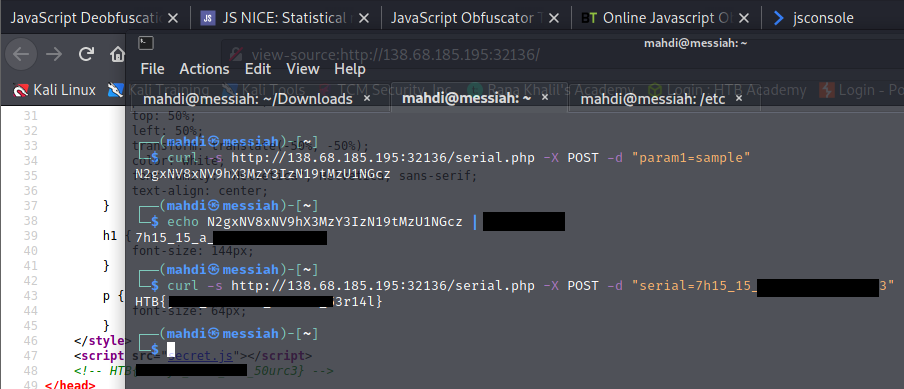
Skills Assessment
There was a pen test that discovered JavaScript and APIs on a web server. The job was to determine their functionality to understand how it could negatively affect a customer.
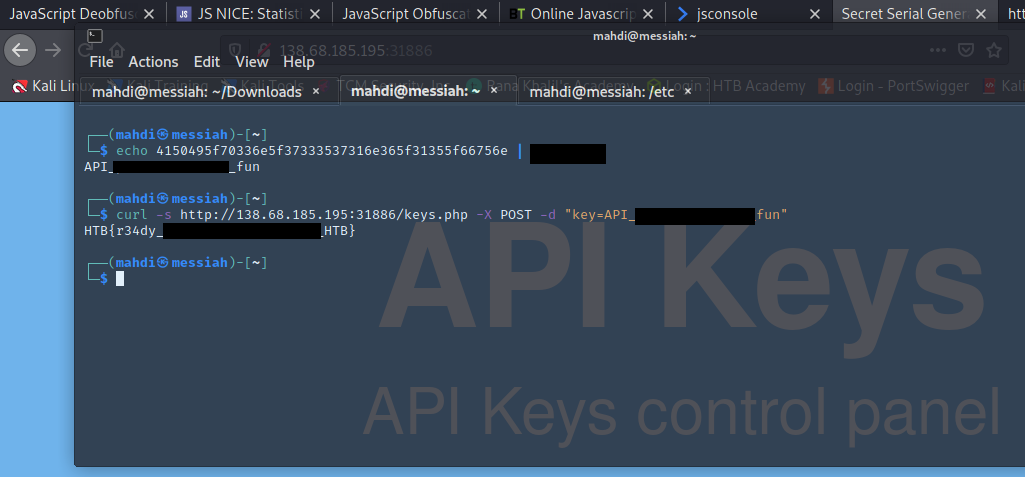
Once you have the secret key, try to decide it’s encoding method, and decode it. Then send a ‘POST‘ request to the same previous page with the decoded key as “key=DECODED_KEY“. What is the flag you got?
Our assessment was a success. By tackling it we familiarized ourselves with deobfuscating code and analyzing its main function, HTTP requests and replicating the main function of obfuscated JavaScript code, and discovering methods to encode and decode strings.
I hope this article has served as a source of enlightenment as opposed to a source of confusion. If there’s something you’d like a bit more insight into and think I may be of some help, please don’t hesitate to reach out.
As always, thanks for reading. Hack On, Ladz & Gentz!


